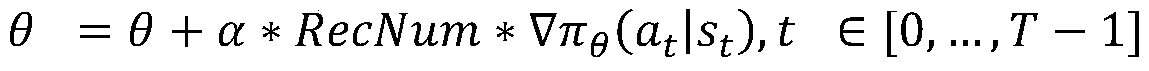Intelligent general evaluation method and system for vulnerability of recommendation system
A recommendation system and vulnerability technology, applied in the information field, can solve the problems of high recommendation system, high cost, and a lot of manpower and material support, and achieve the effect of guiding design, accurate evaluation, and low labor cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
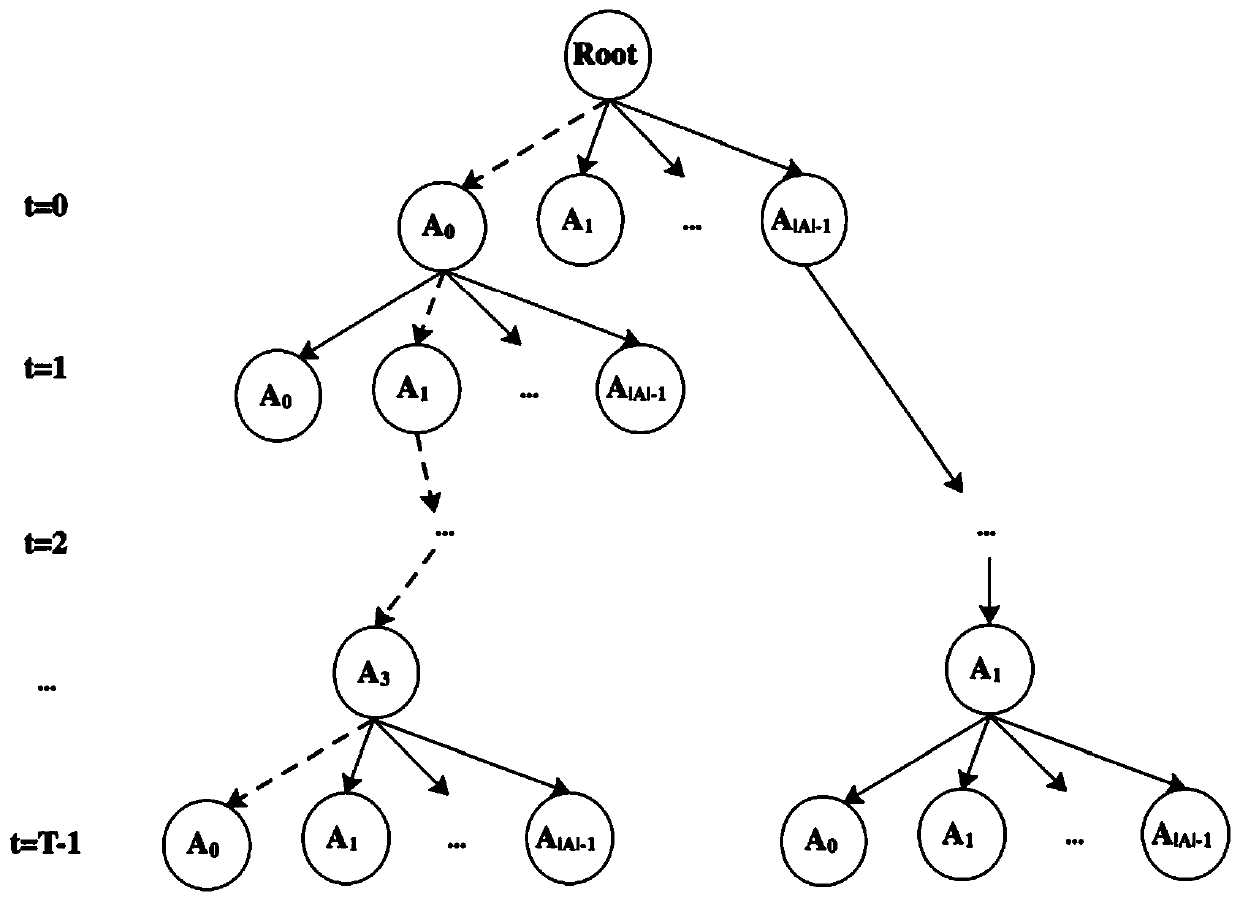
[0037] Based on the e-commerce recommendation platform, the following is a more specific introduction to the vulnerability detection method of the adaptive recommendation system proposed by the present invention, including some background knowledge during algorithm design, and the specific process of reinforcement learning algorithm training.
[0038]First, we assume that there is an attacker, and describe the scope and target of the attacker's operation authority on the recommendation system in real situations.
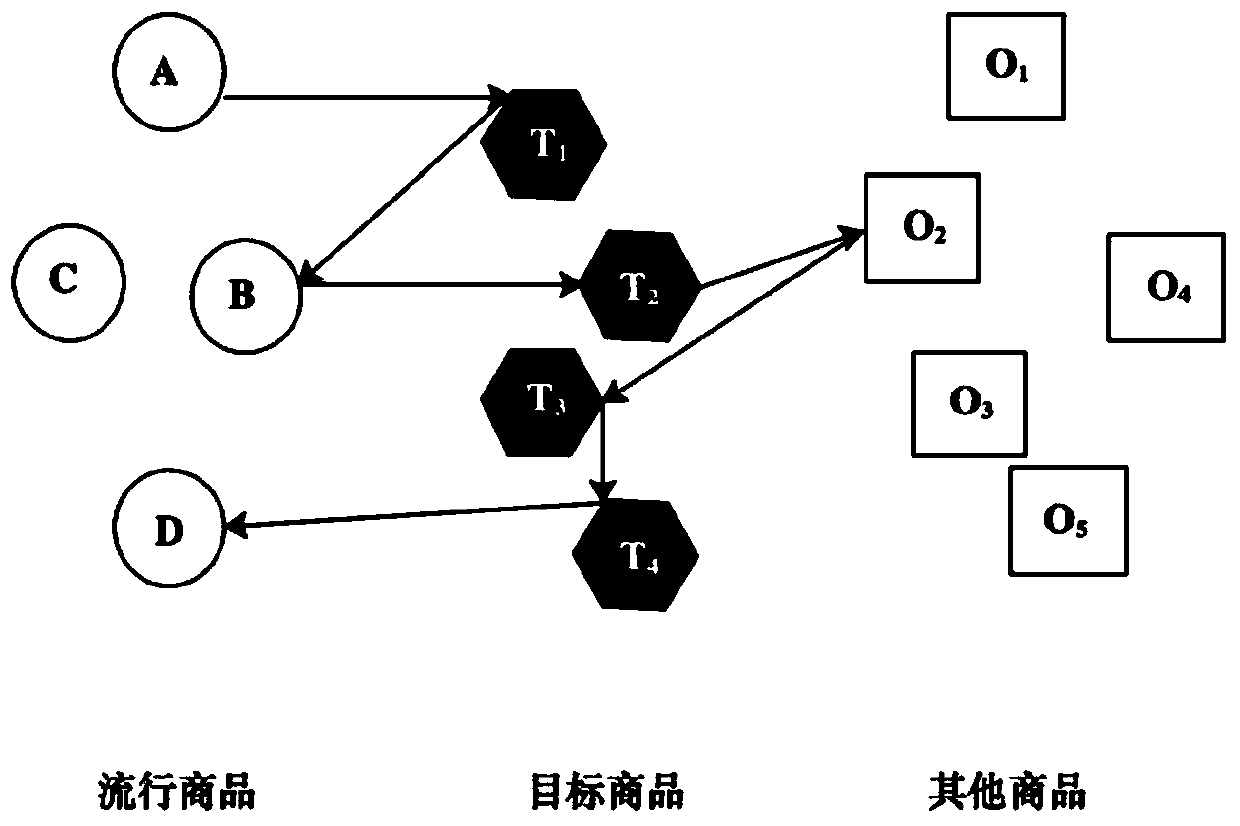
[0039] 1. Due to the privacy of the recommendation system itself, the attacker cannot know: (1) which recommendation algorithms are specifically used by the recommendation system and what steps are in the recommendation process; (2) the operation log information of other users. The attacker only knows the basic product information and the roughly estimated product popularity information through multiple interactions with the system.
[0040] 2. The attacker's attack ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com