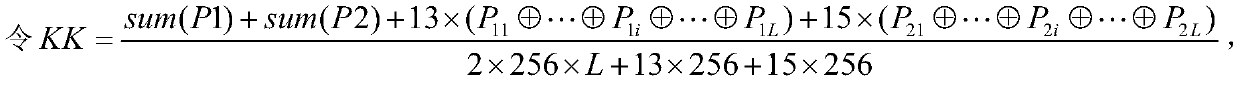Chinese character-to-picture encryption method
An encryption method and technology for Chinese characters, which are applied in the fields of digital data protection, electrical digital data processing, instruments, etc., can solve the problems of few Chinese character encryption algorithms, large amount of information, poor readability and reproducibility of ciphertext, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
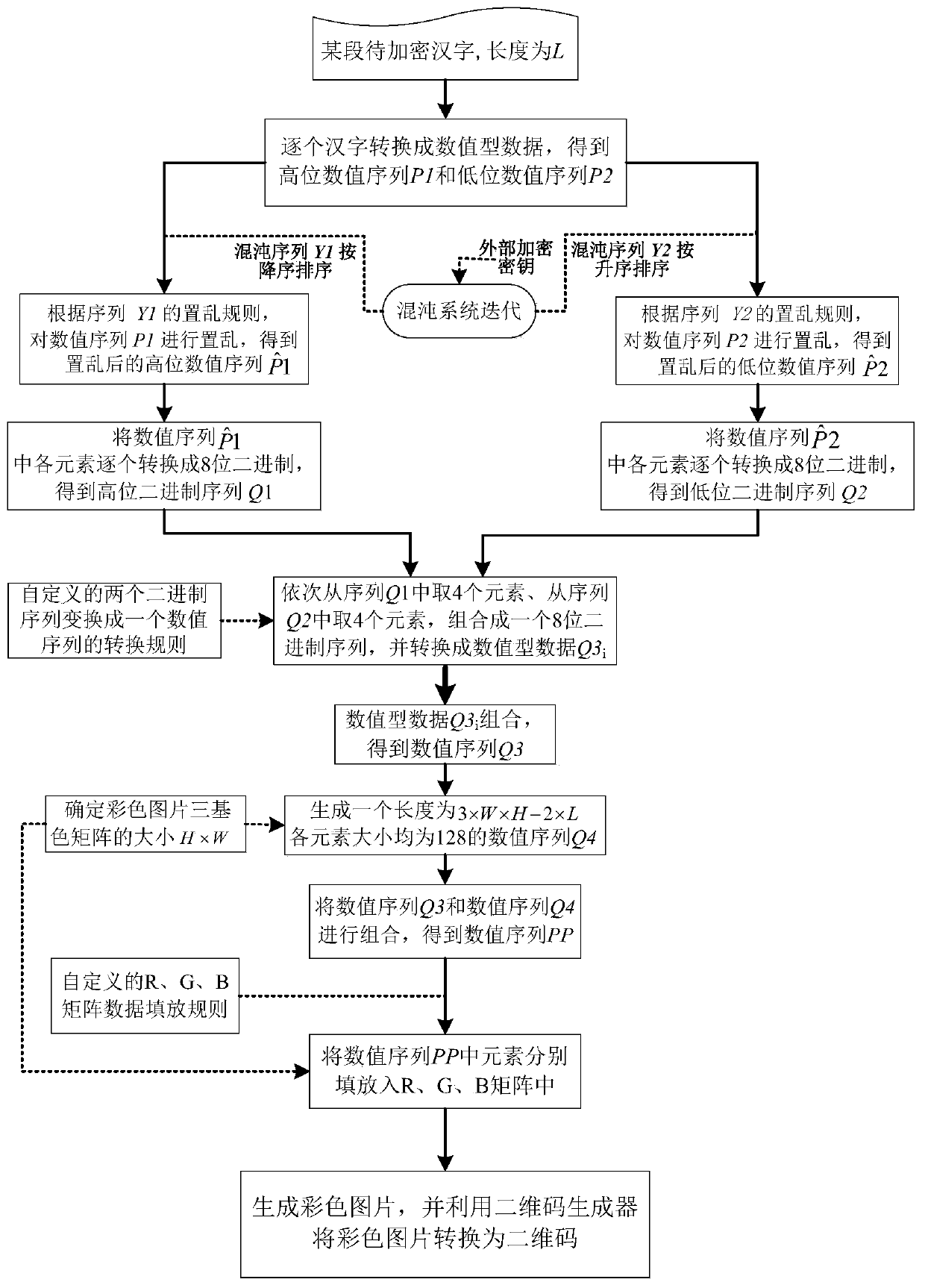
[0069] According to the encryption method of a kind of Chinese character conversion picture in the above-mentioned specific embodiment, the steps are as follows:
[0070](1) Taking a certain Chinese character as "an encryption method for converting Chinese characters to pictures is a relatively simple and feasible method. Pictures refer to flat media composed of graphics, images, etc. There are many formats of pictures, but generally they can be It is divided into two categories: bitmap and vector diagram. The characteristic of chaos is that the orderly motion form that originally followed simple physical laws suddenly deviates from the expected regularity under certain conditions and becomes a disordered form. Chaos refers to Deterministic dynamical system is unpredictable and similar to random motion due to its sensitivity to the initial value. It is also called chaos. The English word comes from Greek, and the original meaning is the scene before the beginning of the univers...
Embodiment 2
[0086] According to the above-mentioned encryption method for converting Chinese characters to pictures, a certain section of Chinese characters to be encrypted is still: "A kind of encryption method for converting Chinese characters to pictures is a relatively simple and feasible method. A picture refers to a structure composed of graphics, images, etc. Print media. There are many formats of pictures, but generally they can be divided into two categories: dot matrix and vector graphics. The characteristic of chaos is the orderly movement form that originally follows simple physical laws, and suddenly deviates from the expected regularity under certain conditions Instead, it becomes a disordered form. Chaos refers to the unpredictable, random-like motion of a deterministic dynamical system due to its sensitivity to the initial value. It is also called chaos. The English word comes from Greek, and its original meaning It is the scene before the beginning of the universe, and its...
Embodiment 3
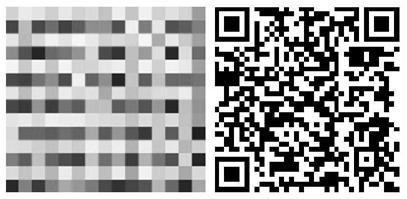
[0092] According to the above-mentioned encryption method for converting Chinese characters into pictures, the encryption steps are similar to those in Embodiment 1, and only a certain section of Chinese characters to be encrypted changes slightly: the first Chinese character "one" becomes "two"; or the 27th Chinese character "." becomes "!"; or the 55th Chinese character "But" becomes "Dan"; or the 100th Chinese character "Zhong" becomes "Zhong"; or the 151st Chinese character "De" becomes "地" ; or the 199th Chinese character "random" becomes "enemy"; or the 230th Chinese character "fu" becomes "fu"; or the 270th Chinese character "heavy" becomes "child"; or the 302nd Chinese character ". " into "combined", the encryption results of converting Chinese characters to pictures are shown in Table 2. It can be seen from Table 2 that a slight change in a certain Chinese character to be encrypted will cause the encrypted color picture to be "unrecognizable", so it can be seen that t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com