Robust security optimization design method of wireless energy-carrying security communication system
A technology of secure communication and wireless energy carrying, which is applied in the field of information technology security to achieve the effect of improving the security rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The technical solution of the present invention will be further described in detail below in conjunction with the accompanying drawings, but the protection scope of the present invention is not limited to the following description.
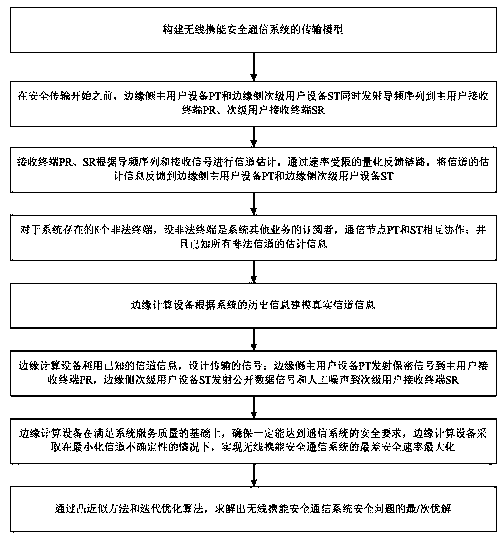
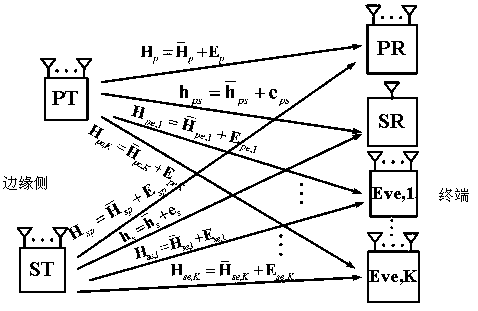
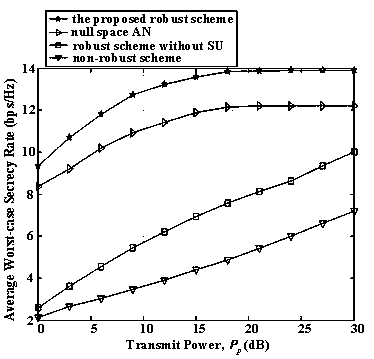
[0024] The present invention is an improvement to the security optimization design scheme of the edge computing security communication system based on wireless energy carrying. Since the complex non-convex security optimization problem is difficult to solve, the physical layer security under the current norm-bounded channel uncertainty model The transmission method is relatively simple, and usually only artificial noise is used to assist the safety communication link for safety enhancement. The present invention utilizes the secondary user transceiver link to further enhance the security performance of the communication system, specifically:
[0025] Such as figure 1 As shown, a robust security optimization design method for a wireless ene...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com