A relay-assisted non-orthogonal multiple access cooperative network security communication method
A non-orthogonal multiple access, cooperative network technology, applied in transmission monitoring, electrical components, radio transmission systems, etc., can solve problems such as information exposure, and achieve the effect of improving security and reducing the probability of security interruption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
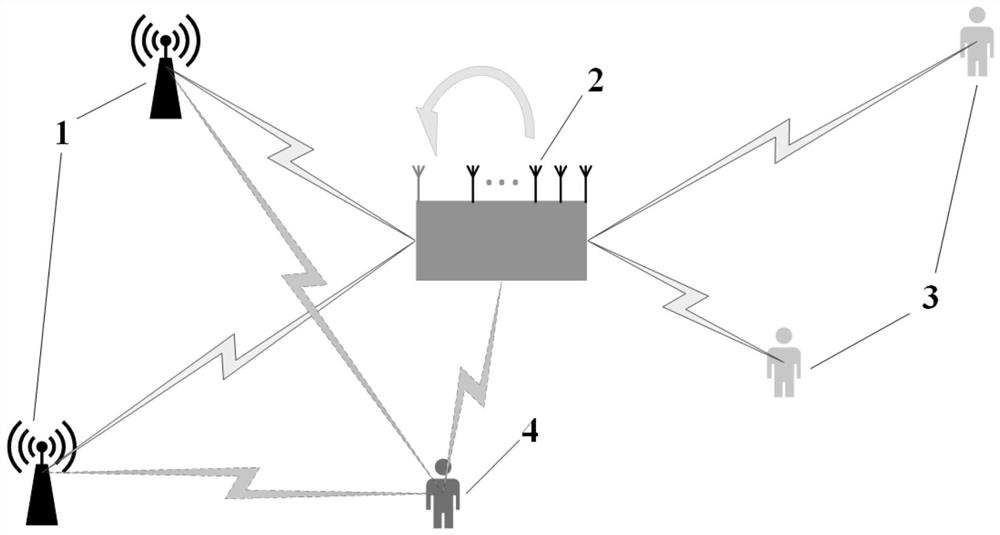
[0032] The implementation of a relay-assisted non-orthogonal multiple access cooperative network security communication method, firstly, in a double-source and double-sink NOMA network, the relay R is used as the information forwarding node, and the information transmission is divided into sub-source T 1 and T 2 Broadcast to relay R, and forward from relay R to destination user U 1 and U 2 Two phase transfer. The confidentiality rate threshold of each information is r 1 = r 2 =0.5, it is assumed that the channel between each node of the system is affected by Rayleigh fading. Set the lengths of the paths from the two information transmitters to the relay as 12m and 20m, the distances from the eavesdroppers to them are 20m and 12m respectively, and the distance from the relay to the destination user U 1 , U 2 , and the distances of the eavesdroppers are 80m, 20m and 16m respectively. Relay R uses one of the antennas to receive information. According to the working princi...
Embodiment 2
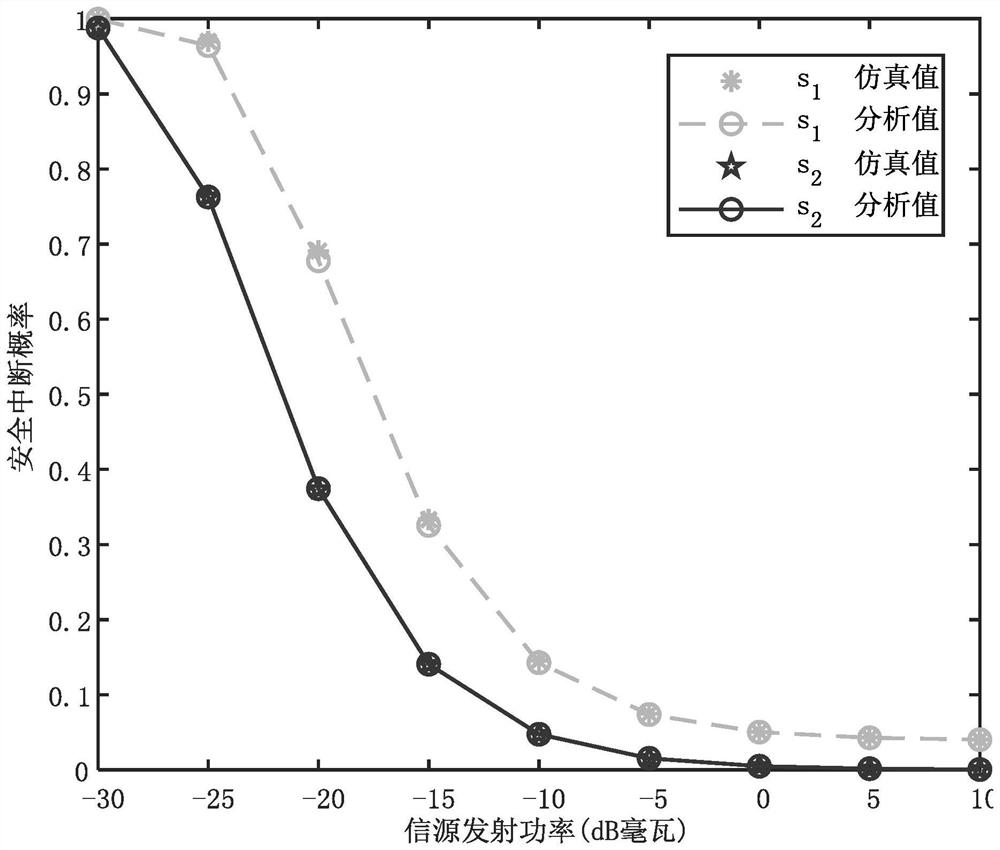
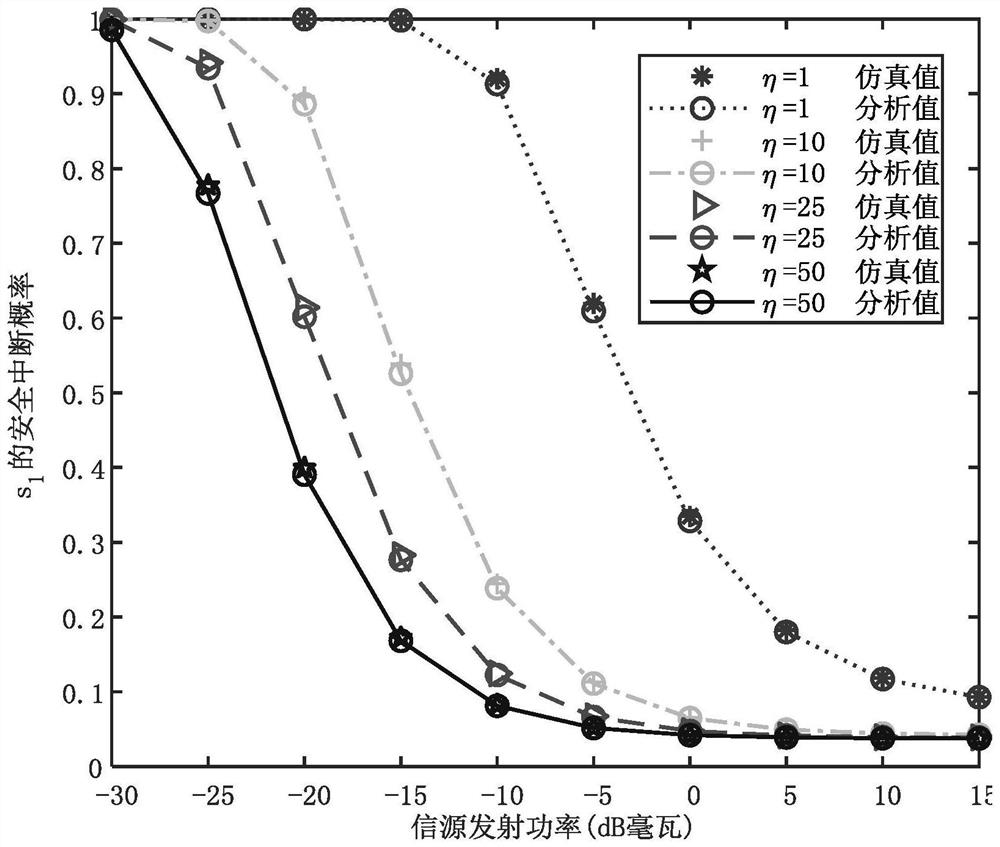
[0037] The new method of cooperative communication in user wireless network provided by the present invention can obtain the optimal power allocation coefficient α of artificial noise 5 , so that the system can reach the lowest SOP, so high EST transmission can be realized, and it can be applied to the fifth generation mobile communication system network with high confidentiality throughput to improve the transmission security of such systems.
[0038] The specific implementation is that the relay R is used as the information forwarding node, and the information is transmitted from the source T 1 and T 2 Broadcast to relay R, and then forward from relay R to destination user U 1 and U 2 . The channel between each node of the system is affected by Rayleigh fading, set T 1 and T 2 The path length to the relay is 12m and 20m, and the eavesdropper distance T 1 and T 2 20m and 12m respectively, relay R to destination user U 1 , U 2 , and the distances of the eavesdroppers ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com