Program bug testing method and related device
A testing method and program technology, applied in the computer field, can solve problems such as time-consuming, inability to meet vulnerability detection, affecting the efficiency of program vulnerability detection, etc., and achieve the effect of improving efficiency and reducing repetitive code writing.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
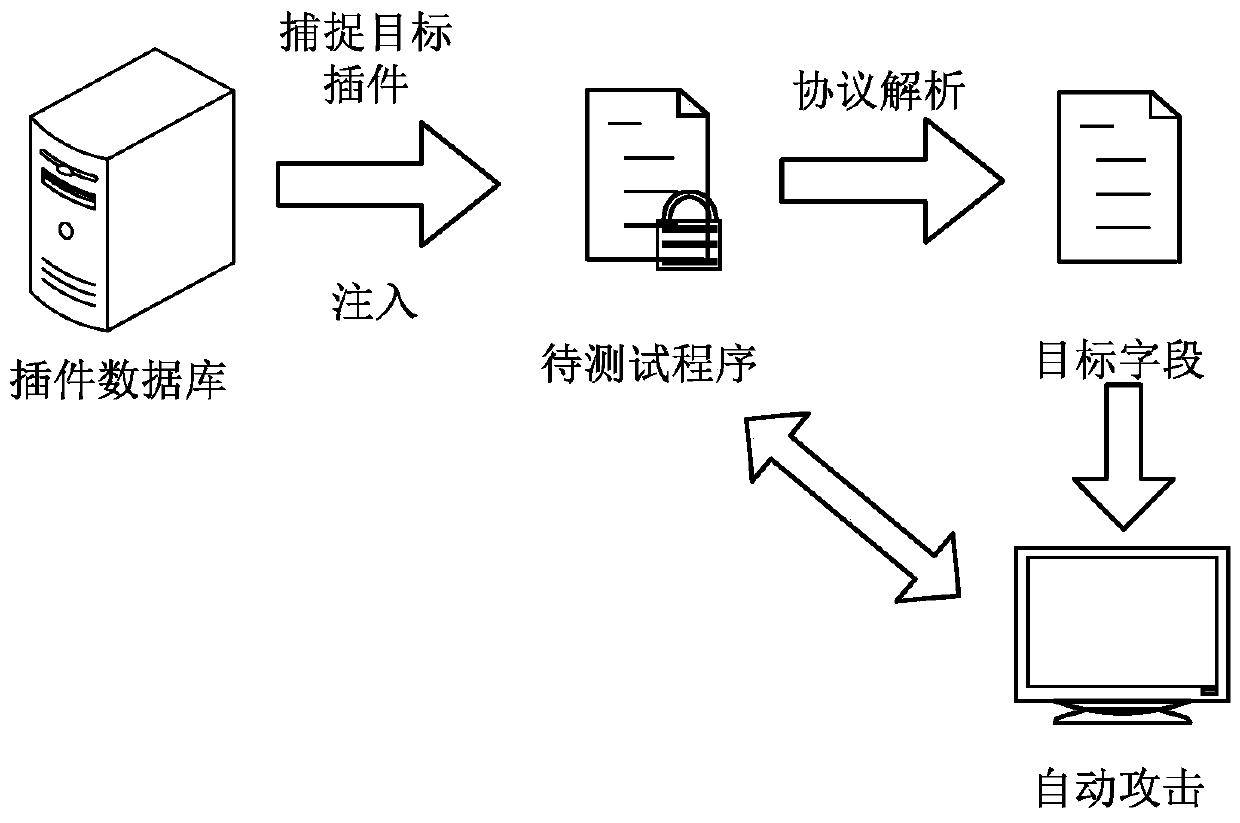
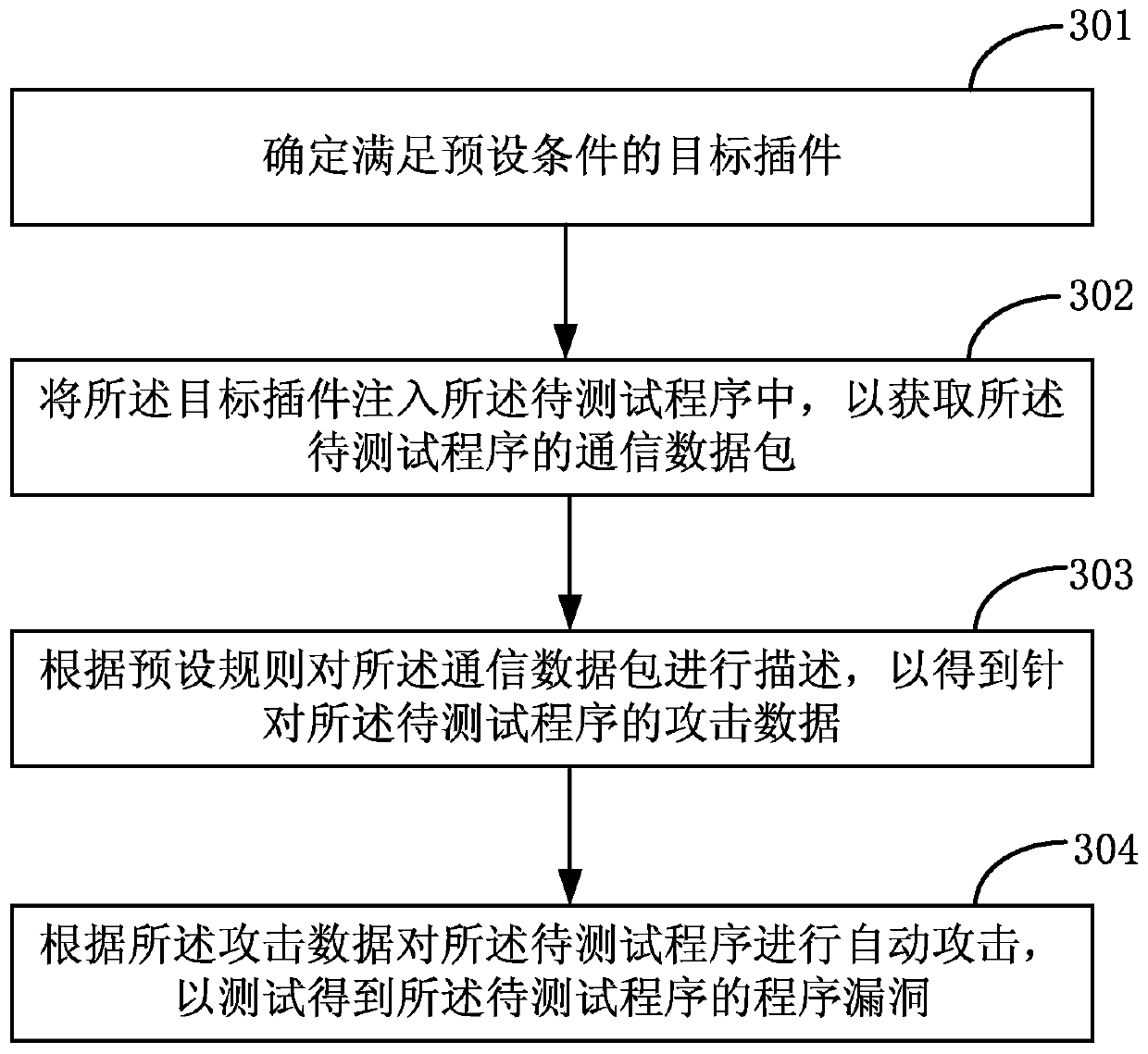
[0059] The embodiment of the present application provides a vulnerability testing method and a related device, which can be applied to the running process of a vulnerability detection system or a game vulnerability detection program, by determining the target plug-in that satisfies the preset condition, and the preset condition is based on the target determining the matching information between the plug-in and the program to be tested; then injecting the target plug-in into the program to be tested to obtain a communication data packet of the program to be tested; and describing the communication data packet according to preset rules, to obtain attack data for the program to be tested; and then automatically attack the program to be tested according to the attack data, so as to test and obtain the program vulnerability of the program to be tested. In this way, the auxiliary analysis and automatic attack of programs using complex encrypted communication protocols can be realized...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com