An authentication key agreement method and implementation device based on cross-interlock mechanism
An authentication key agreement and key agreement technology, which is applied in the field of authentication key establishment, can solve the problems that the participants cannot judge the initiator or the responder, unfavorably calculate the session key, and cannot detect attacks, etc., so as to improve the anti-jamming attack ability, high success rate, effect of ensuring symmetry
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
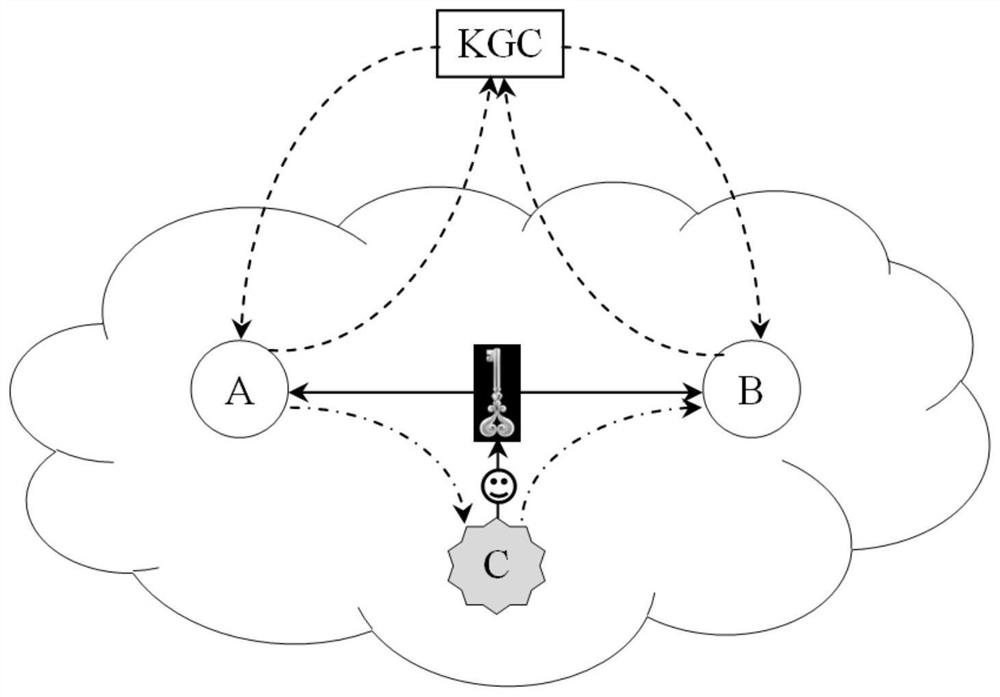
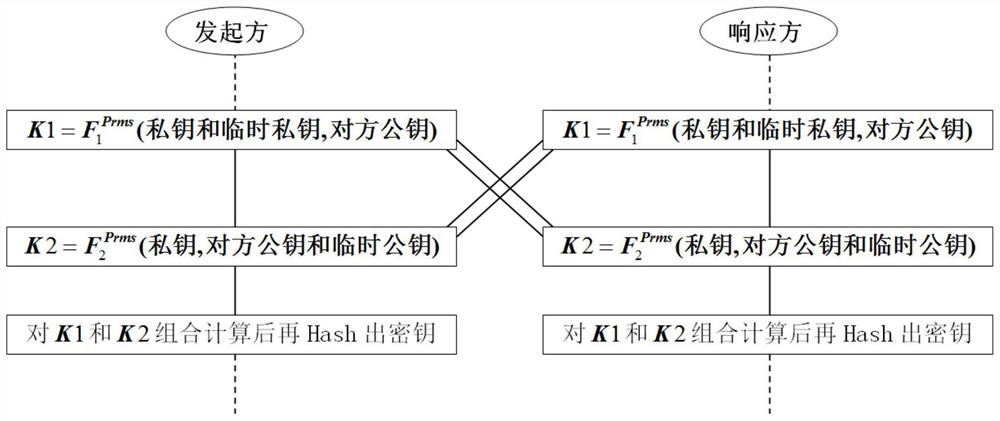
[0071] The invention is mainly based on the non-certificate authentication / self-authentication public key mechanism, and proposes a session key negotiation method and an implementation device for realizing two-party authentication through a cross-interlocking method based on difficult problems. This method fully considers the problem of preventing counterfeit attacks in the negotiation process, and ensures the reliability of the negotiation through the confirmation stage of the symmetric key after the negotiation. The authentication session key agreement through the invention is safer and more reliable.
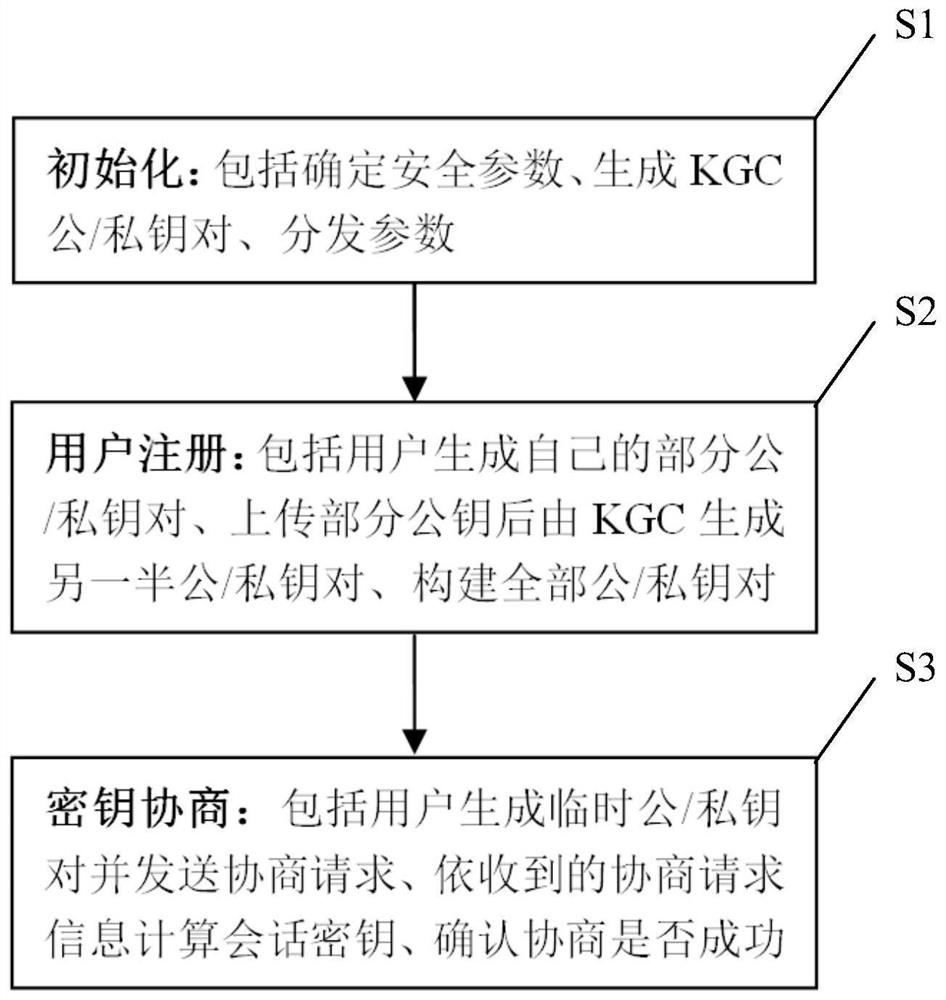
[0072] The implementation of the present invention can be divided into three stages and carry out (main process such as figure 2 shown):
[0073] Phase One (S1): Initialization.
[0074] First, select the public key primitive (such as ECC, RSA, etc.) Curve parameters, large prime numbers, etc.), select relevant security algorithms, Hash functions, etc.
[0075] Then gene...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com