Access authentication method of IMS network
An access authentication and network technology, applied in the field of data communication, can solve the problems of not being able to ensure data confidentiality and integrity, affecting user experience, information leakage, etc., to reduce authentication time, ensure confidentiality and integrity, and simplify The effect of the parameter
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] Embodiments of the present invention are described in detail below in conjunction with accompanying drawings:
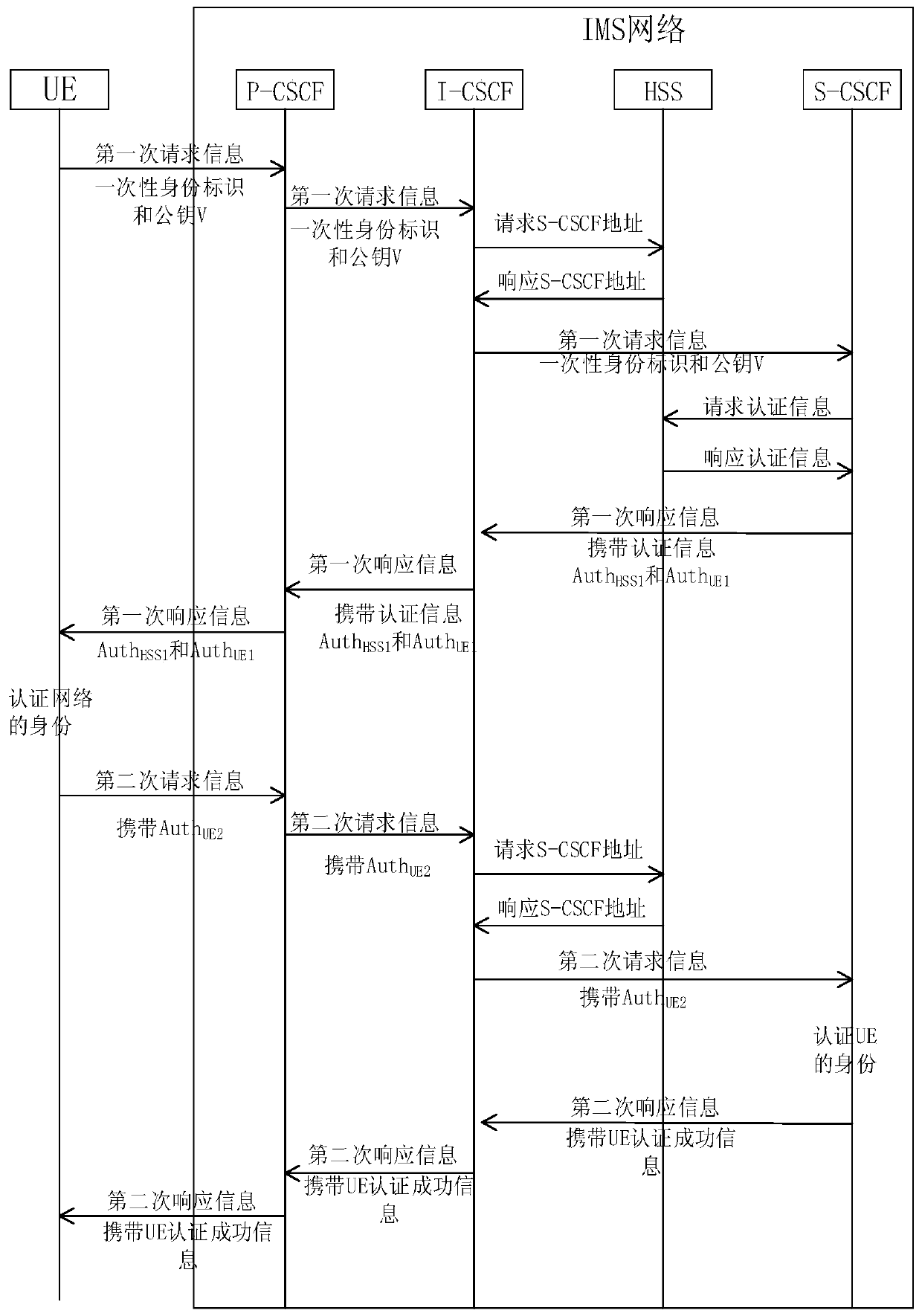
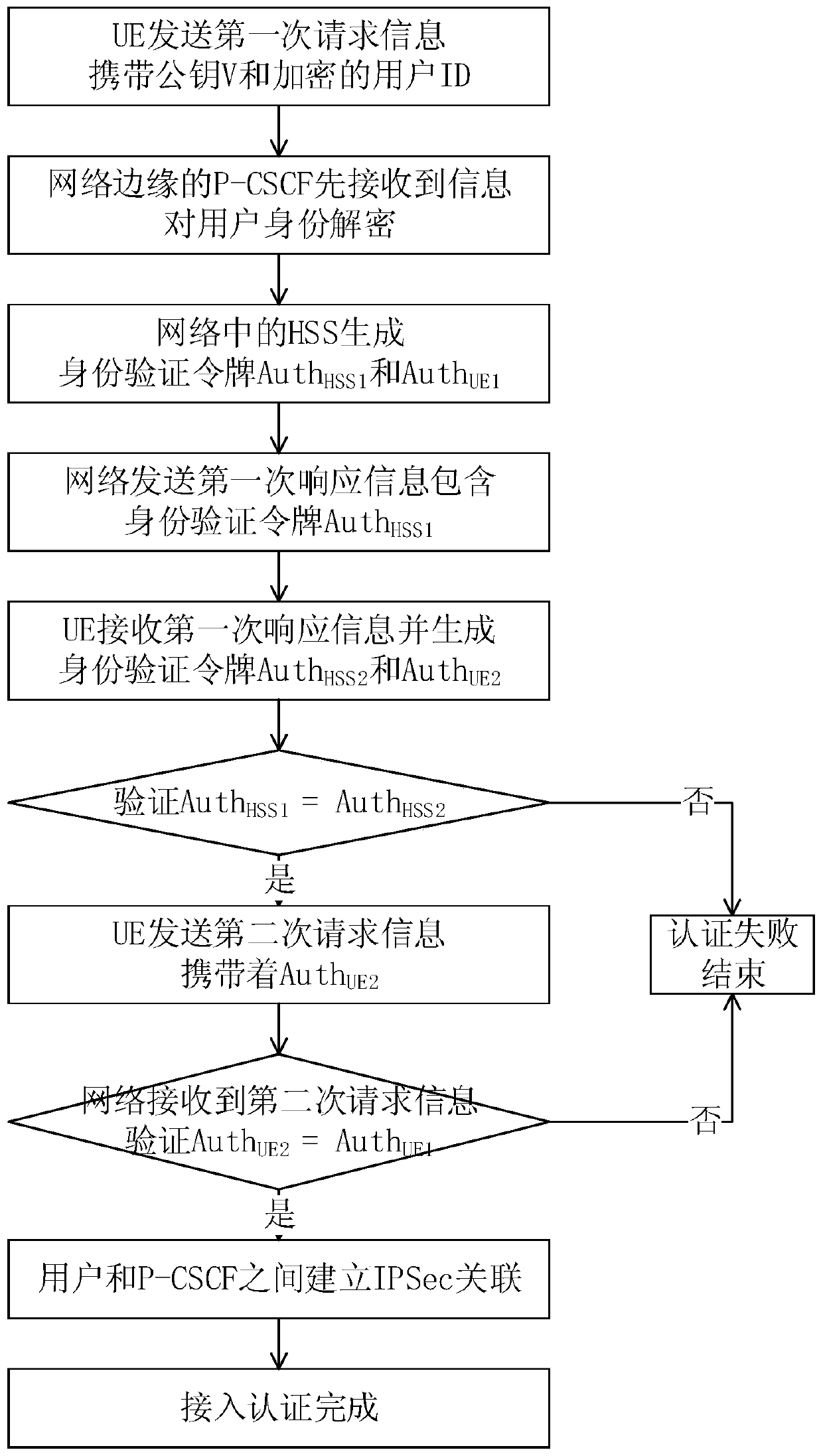
[0042] An access authentication method for an IMS network, comprising:
[0043] Step 1: The network encrypts the user ID. Before registration and authentication between the network and the user, the P-CSCF at the edge of the network exchanges encryption functions with the user to encrypt the user ID twice;
[0044] The user ID includes a user private identifier IMPI and a user public identifier IMPU.
[0045] Step 2.1: The user generates the public key V to send the first request information to the network, the user server (HSS) in the network generates the public key W after receiving the first request information, and the HSS generates the public key W according to the public key V and Public key W generates session key AICK HSS and the authentication token and send the first response information to the user, the authentication token includes the HSS authe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com