A method for monitoring information security domain of industrial control system
A technology for industrial control systems and information security, which is applied in the field of monitoring information security of industrial control systems, and can solve problems such as incomplete details
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] The present invention will be further described in detail below in conjunction with the accompanying drawings.
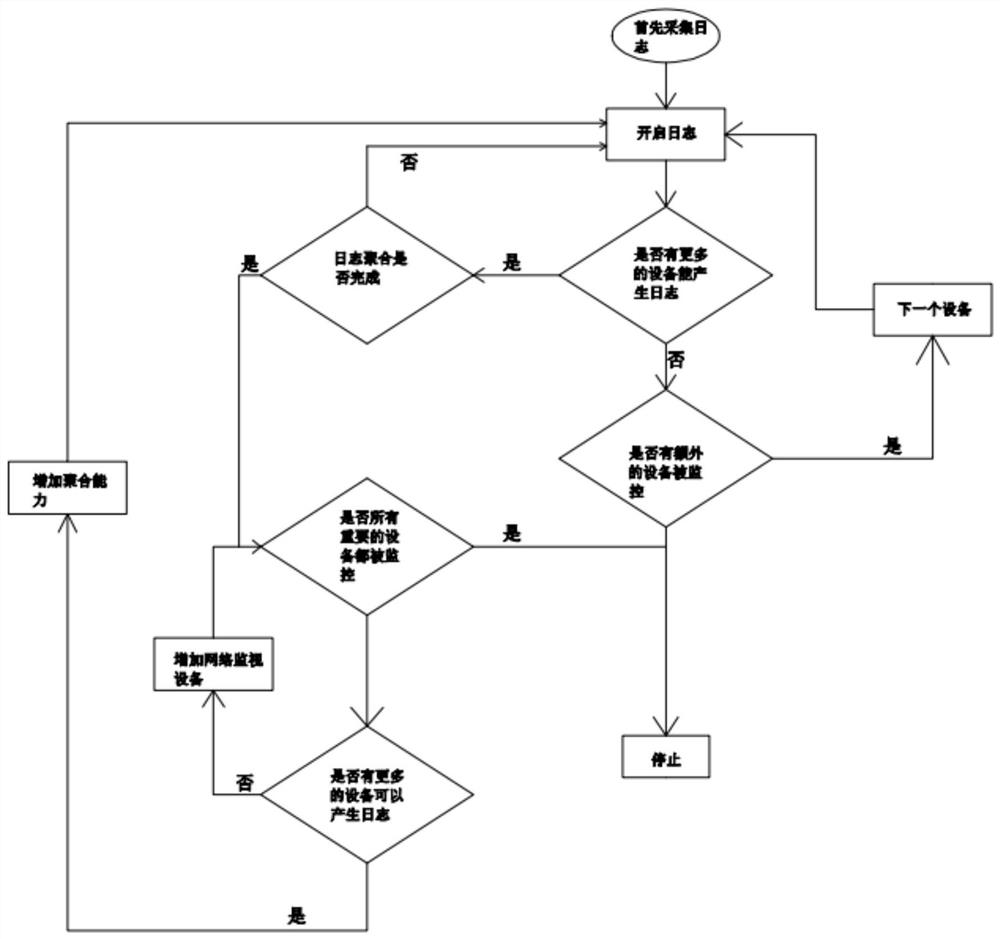
[0020] (1) Log collection
[0021] Log collection refers to collecting data from all possible sources of data, that is, guiding and outputting log information to a log collection node and using a network storage device. If events are stored in a local database rather than in log files, the event information needs to be reprocessed locally through a software agent such as snare and transmitted through the standard syslog. View user activities in the collected logs, including user configuration changes, online and offline user statistics, login operations performed by users, and offline operations performed by users. By analyzing the collected logs, if an abnormal phenomenon is detected, such as the increase of illegal new users, sensitive user operations, etc., a warning will be issued.
[0022] (2) Direct monitoring
[0023] Since some systems, such as RTU...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com