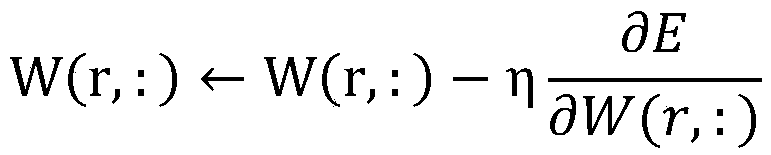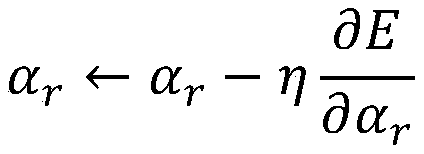Watermark encryption and decryption algorithm based on chaotic neural network
A neural network and watermark encryption technology, applied in the field of information hiding, can solve the problems of not being able to know the content, and the scrambling rules are easy to be cracked
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
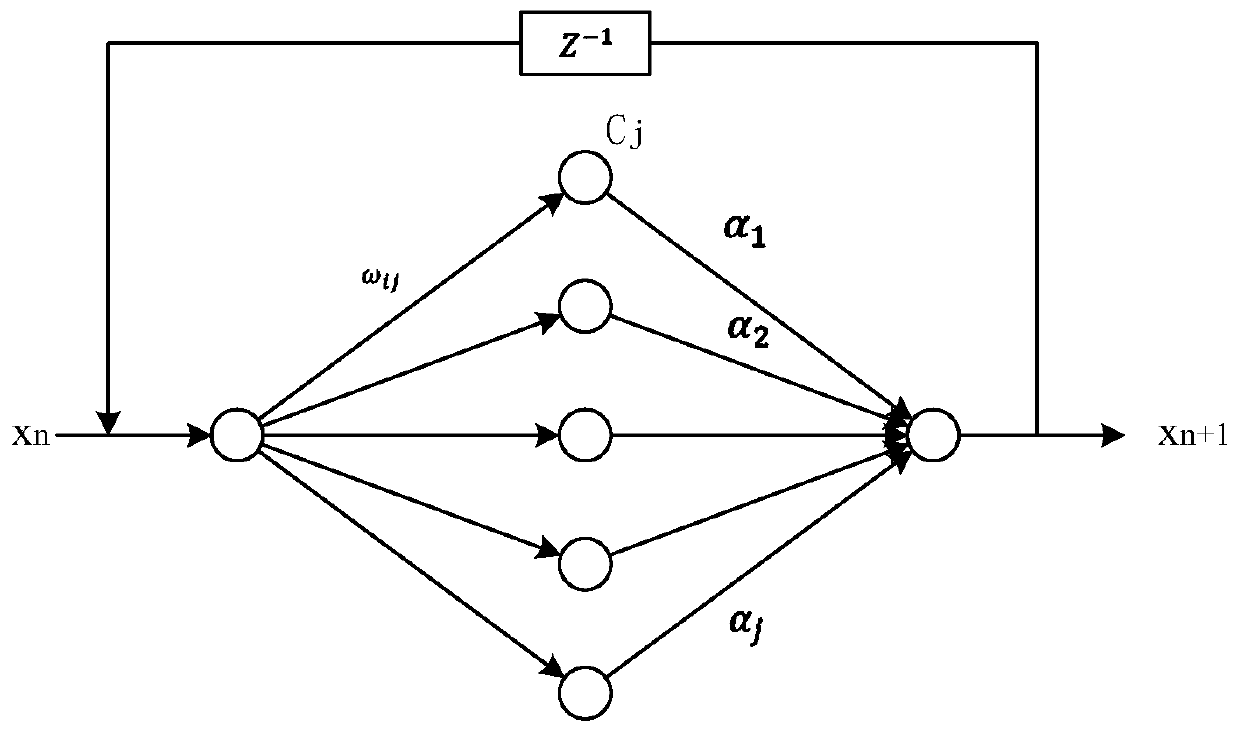
[0017] Step 1: Establish the LCNN neural network. figure 1 The schematic diagram of the LCNN neural network is shown, and the specific algorithm steps are described as follows:
[0018] 101. Initialize the input and output vectors of the neural network, and initialize the initial value x of the Logistic map 1 =0.32, iterate 220 times, generate chaotic sequence x k , put x k The last 200 sequences are used as the input vector and target vector of LCNN;
[0019] 102. First initialize the network weights W and α, and then use the obtained Logistic chaotic sequence x k Train the network, calculate the output t of the neural network, and then calculate the partial derivatives of the error E of the neural network to the network weights W and α respectively and r=1,...,m;
[0020] 103. Correct the weights of the neural network, namely: r=1,...,m;
[0021]
[0022]
[0023] 104. Calculate the error E of the neural network;
[0024] 105. If the exit condition of trainin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com