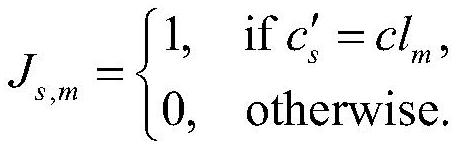A computing migration method considering privacy protection in wireless metropolitan area network environment
A wireless metropolitan area network and privacy protection technology, applied in the field of privacy protection and mobile network edge computing task planning, can solve problems such as cloud load balancing that has not taken into account user privacy protection, to reduce the risk of privacy leakage, improve load balancing, Optimum service performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
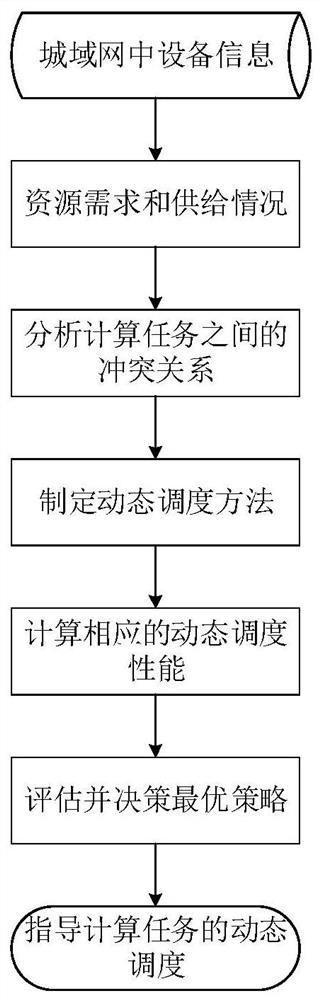
[0112] This embodiment simulates the dynamic scheduling of computing tasks in a wireless metropolitan area network.
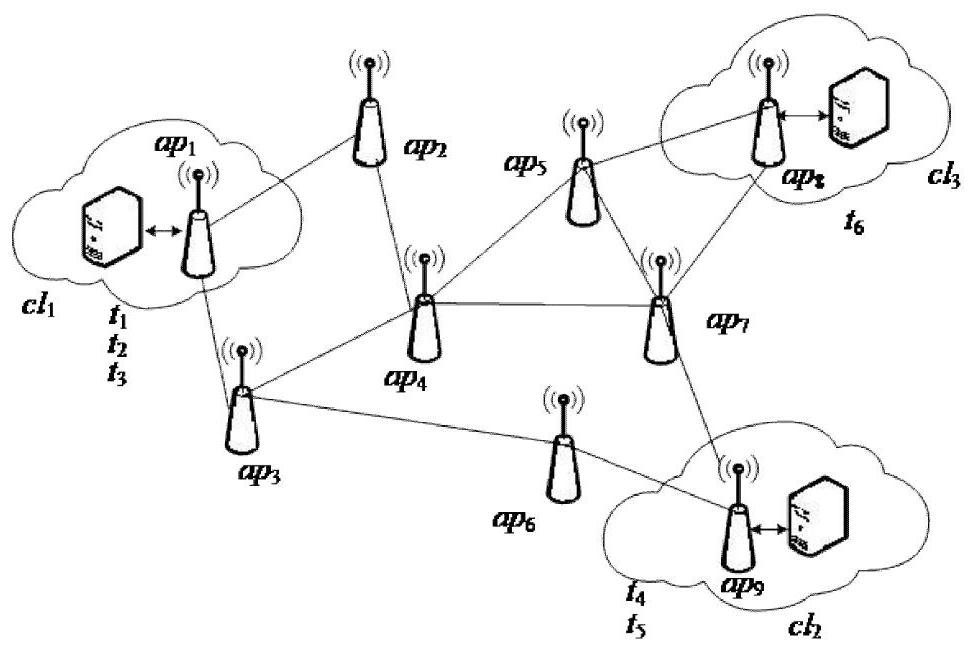
[0113] Such as figure 2 As shown, in the experiment, we consider the situation of 6 computing tasks, 3 clouds, and 9 access points, that is, CL={cl 1 ,cl 2 ,cl 3}, AP={ap 1 ,ap 2 ,...,ap 9},T={t 1 ,t 2 ,...,t 6}. Among them, the number of virtual machines in each cloud is 10. The information of each computing task is shown in Table 1.
[0114] Table 1 Computing task information
[0115]
[0116] It can be seen from Table 1 that t 1 and t 2 There is a data conflict between t 3 and t 5 There is a data conflict between t 4 and t 5 Execution required more resources than cl 2 Therefore, in order to ensure the smooth execution of tasks and protect the privacy of users, the initial task scheduling strategy needs to be modified.
[0117] if t 2 still in cl 1 on the implementation, then t 1 Needs to be rescheduled, can migrate to cl 2 or cl 3...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com