Trusted computing measurement method and system and computer readable storage medium
A technology of trusted computing and measurement methods, applied in computer security devices, computing, instruments, etc., can solve problems such as data tampering, untrustworthy trusted computing, and data loss
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
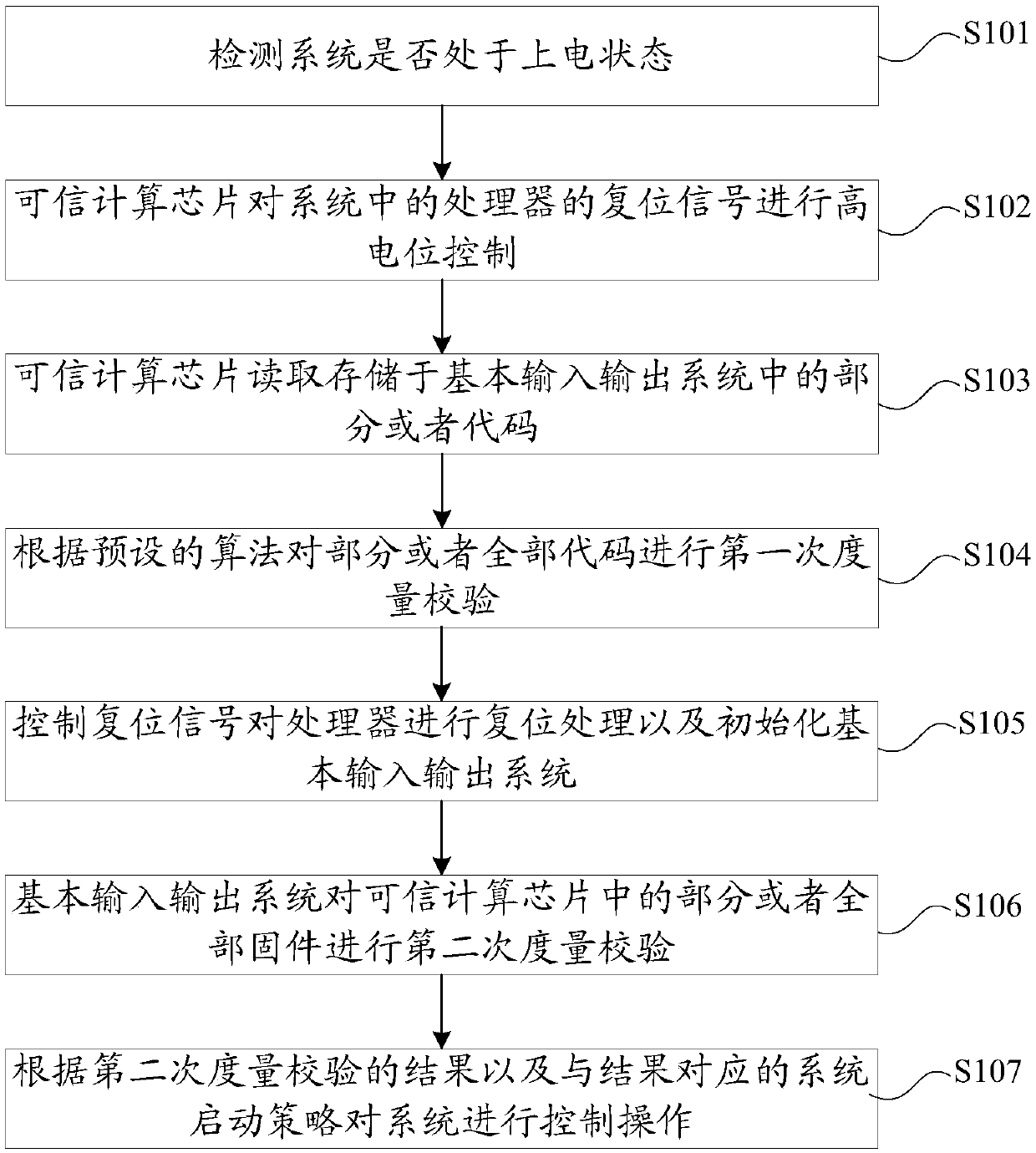
[0050] figure 1 For a flowchart of the trusted computing measurement method provided in Embodiment 1 of the present invention, please refer to figure 1 , the trusted computing measurement method provided by this embodiment includes the following steps:
[0051] S101: Detect whether the system is in a power-on state, if yes, perform step S102; otherwise, continue to detect the power-on state.
[0052] In this embodiment, the system here refers to a communication or terminal system including all components such as a trusted computing chip, a basic input output system, and a processor, and may also refer to a basic input output system.
[0053] The number of power supply units may be one or more. Preferably, only one power supply unit is selected in this embodiment, and this power supply unit is used to supply power to all units in the entire system, and here in When the system is powered on, all units in the system will be powered on, but the power-on status detected here is m...
Embodiment 2
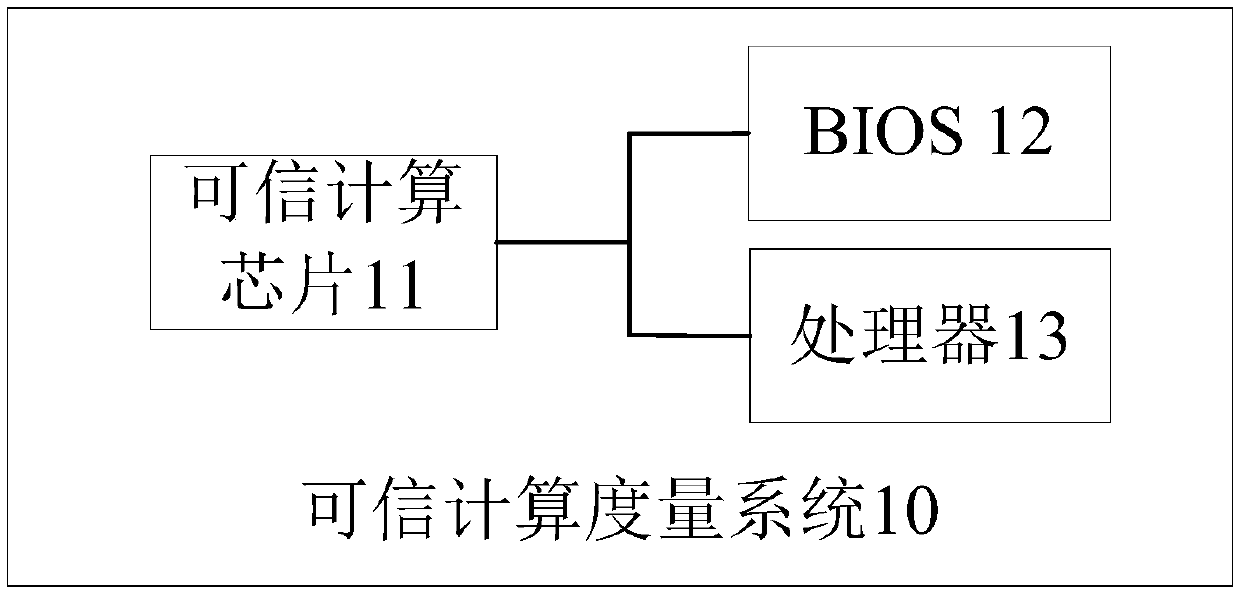
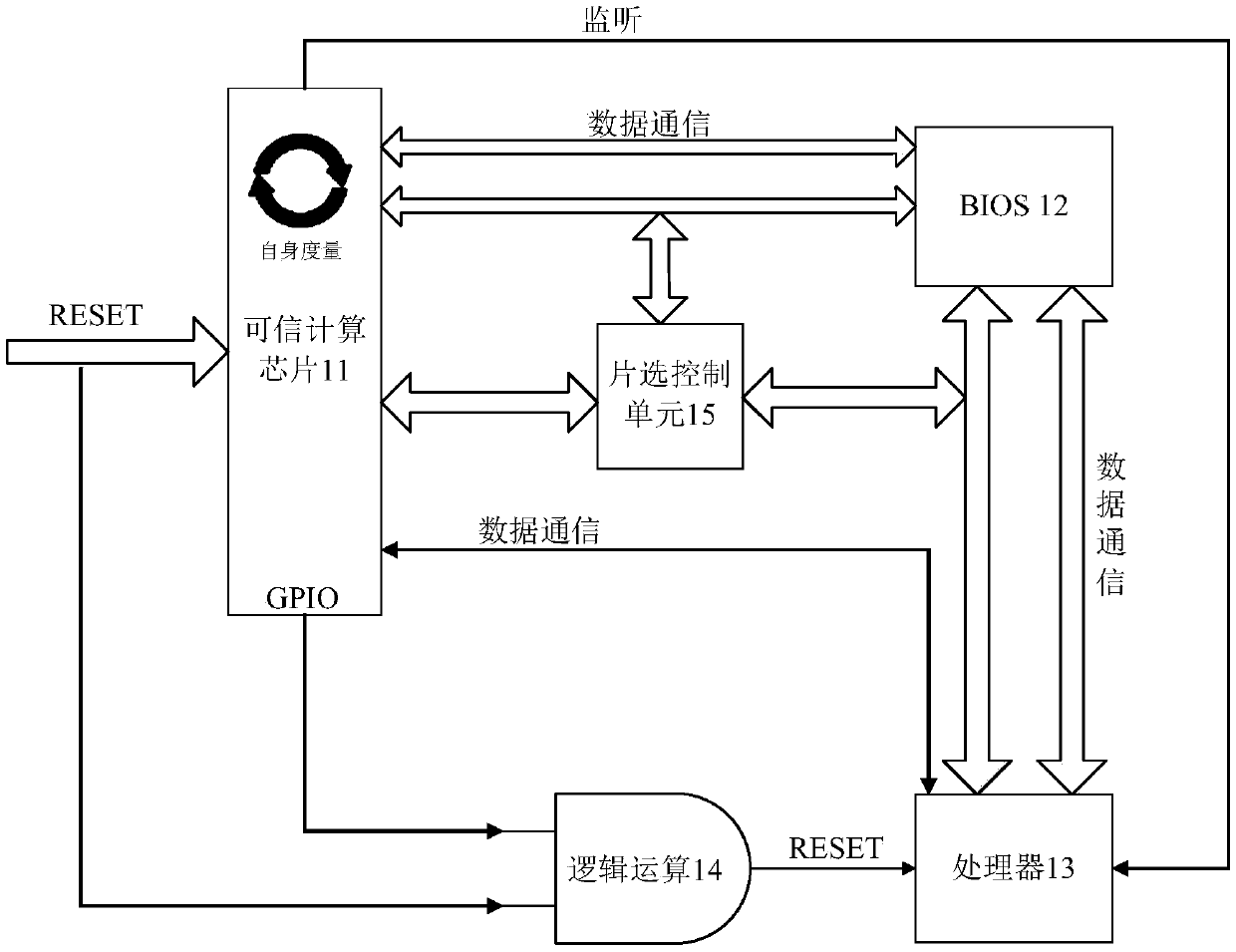
[0086] figure 2 It is a schematic structural diagram of the trusted computing measurement system provided by the second embodiment of the present invention, please refer to figure 2 , the trusted computing measurement system 10 provided in this embodiment specifically includes: a trusted computing chip 11 , a basic input output system 12 and a processor 13 , wherein
[0087] The trusted computing chip 11 is used to perform high-level control on the reset signal of the processor 13 in the system when the trusted computing measurement system is powered on, and read the data stored in the basic input output system 12 of the system. For part or all of the code, the first metric check is performed on the part or all of the code according to a preset algorithm.
[0088] If the first metric verification passes, the trusted computing chip 11 controls the reset signal to reset the processor 13 and initialize the basic input output system 12 .
[0089] The basic input output system ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com