Description, generation and detection method of corpus product rule for password guessing
A detection method and rule technology, applied in the field of password guessing, can solve problems such as large computational overhead, inappropriate password segmentation, and difficulty in providing a unified processing mode for corpus vocabulary.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
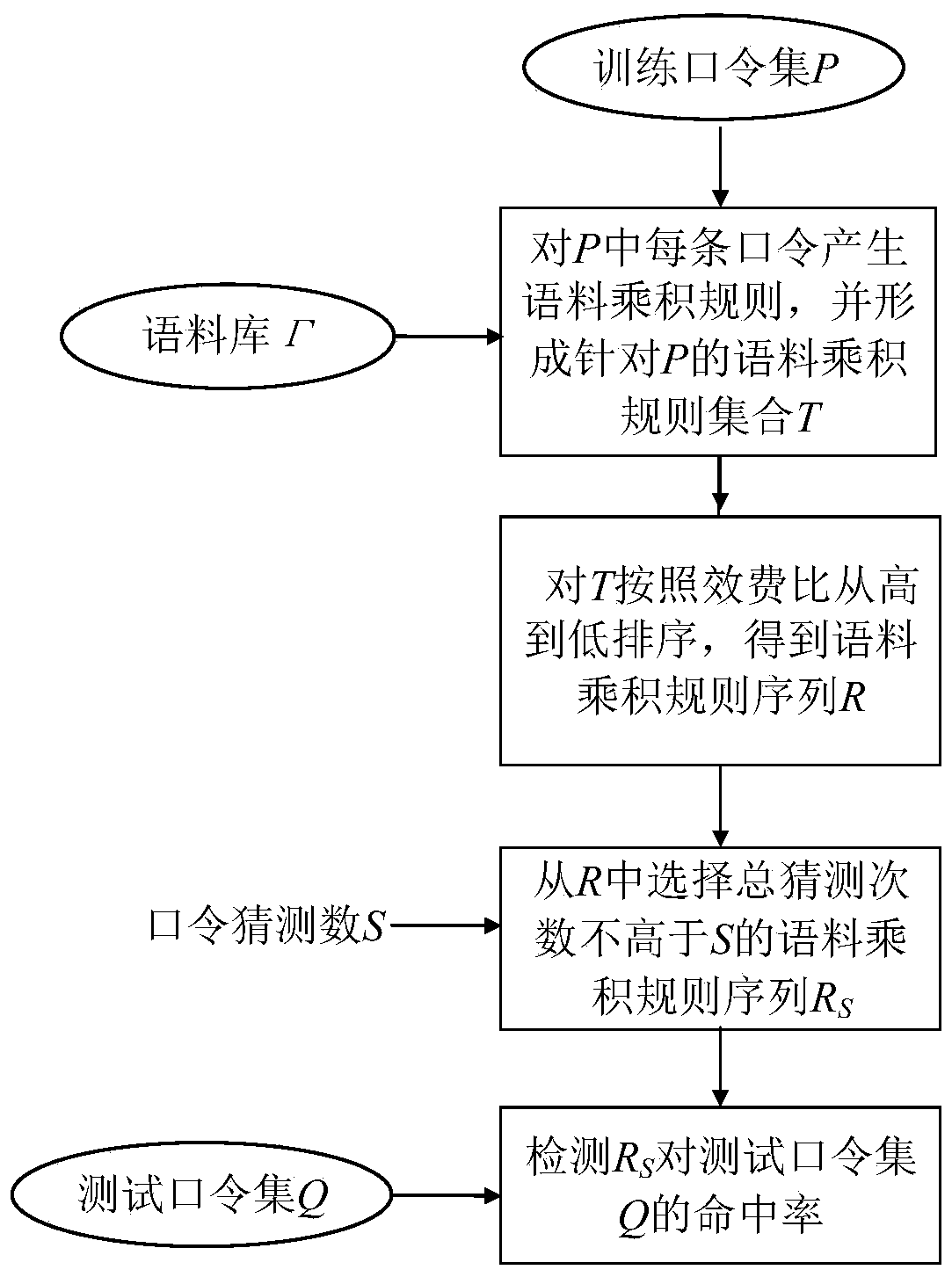
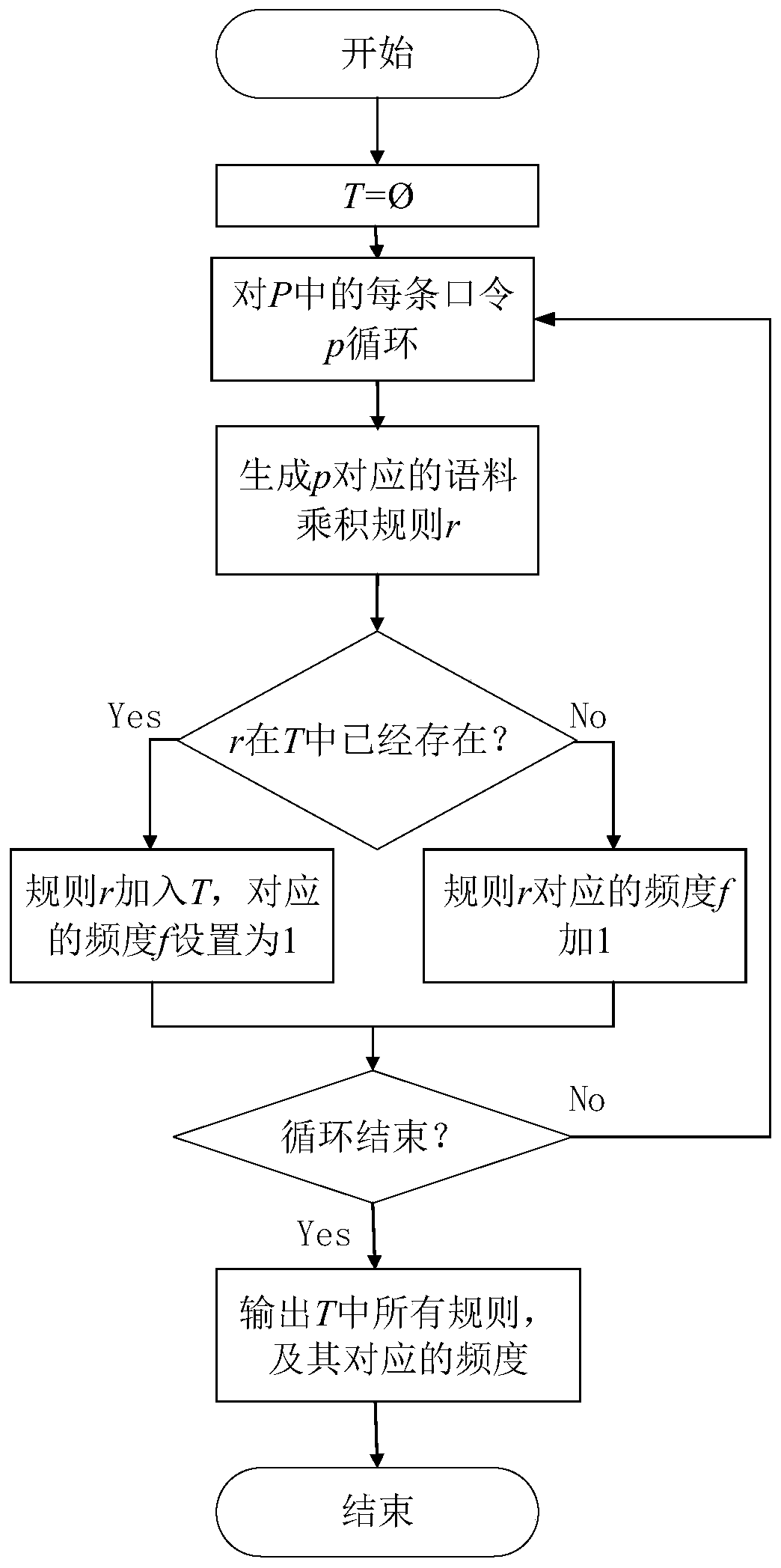
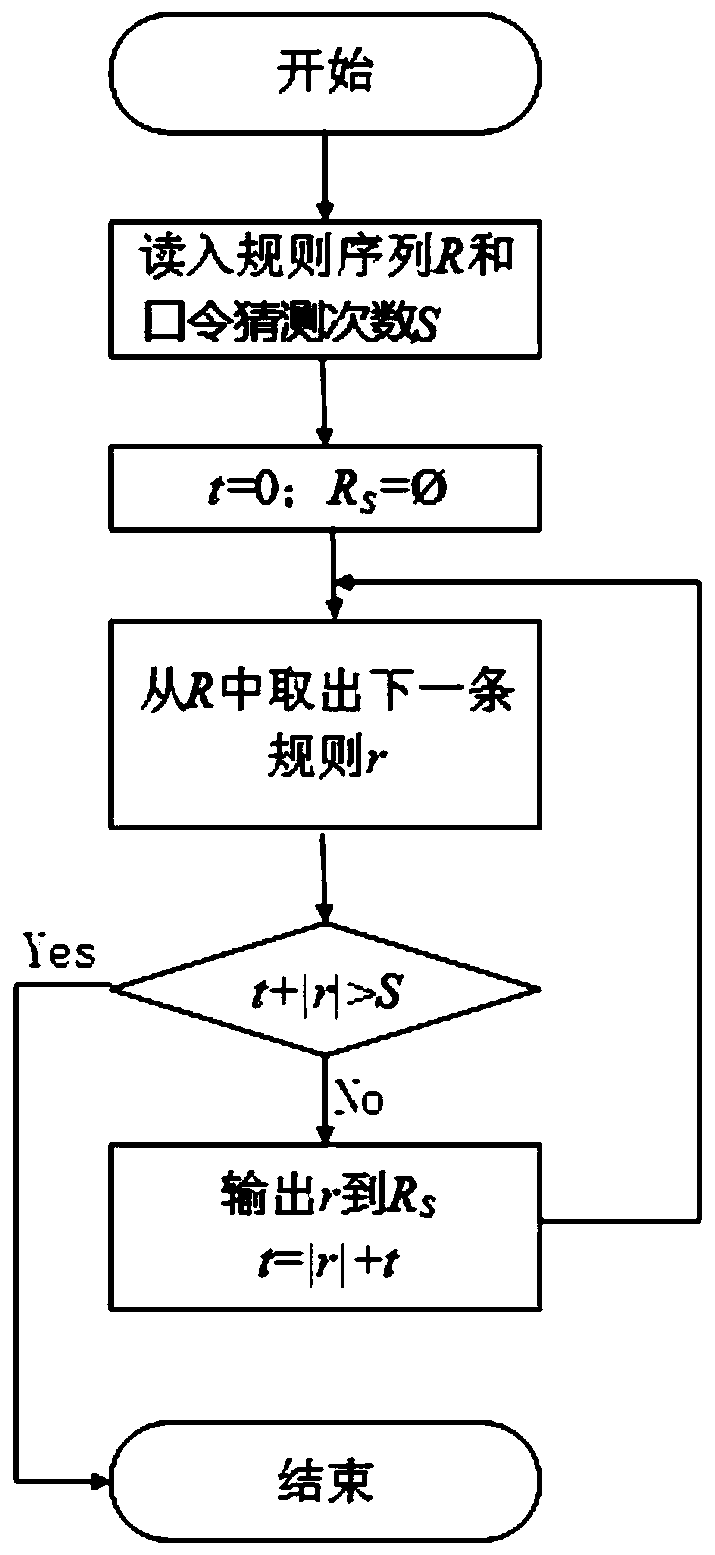
Image
Examples
Embodiment 1
[0118] The password "loverain" contains multiple words, including "love", "lover", "over", "in" and so on. Based on these words, a directed acyclic graph of "loverain" can be formed, such as Figure 5 shown.
[0119] Each path in the directed acyclic graph of the password "loverain" has a weight, and the weight of each path is equal to the number of words in the corresponding corpus. Among them, the number of words in the corpus EN0_2 of "in" is 255, the number of words in the corpus EN0_4 of "love", "over" and "rain" is 5620, and the number of words in the corpus EN0_5 of "lover" is 2977. The vocabulary size of the lowercase alphabet road corpus is 26.
[0120] Traverse the directed acyclic graph to get all possible paths from the start point to the end point. Each path corresponds to a rule, and thus the number of guesses and the number of segments corresponding to the path and rule can be obtained. The password "loverain" has the following 8 paths, as shown in Table 1: ...
Embodiment 2
[0125] In this embodiment, the password set Rockyou is used as the training set, and the password set phpBB is used as the test set. When the number of guesses changes, the hit rate of the test set in the present invention is shown in Table 2, and the relationship between the number of guesses and the hit rate Such as Image 6 shown.
[0126] Table 2
[0127] number of guesses 10 8
10 9
10 10
10 11
10 12
10 13
10 14
10 15
hit rate 38% 52% 63% 72% 80% 86% 90% 94%
[0128] Table 3 shows the guessing hit rate compared with the password guessing methods in the present invention and related papers. In most cases, the hit rate of the password of the present invention is obviously better than the existing experimental results in most cases, and there is only one exception, that is, when the total number of guesses is small, the present invention is slightly weaker than the 5th order Markov process, and this is due to The g...
Embodiment 3
[0135] The corpus Γ is set to only contain four types of corpus collections such as uppercase letters, lowercase letters, letters and numbers, then the method of the present invention can generate a sequence of brute force guessing rules.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com