Internet of Things terminal security authentication method based on security chip
An Internet of Things terminal and security chip technology, applied in the field of Internet of Things, can solve problems such as potential safety hazards, achieve high security levels, strong defense capabilities, and reduce the effect of system coupling
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
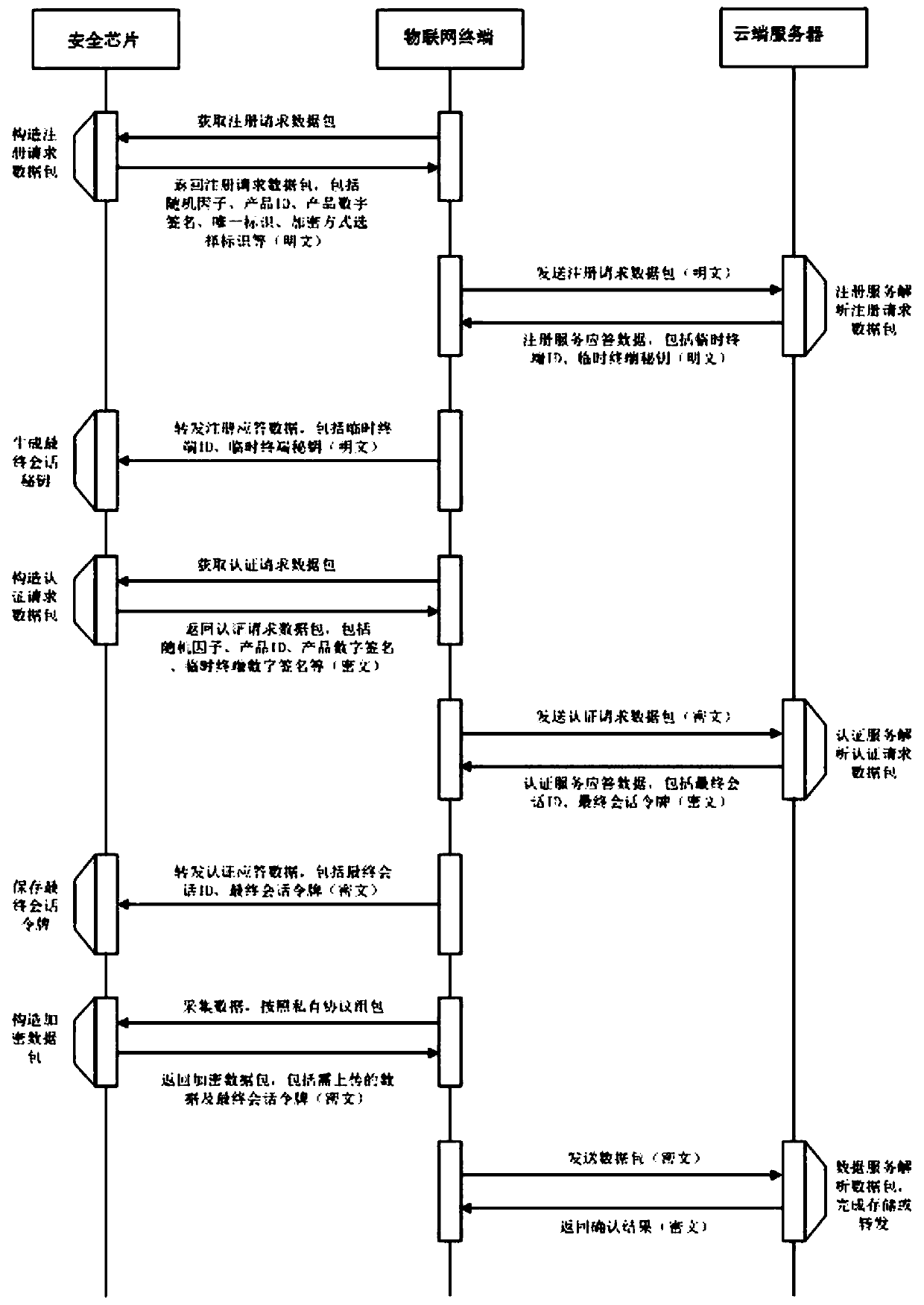
[0035] figure 1 It is a flow chart of a security chip-based IoT terminal security authentication method according to an embodiment of the present application, wherein the main process of the IoT terminal security authentication method is shown.
[0036] This embodiment provides a security chip-based IoT terminal security authentication method, such as figure 1 shown, which includes:
[0037] 101: A network connection is formed between the IoT terminal and the cloud server;
[0038]102: The security chip set in the IoT terminal constructs a registration request and sends it to the cloud server, and the cloud server verifies the legitimacy of the IoT terminal according to the registration request, and generates the IoT terminal corresponding to this session after the verification is successful. The temporary terminal ID and the temporary terminal secret key are saved, and then the server-side final session secret key is generated in the cloud server, and the generated temporar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com