Initial access control method and device, terminal, intelligent card and storage medium
An initial access and control method technology, applied in the field of communication, can solve the problems of unprotected pseudo base station attack, low security of the terminal initial access process, etc., and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0030] Aiming at the problem in the related art that during the initial access process of the terminal accessing the core network, the preventive control for the base station is blank, this embodiment provides an initial access control method, which can be implemented in the terminal During the initial access process of accessing the core network, attacks by pseudo base stations on the terminal are avoided as much as possible, thereby improving the security of the initial access of the terminal and the satisfaction of user experience.
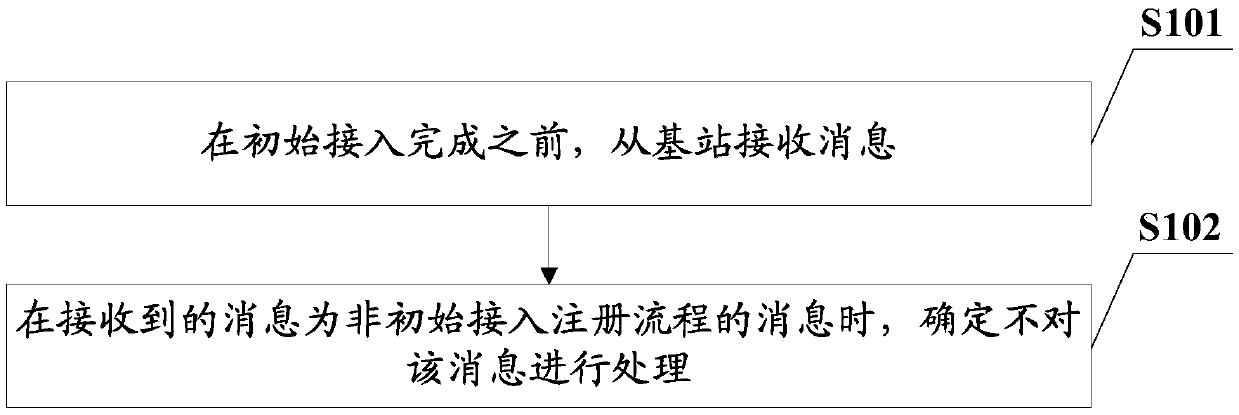
[0031] For ease of understanding, this embodiment follows the figure 1 The initial access control method shown is an example for illustration, see figure 1 shown, which includes:
[0032] S101: Receive a message from a base station before initial access is completed.
[0033] Before the initial access in this step is completed, it means that the terminal is before initial access to the core network to be accessed; the base station in this ste...
Embodiment 2
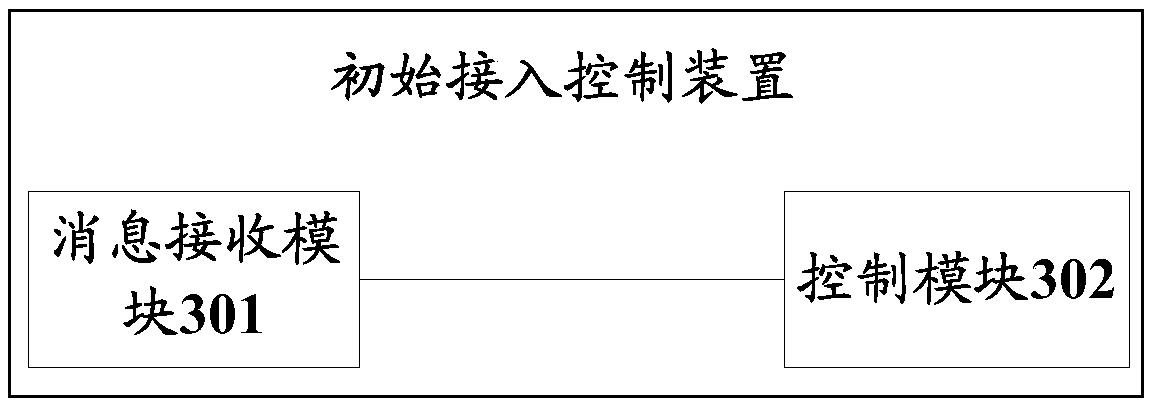
[0068] This embodiment provides an initial access control device, the initial access control device can be directly set in the terminal, or set in a component that can be separated from the terminal, see image 3 shown, which includes:
[0069] The message receiving module 301 is configured to receive a message from the base station before the initial access of the terminal is completed.
[0070] The control module 302 is configured to determine not to process the message when the message received by the message receiving module 301 is not a message of an initial access registration process.
[0071] In an example of this embodiment, when the received message is a message of an initial access registration procedure, the control module 302 may be configured to process the message. The processing can be normal processing of the message.
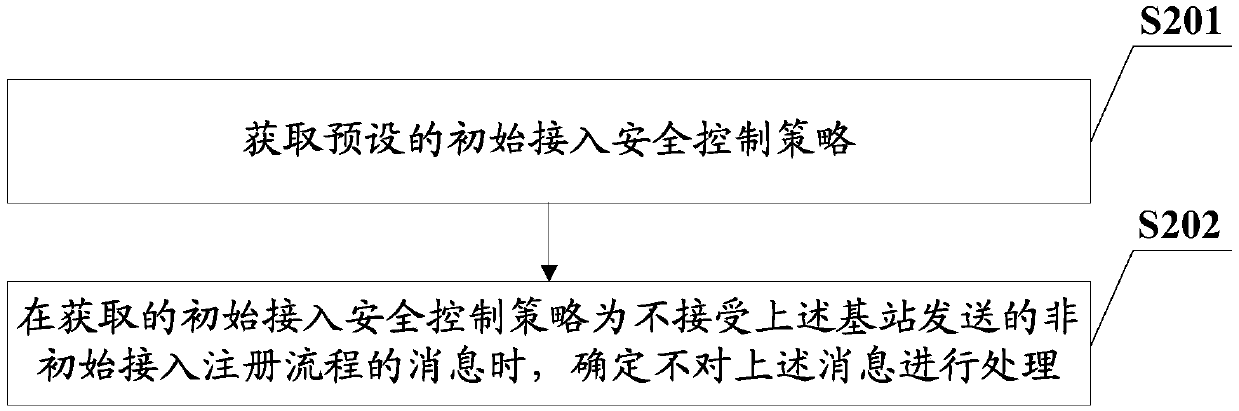
[0072] In an example of this embodiment, when the control module 302 receives a message sent by the base station that is not a message of a ...
Embodiment 3
[0090] This embodiment provides a terminal. The terminal in this embodiment can be a variety of communication terminals that can communicate with the core network through the base station, and can include various mobile terminals, and can also be non- mobile terminal. see Figure 4 As shown, it includes a first processor 401, a first memory 402 and a first communication bus 403;
[0091] The first communication bus 403 is used to connect the first processor 401 and the first memory 402;
[0092] The first processor 401 is configured to execute the computer program stored in the first memory 402, so as to implement the steps of the initial access control method shown in the above embodiments. The first memory 402 here may be the terminal's own memory; it may not include the memory provided on the terminal part that can be separated from the terminal; of course, it can also be set to include the memory provided on the terminal part that can be separated from the terminal accor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com