Fundus blood vessel image segmentation adversarial sample generation method and segmentation network security evaluation method
A blood vessel image and anti-sample technology, applied in the field of medical image processing, can solve suboptimal problems and achieve the effect of verifying security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0044] The invention discloses a method for generating an adversarial sample for fundus blood vessel image segmentation, which includes the following steps:
[0045] Step 1, establish fundus blood vessel image segmentation network f;
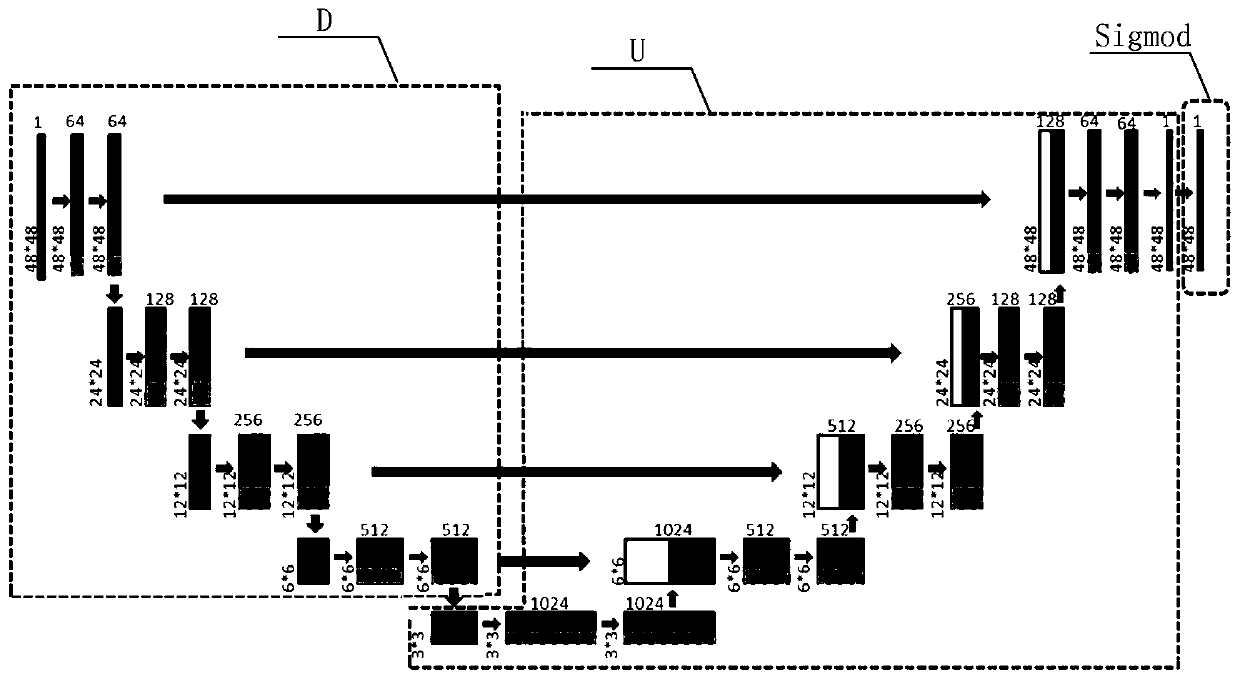
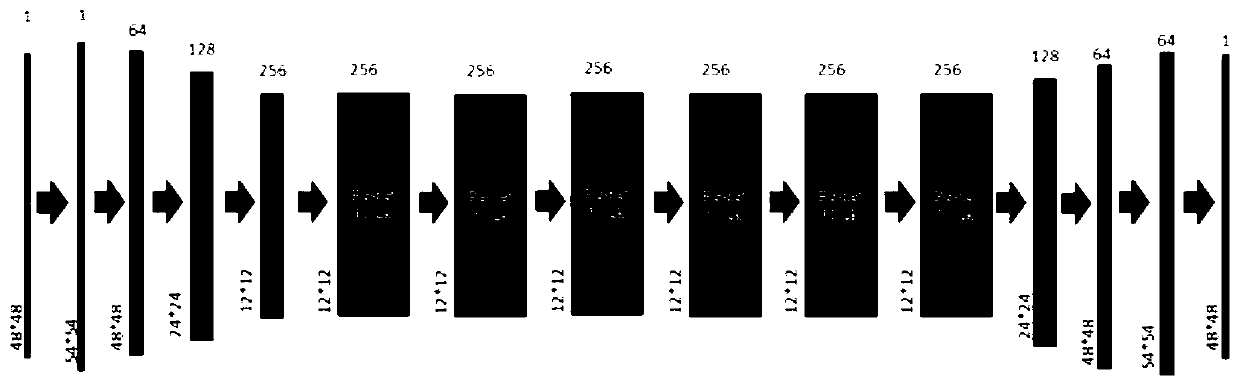
[0046] In this embodiment, the fundus blood vessel image segmentation network is a U-Net network, such as figure 2 As shown, it includes four lower convolutional layers D, four upper convolutional layers U and one sigmoid operation layer; one lower convolutional layer contains two convolutional layers and one pooling layer; one upper convolutional layer contains two Convolutional layers, a deconvolutional layer, and a concatenation operation.
[0047] In the present invention, on the original U-Net network structure, the convolution operation is set with kernelsize as 3 and padding as 1, which ensures that the size of the image remains unchanged after the convolution operation. The pooling operation selects the maximum pooling method, and the...
Embodiment 2
[0074] In this embodiment, an adversarial example is generated through a general perturbation. A general perturbation is a fixed perturbation, unlike one per image, a general perturbation can be applied to all original images and fool their pre-trained segmentation models.
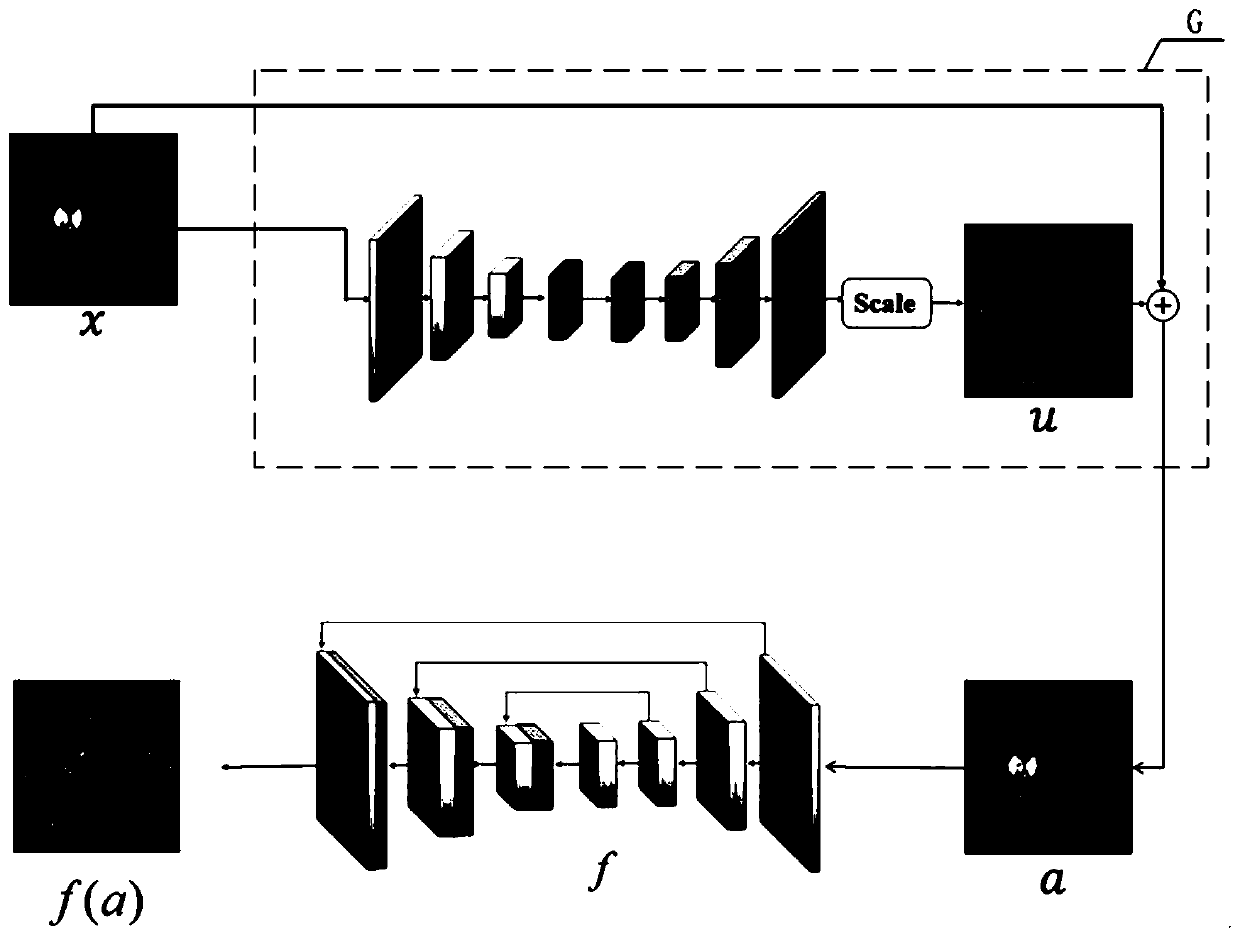
[0075] Let X represent the fundus blood vessel image in the pixel space R d distribution within , f is the segmentation model with high accuracy on X. The goal of the general perturbation is to find a fixed pattern u∈R d , so that for satisfy:
[0076] f(x+u)≠f(x), s.t.||u|| p ≤σ(5)
[0077] The parameter σ is the preset threshold, which means that the general disturbance u performs L p Upper bound for norm constraints. In order for the disturbance to be imperceptible to the human eye, σ needs to be small enough. Such as Figure 5 As shown, it is a schematic diagram of the model framework for generating adversarial samples for fundus blood vessel image segmentation in this embodiment.
[0078] B...
Embodiment 3
[0085] In this embodiment, the Dice coefficient before and after the attack is used to evaluate the security of the fundus blood vessel image segmentation network, as shown in Table 1 for non-target attacks.
[0086] Table 1 Dice coefficient after non-target attack on U-Net network (initial value is 68.5%)
[0087]
[0088] It can be seen from Table 1 that compared with the output of the previous segmentation model and the Dice coefficient of manually marked pictures of 68.5%, after the attack, the Dice coefficient drops significantly, indicating that the segmentation network has made a significant difference to the input image with disturbances invisible to the human eye. The very different segmentation results indicate that the U-Net network used for segmentation is very vulnerable to counter-perturbations and is extremely vulnerable to attacks. After being attacked, the Dice coefficient drops sharply. For example in L ∞ When = 20, the Dice coefficient drops from 68.5% t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com