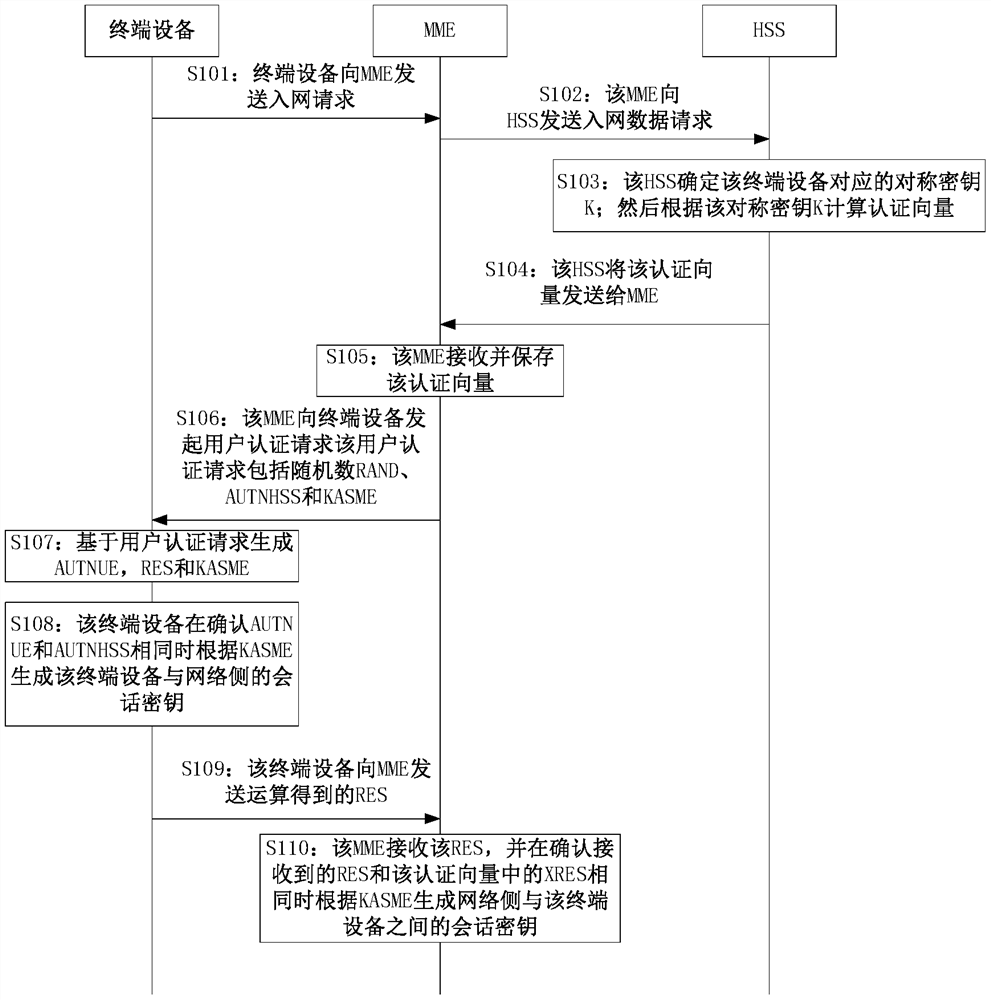
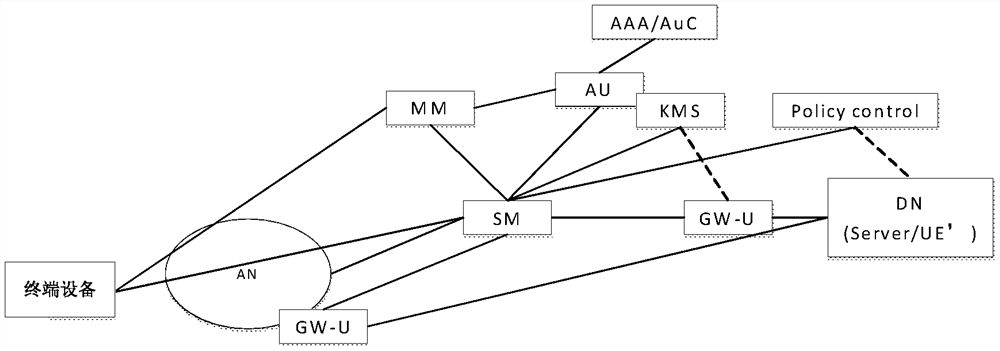
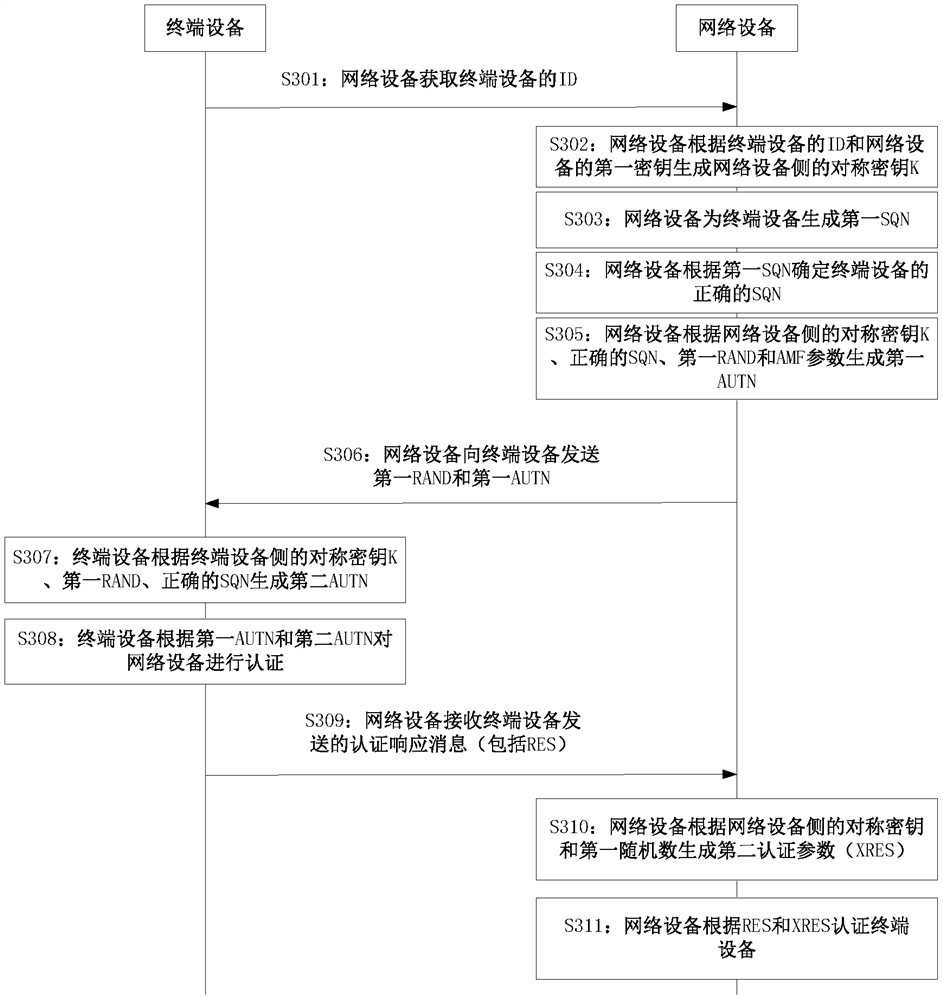
Network authentication method, network device, terminal device and storage medium
A technology of terminal equipment and network equipment, applied in the field of communication, can solve the problems of network authentication efficiency, long network authentication chain, HSS load pressure and other problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0121] The terminal devices involved in this application can be called Internet of things (IoT) devices, and the terminal devices can be computers, mobile phones, printers, refrigerators, robots, sensors, electricity meters, water meters, etc., which can be connected to IoT terminal equipment.
[0122]The network device involved in this application is a device that can perform network authentication with a terminal device. The network device may be an access network device, such as a Base Transceiver Station (BTS) in Global System of Mobile communication (GSM for short) or Code Division Multiple Access (CDMA for short). In , it may also be a base station (NodeB, NB) in Wideband Code Division Multiple Access (WCDMA for short), or an evolved NodeB in a Long Term Evolution (Long Term Evolution, LTE) network, An eNB for short), an access point (Access Point, AP) or a relay station, may also be a base station in a 5G network or a new generation of wireless access technology (New R...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com