Information system service security evaluation method
A security assessment and information system technology, applied in computer security devices, instruments, electrical digital data processing, etc., can solve problems such as lack of information, and achieve the effect of information service optimization
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] In order to better understand the essence of the present invention, the present invention will be further described below in conjunction with specific embodiments and accompanying drawings.
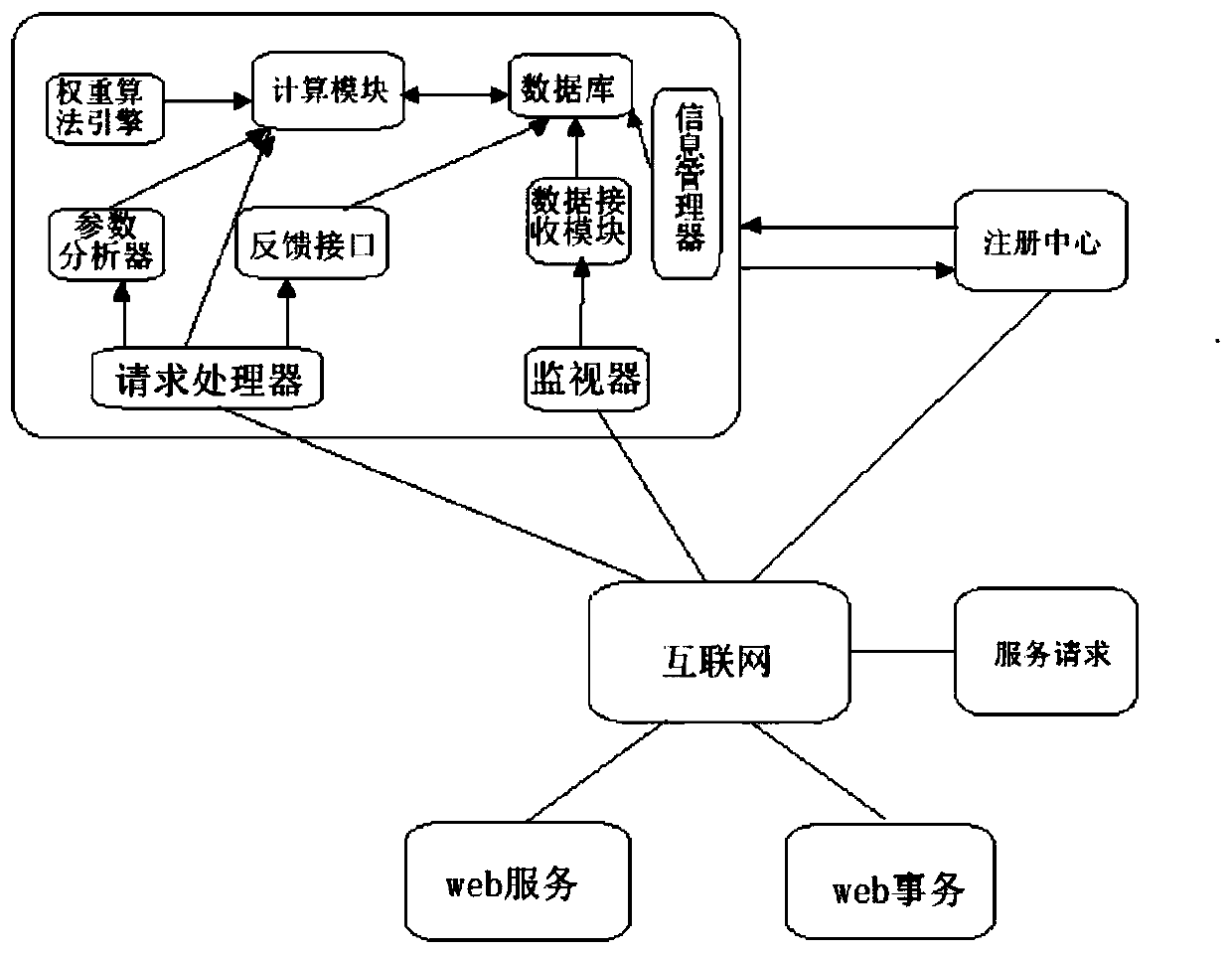
[0019] The present invention is applicable to the field of information system service security evaluation, and the specific steps are as follows: figure 1 as shown,
[0020] Step 1: Use data collection equipment to collect security data during the execution of information system services. Security data is collected using monitors and request handlers.
[0021] The monitor is responsible for monitoring optional services deployed on the network to ensure their accessibility and availability, and dynamically collects information on the actual execution of the services to obtain all attributes related to the network environment, service-specific vulnerabilities on the server side, and application Data such as vulnerabilities on the terminal are the same as those of traditional applic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com