Service access method, device and system, equipment and storage medium
A business access and server system technology, applied in the field of business access, can solve problems such as inability to guarantee accuracy, affecting normal user interests, setting gray list addresses, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
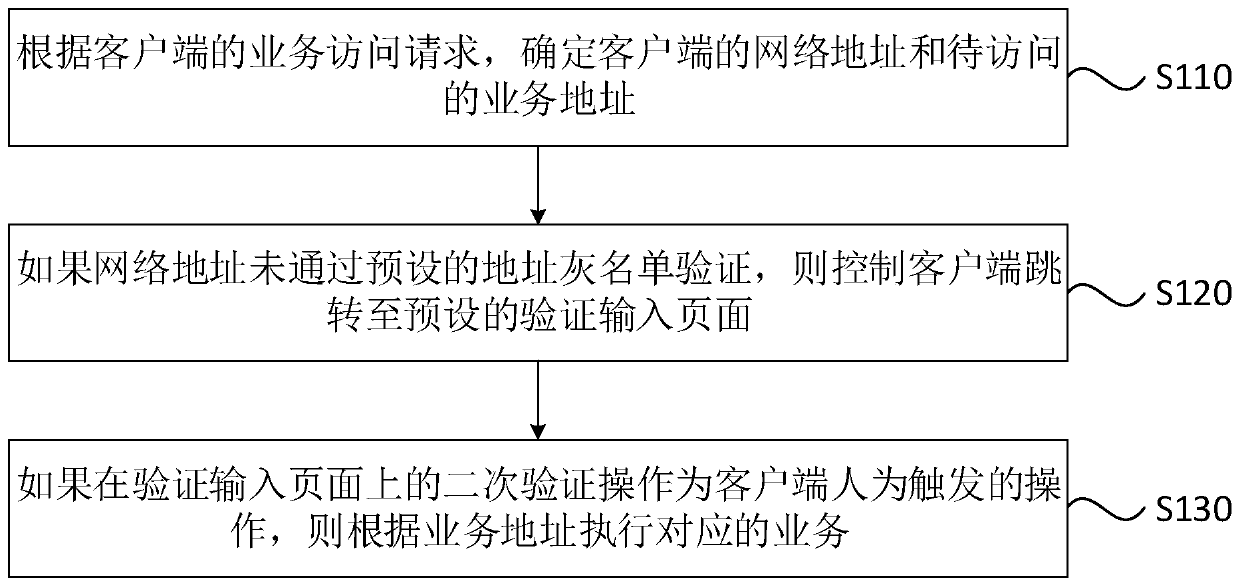
[0036] Figure 1A It is a flow chart of a service access method provided by Embodiment 1 of the present invention. This embodiment can be applied to the situation of accessing services with rights. A service access method provided in this embodiment can be executed by a service access device provided in an embodiment of the present invention, and the device can be realized by means of software and / or hardware, and integrated into a device that executes the method. The device can be any kind of server capable of business processing.
[0037] Specifically, refer to Figure 1A , the method may include the following steps:
[0038] S110. Determine the network address of the client and the address of the service to be accessed according to the service access request of the client.
[0039] Specifically, this embodiment is mainly aimed at accessing specific services developed for various preferential activities. Users can obtain corresponding rewards by accessing the specific servi...
Embodiment 2
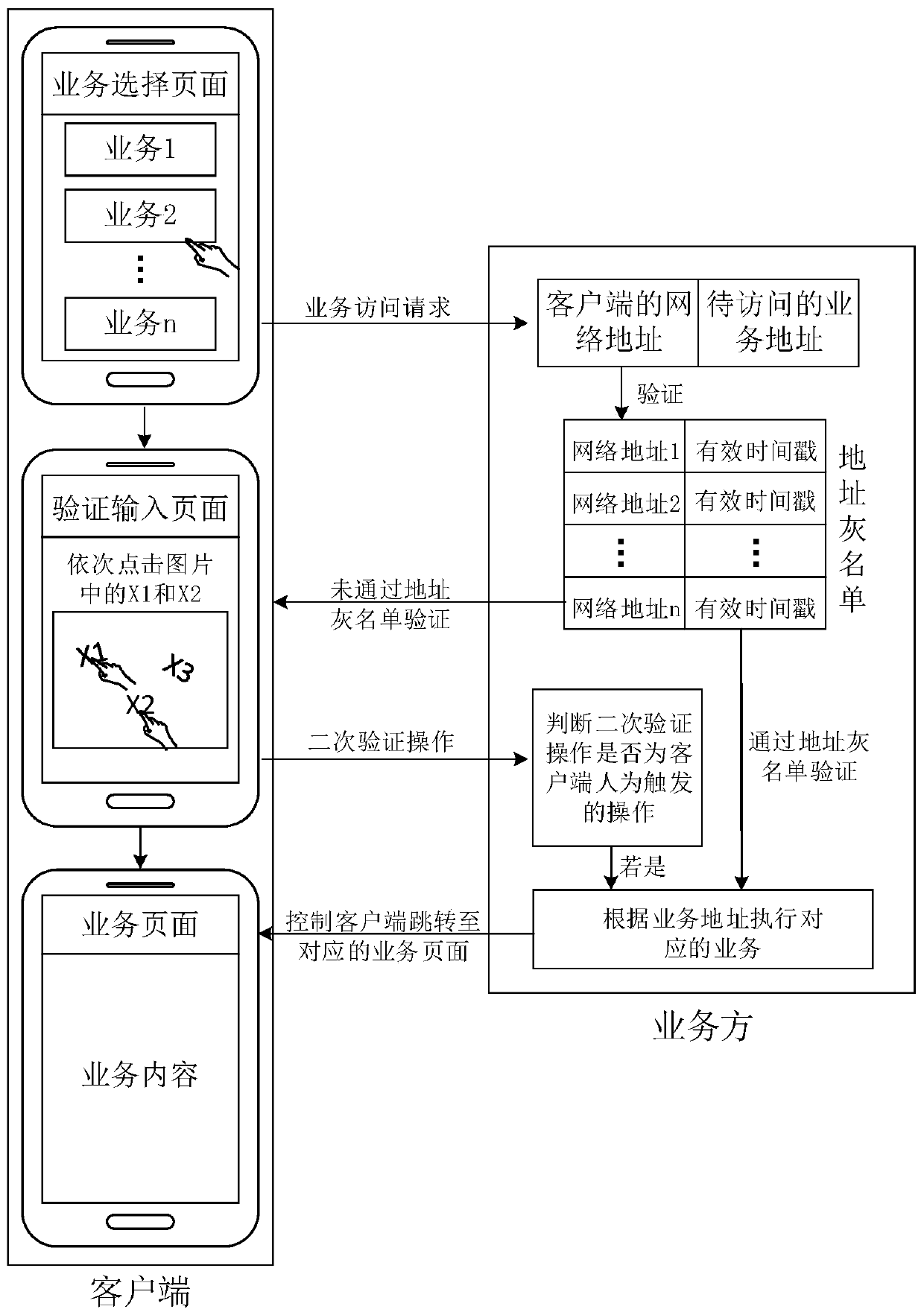
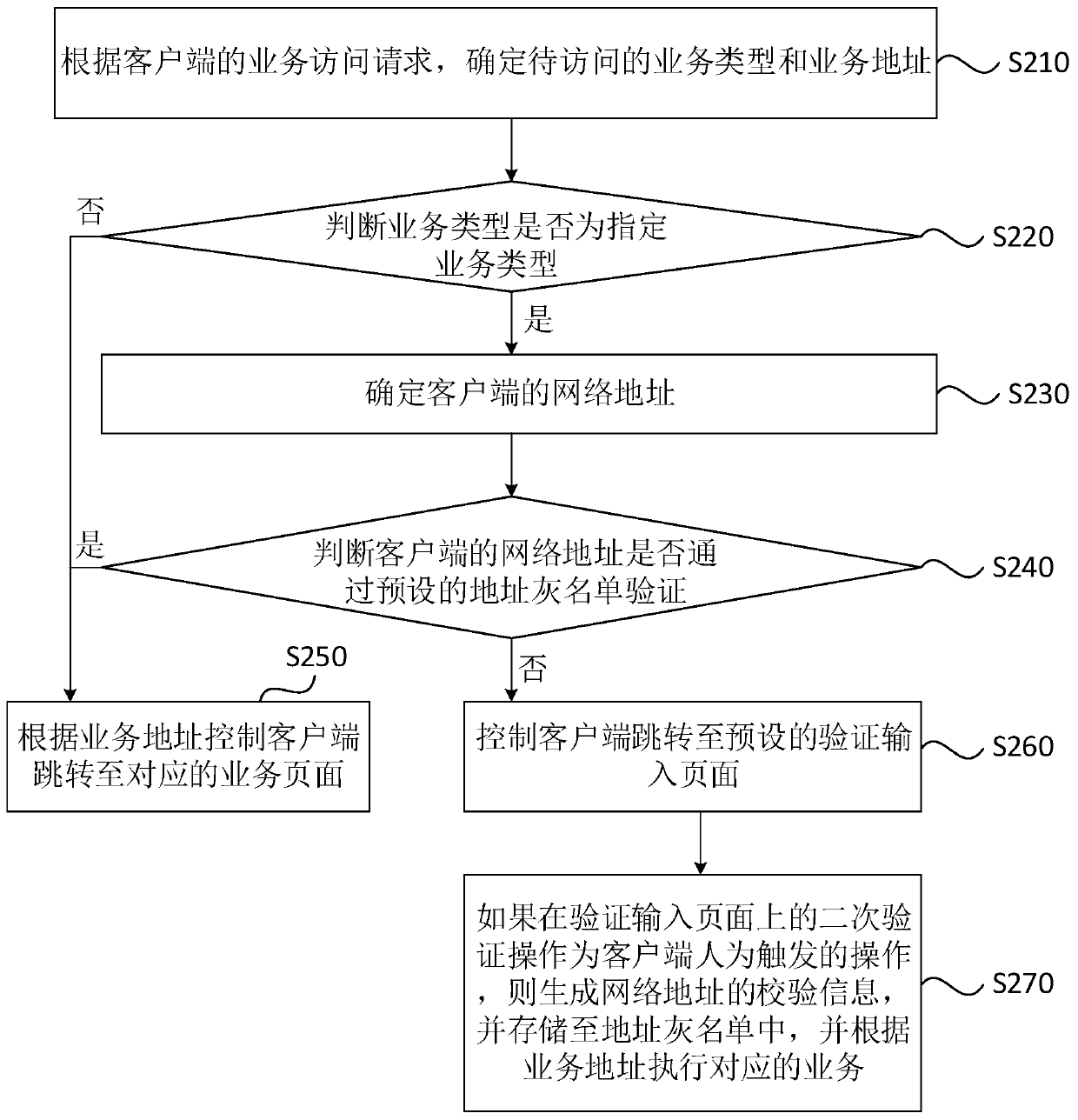
[0056] Figure 2A It is a flow chart of a service access method provided in Embodiment 2 of the present invention, Figure 2B It is a schematic diagram of the principle of the service access process provided by Embodiment 2 of the present invention. This embodiment is optimized on the basis of the foregoing embodiments, and this embodiment mainly describes other situations existing in the service access process.
[0057] optional, such as Figure 2A As shown, this embodiment may include the following steps:
[0058] S210. Determine the service type and service address to be accessed according to the service access request of the client.
[0059] S220, judging whether the service type is a specified service type, if yes, execute S230; if not, execute S250.
[0060] Specifically, the specified service type in this embodiment is a specific service type developed for various preferential activities, and users can obtain corresponding rewards by accessing the specified service....
Embodiment 3
[0074] image 3 A schematic structural diagram of a service access device provided in Embodiment 3 of the present invention, specifically, as image 3 As shown, the device may include:
[0075] Request access module 310, configured to determine the network address of the client and the address of the service to be accessed according to the service access request of the client;
[0076] The verification page jump module 320 is used to control the client to jump to the preset verification input page if the network address does not pass the verification of the preset address gray list;
[0077] The service access module 330 is configured to execute the corresponding service according to the service address if the secondary verification operation on the verification input page is manually triggered by the client.
[0078] In the technical solution provided by this embodiment, first, the network address of the client requesting access is verified through the preset address gray l...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com