Static measurement method of trusted computing platform based on double-system structure
A technology of trusted computing and architecture, applied in the field of network security, can solve problems such as difficult to resist and unable to play, and achieve the effect of improving security performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] Explanation of terms:
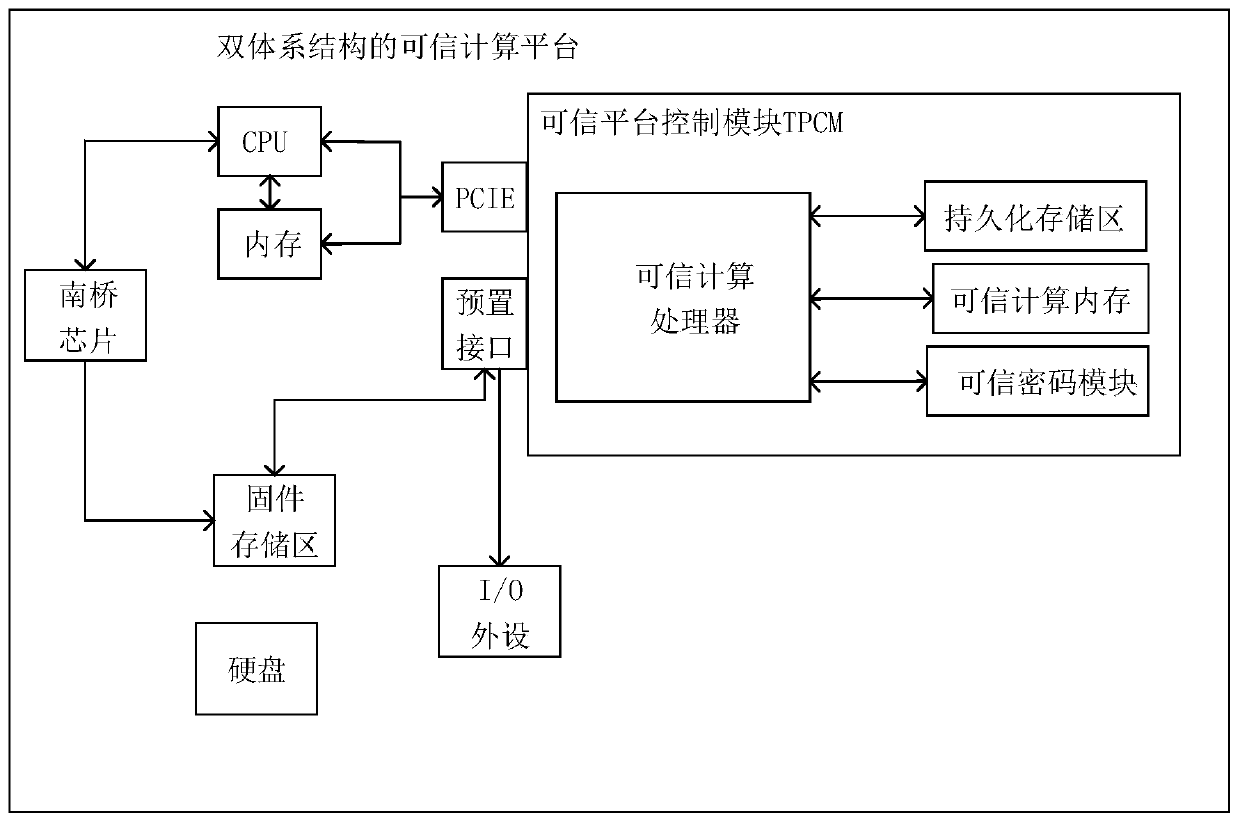
[0039] TCM: Trusted Cryptographic Module, the hardware module of the Trusted Computing Platform, provides cryptographic computing functions for the Trusted Computing Platform, and has a protected storage space.
[0040] TPCM: Trusted Platform Control Module, a hardware core module integrated in a trusted computing platform to establish and guarantee a source of trust, providing integrity measurement, secure storage, trusted reporting, and cryptographic services for trusted computing function, used as a protection subsystem in the present invention.
[0041] TSB: Trusted Software Base, a collection of software elements that provide support for the trustworthiness of trusted computing platforms.
[0042] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
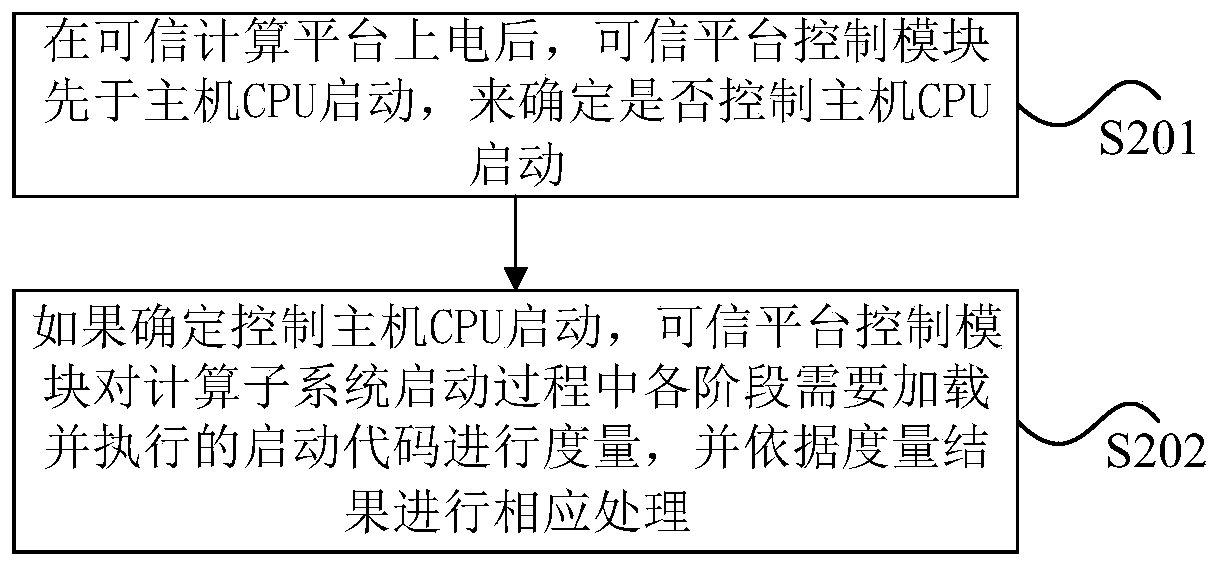
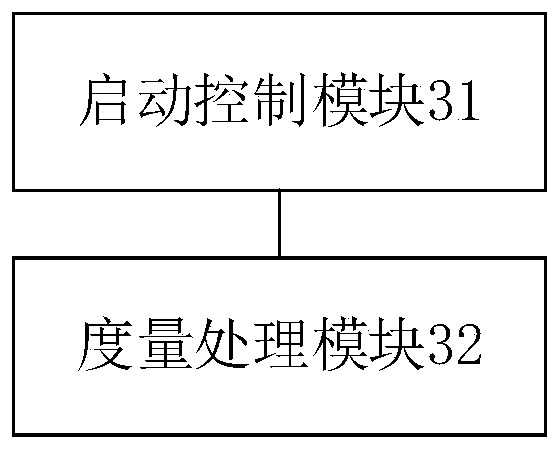
[0043] An embodiment of the present invention provides a static measurement method for a trusted computing platform based on du...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com