Equivalent key acquisition method and device and computer readable storage medium
An acquisition method and key technology, applied in the field of optical cryptography, can solve the problems of limited applicable scenarios, low analysis efficiency and accuracy, and achieve the effect of expanding applicable scenarios and improving efficiency and accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
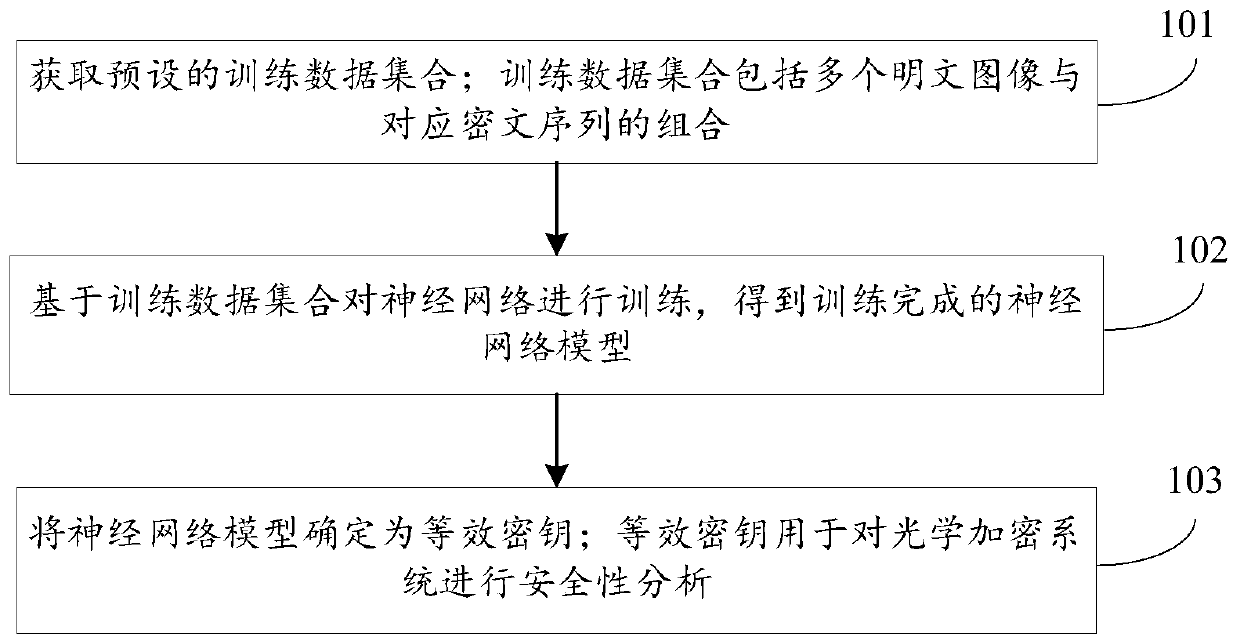
[0028] In order to solve the technical problems in related technologies that rely on the geometric parameters and related structures of the optical encryption system for security analysis of the optical encryption system, the analysis efficiency and accuracy are low, and the applicable scenarios are relatively limited, this embodiment proposes an equivalent The key acquisition method, such as figure 1 Shown is a schematic flow diagram of the basic flow of the equivalent key acquisition method provided in this embodiment. The equivalent key acquisition method proposed in this embodiment includes the following steps:
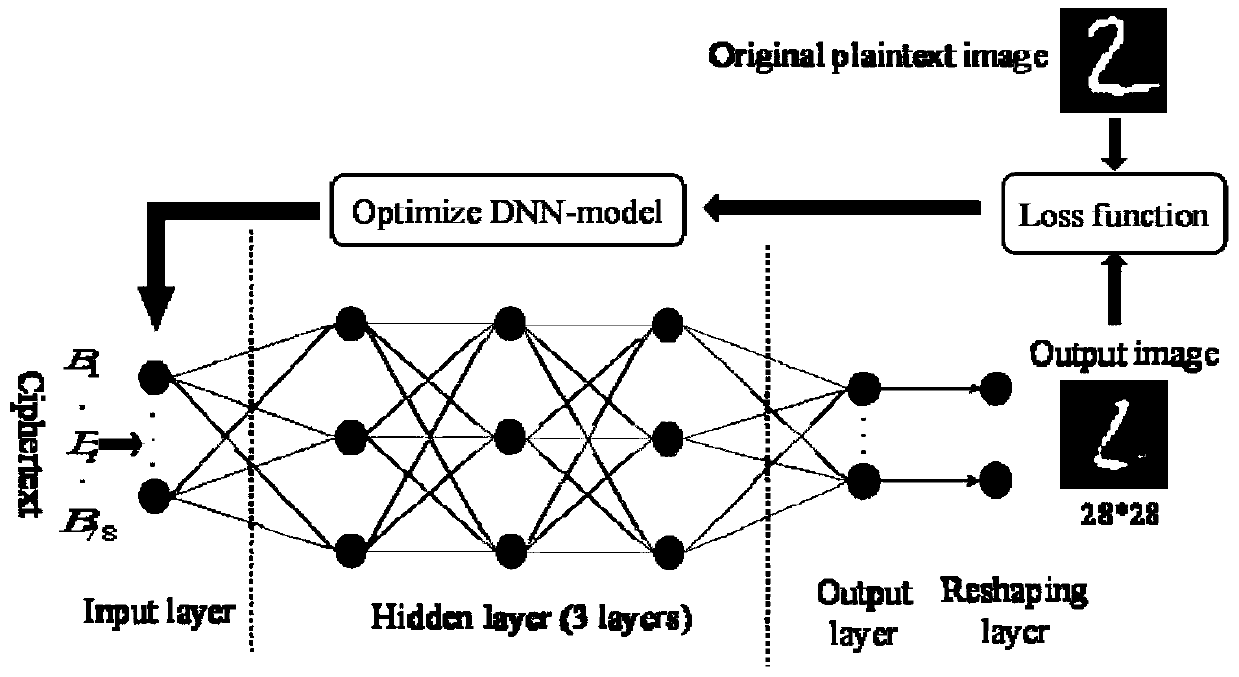
[0029] Step 101. Obtain a preset training data set; the training data set includes a combination of multiple plaintext images and corresponding ciphertext sequences.
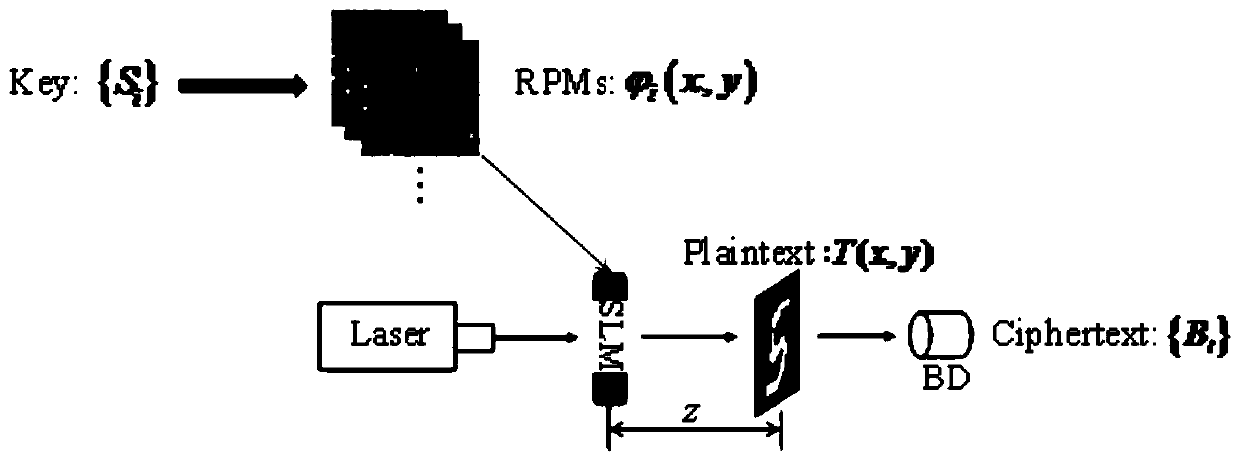
[0030] Specifically, the present invention is based on the Kerckhoffs principle, a basic criterion recognized in the field of cryptanalysis, and adopts a chosen plaintext attack scheme, that is, it ...
no. 2 example
[0055] In order to solve the technical problems in the related art that rely on the geometric parameters and related structures of the optical encryption system for the security analysis of the optical encryption system, the analysis efficiency and accuracy are low, and the applicable scenarios are relatively limited, this embodiment shows an equivalent key acquisition device, see Figure 5 , the equivalent key acquisition device of this embodiment includes:
[0056] The obtaining module 501 is used to obtain a preset training data set; the training data set includes a combination of multiple plaintext images and corresponding ciphertext sequences;
[0057] The training module 502 is used to train the neural network based on the training data set to obtain a trained neural network model;
[0058] The determining module 503 is configured to determine the neural network model as an equivalent key; the equivalent key is used for security analysis of the optical encryption system...
no. 3 example
[0072] This embodiment provides an electronic device, see Figure 6 As shown, it includes a processor 601, a memory 602, and a communication bus 603, wherein: the communication bus 603 is used to realize connection and communication between the processor 601 and the memory 602; the processor 601 is used to execute one or more programs stored in the memory 602 A computer program to implement at least one step in the method for obtaining an equivalent key in the first embodiment above.
[0073] The present embodiment also provides a computer-readable storage medium, which includes information implemented in any method or technology for storing information, such as computer-readable instructions, data structures, computer program modules, or other data. volatile or nonvolatile, removable or non-removable media. Computer-readable storage media include but are not limited to RAM (Random Access Memory, random access memory), ROM (Read-Only Memory, read-only memory), EEPROM (Electri...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com