Trust evaluation device based on subjective logic in edge computing network video processing
A technology of edge computing and network video, applied in the field of computer, can solve the problems that there are not many researches in the field of edge computing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
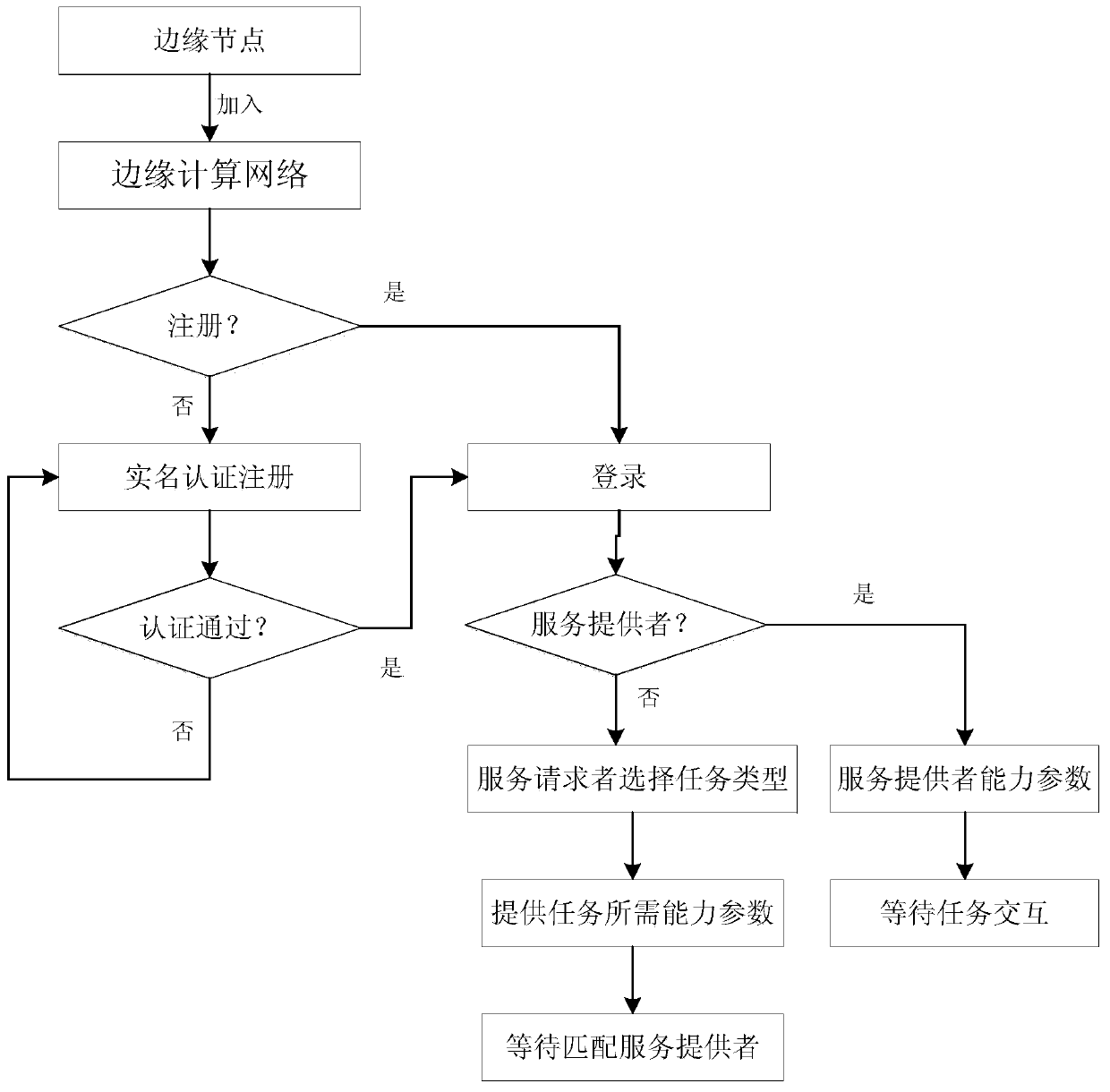
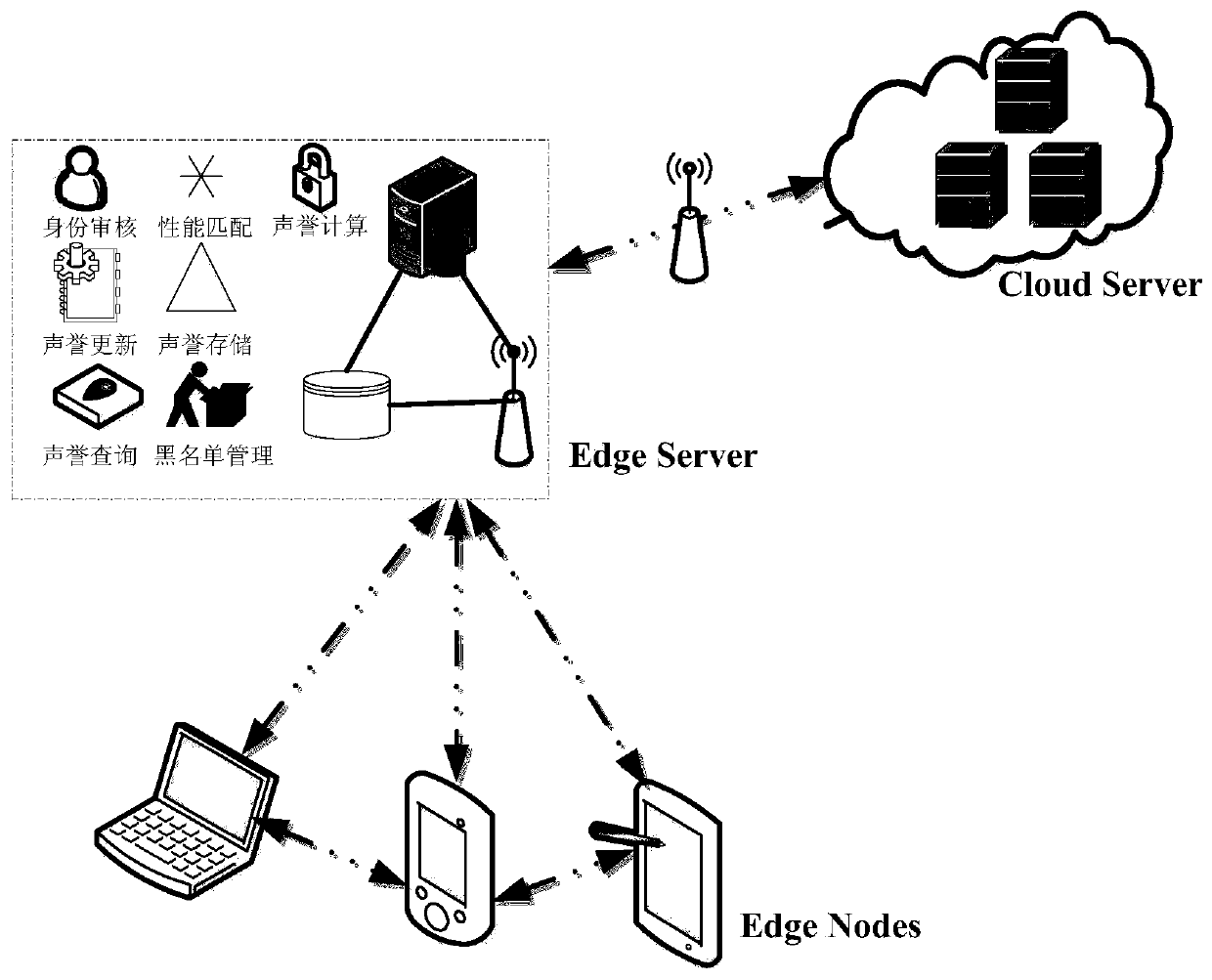
[0072] For a user who requests to join the edge computing network, the user must first be authenticated, and those who meet the requirements can join as a legitimate user, and the newly joined node is assigned an initial reputation value. When a video processing task request is initiated, the edge server first screens out a list of service-providing users that meet the capabilities of the device according to the task's capability requirements (set each task request to have a suitable service-providing node), and randomly Select an end user to interact with. The interaction is completed and the service is updated based on the interaction results based on the behavioral trust mechanism to provide user reputation values. Each region is deployed with a sufficiently powerful and reliable edge server for node identity information verification and storage, node capability matching, reputation value calculation, Storage, update, query and blacklist management. Such as image 3 A tax...
Embodiment 2
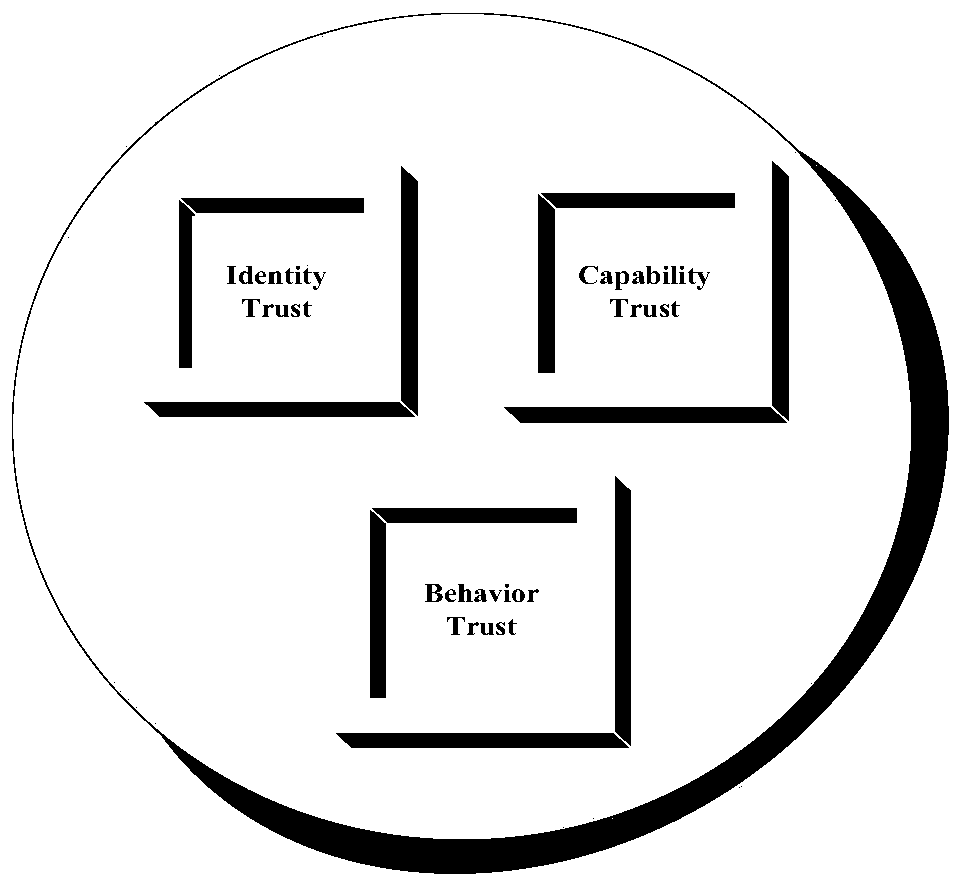
[0134] Such as Figure 5 As shown, this embodiment discloses a trust evaluation device based on subjective logic in edge computing network video processing, including: a trust modeling module, the trust modeling module includes an identity modeling sub-module, a capability modeling sub-module and Behavior modeling sub-module; evaluation module, based on the model established by the trust modeling module, after the interaction is completed, the task request node submits evaluation to the edge server according to the interaction result; update module, the edge server calculates and updates the reputation value of the storage service provider node according to the evaluation result , and notify the service provider node of the updated result.
[0135] Furthermore, the identity modeling sub-module models identity trust, and the specific modeling steps are as follows:
[0136] Only after passing the identity authentication of the trusted central authority (edge server), each edg...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com