Offline identity authentication system and device and computer readable storage medium
An identity authentication and computer program technology, applied in the electronic field, can solve problems such as inconvenient use, easy guessing or brute force cracking of user passwords
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
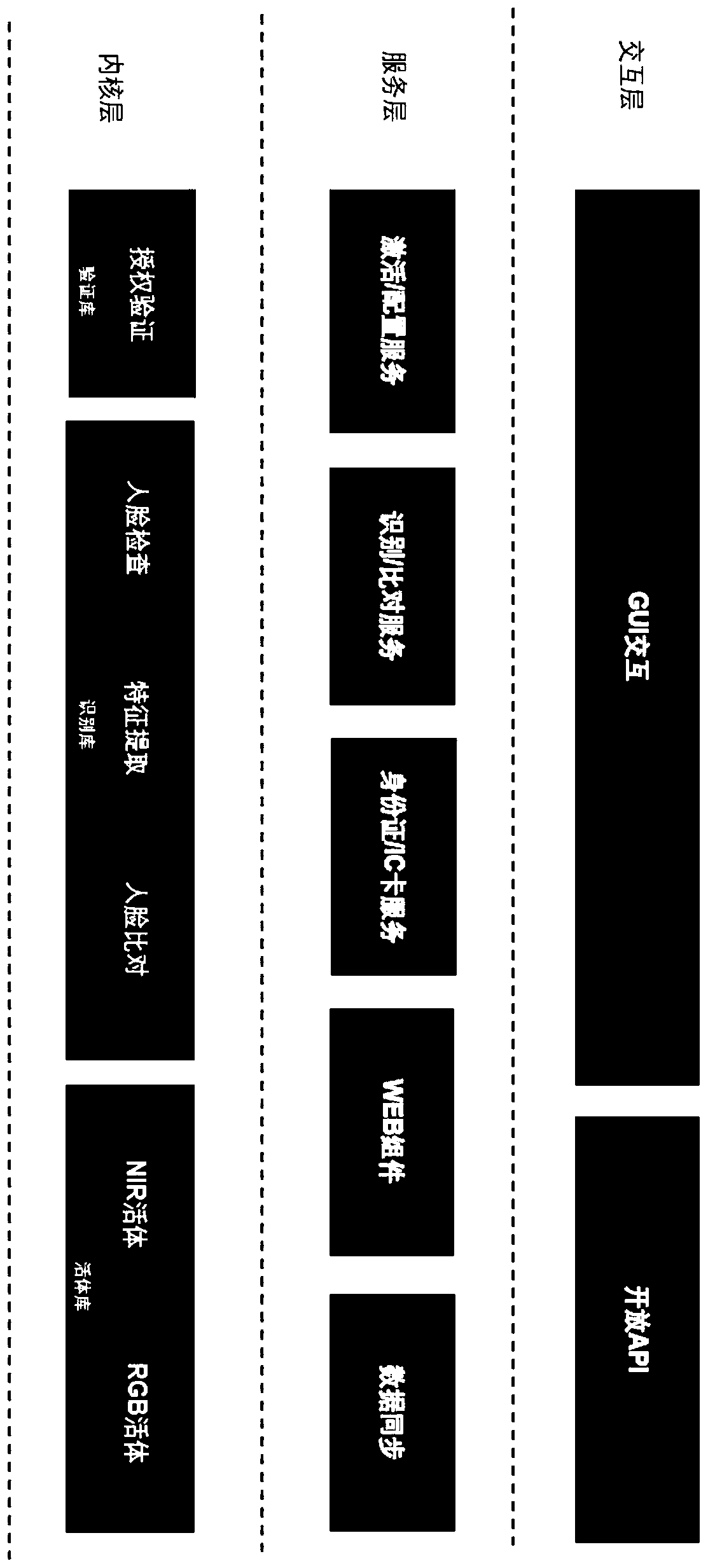
[0039] figure 1 is the first block diagram of the offline identity authentication system of the present invention. An offline identity authentication system, the system includes an interaction layer 10, a service layer 20 and a kernel layer 30, wherein:
[0040] The interactive layer 10 is used to provide an interactive interface, and receive interactive operations acquired by the interactive interface;
[0041] The service layer 20 is used to package business functions into corresponding services, wherein the business functions include preloading the feature data set of the admitted personnel locally, performing feature extraction and feature comparison operations in real time in an offline state, and at the same time , performing a verification and identification operation on the target object in the offline state;
[0042] The kernel layer 30 is used to perform operations and logical task processing.
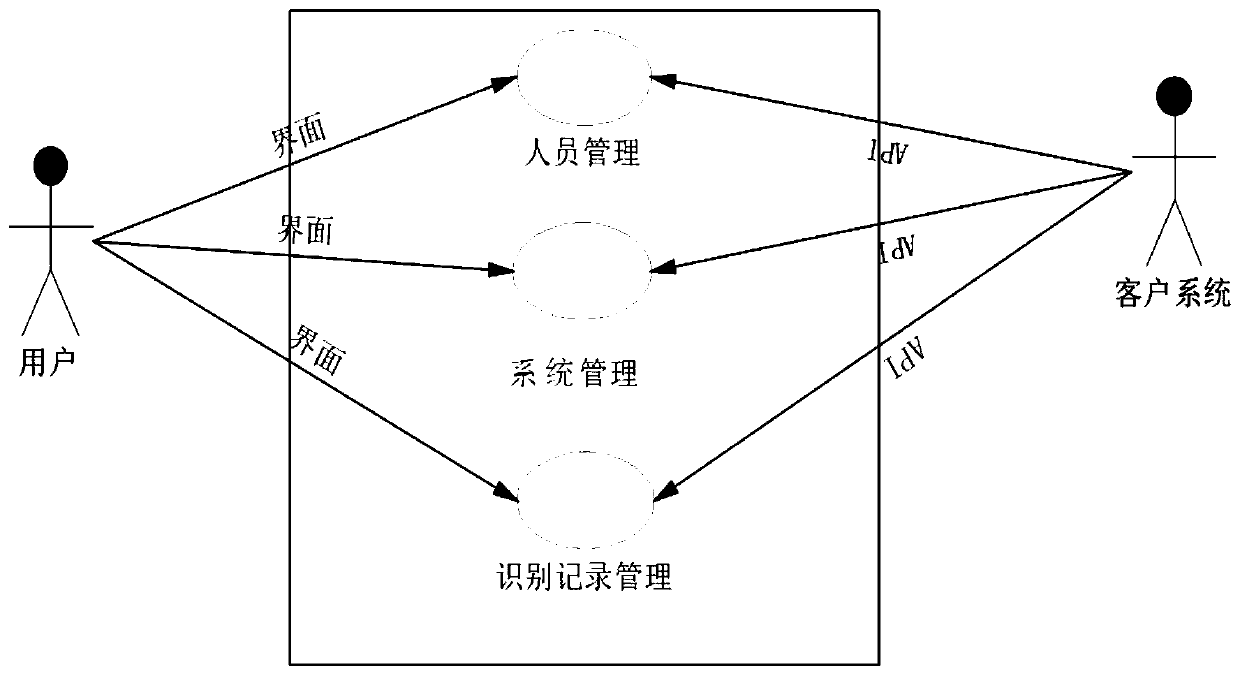
[0043] Optionally, the system further includes a personnel management...
Embodiment 2
[0069] Based on the above embodiments, the present invention also proposes an offline identity authentication device, which includes a memory, a processor, and a computer program stored in the memory and operable on the processor, the computer program being executed by the When the processor executes, it achieves:
[0070] The interactive layer is used to provide an interactive interface, and receive interactive operations acquired by the interactive interface;
[0071] The service layer is used to package business functions into corresponding services, wherein the business functions include preloading the feature data set of the admitted personnel locally, performing feature extraction and feature comparison operations in real time in an offline state, and at the same time, performing a verification and identification operation on the target object in the offline state;
[0072] The kernel layer is used to perform calculation and logic task processing.
[0073] Optionally, ...
Embodiment 3
[0080] Based on the above-mentioned embodiments, the present invention also proposes a computer-readable storage medium, on which an identity authentication program is stored, and when the identity authentication program is executed by a processor, it realizes:
[0081] The interactive layer is used to provide an interactive interface, and receive interactive operations acquired by the interactive interface;
[0082] The service layer is used to package business functions into corresponding services, wherein the business functions include preloading the feature data set of the admitted personnel locally, performing feature extraction and feature comparison operations in real time in an offline state, and at the same time, performing a verification and identification operation on the target object in the offline state;
[0083] The kernel layer is used to perform calculation and logic task processing.
[0084]It can be understood that the computer-readable storage medium propo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com