Copyright information identification system and method
A technology for copyright information and identification system, which is applied in the field of information processing and can solve problems such as security problems and single verification methods.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
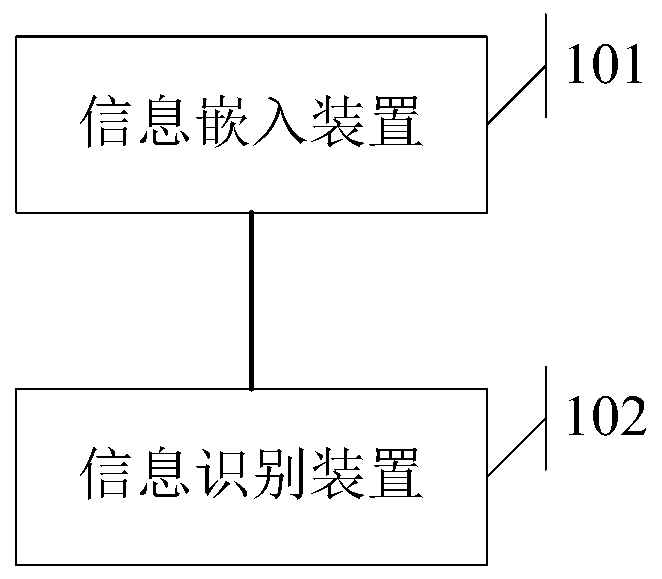
[0045] Such as figure 1 Shown is a schematic structural diagram of a copyright information identification system in an embodiment of the present invention, and the system includes: an information embedding device 101 and an information identification device 102 .
[0046] The information embedding device 101 is used to obtain the design file, read out the security information that needs to be added from the database, and embed the security information into the design file to obtain a brand new design file;
[0047] The information identification device 102 is configured to monitor the information uploaded by the terminal through the communication port, extract image information from the uploaded information, match and compare the amplitude part in the image information with the preset amplitude part, and compare the amplitude part with the preset amplitude part. When the partial difference of the preset amplitude satisfies a condition, sending response information to the termi...
Embodiment 2
[0082] figure 2 It is a flow chart of a method for identifying copyright information in an embodiment of the present invention, and the method includes:
[0083] S1, extracting the image part that needs to embed security information in the design file, as the first embedded original image;
[0084] S2. Perform Fourier transform on the first embedded original image to obtain an amplitude part corresponding to the first embedded original image;
[0085] S3. Read security information from the database, and embed the security information into the first embedded original image;
[0086] S4. Perform inverse Fourier transform on the first embedded original image embedded with security information to obtain a second embedded original image;
[0087] S5. Replace the second original embedded image with the first original embedded image.
[0088] For example, the process of embedding security information in a design file is as follows:
[0089] 1. From the design file of the printed...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com