Illegal request identification method and device and electronic equipment
An identification method and illegal technology, applied in the computer field, can solve the problem of low identification accuracy of illegal requests, and achieve the effect of improving the accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
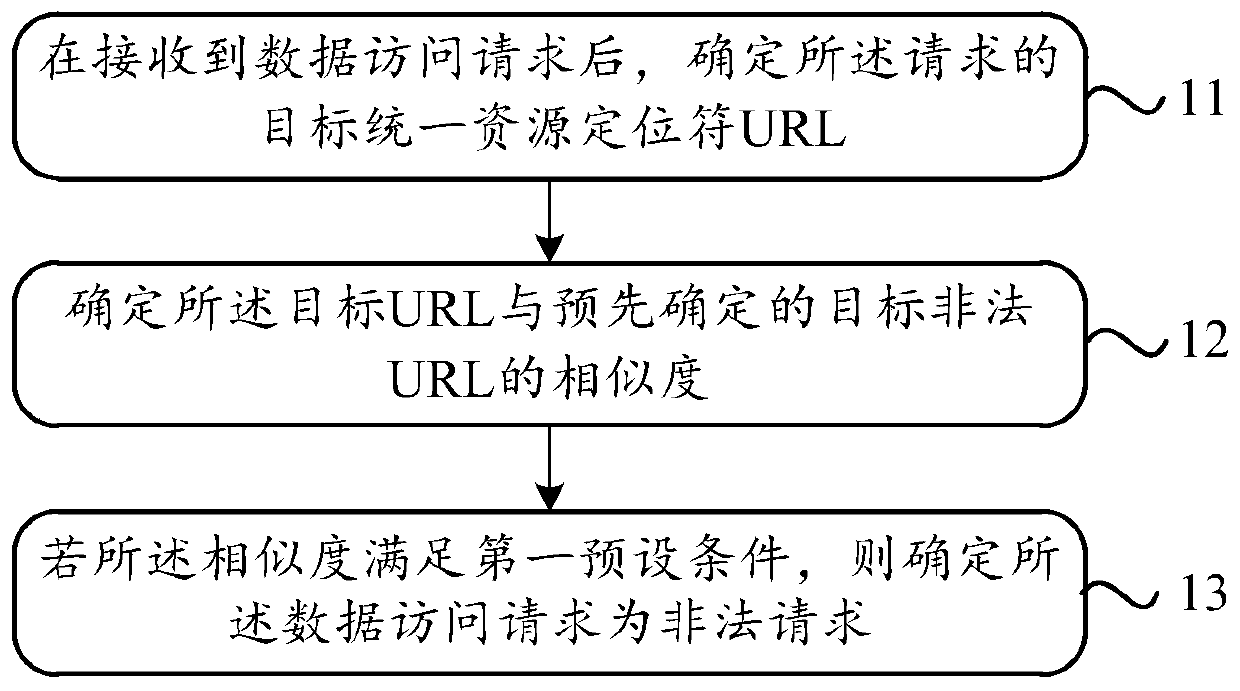
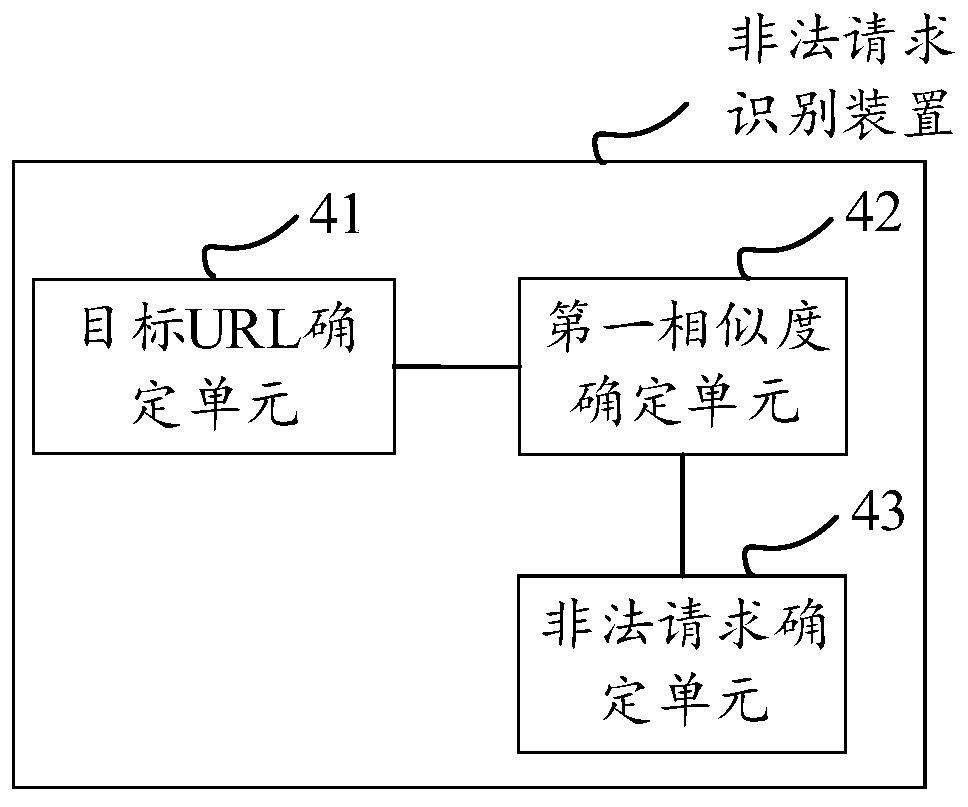
[0069] Determine the target similarity that satisfies the third preset condition among the similarities among the illegal URLs; use the illegal URL corresponding to the target similarity as the target illegal URL. Since the target similarity is calculated from two illegal URLs, the illegal URLs corresponding to the target similarity are the two illegal URLs from which the target similarity is calculated.
[0070] The third preset condition includes at least one of the following:
[0071] The similarity is greater than the set similarity threshold, which can be set according to manual experience, for example, it can be 90%;
[0072] The order of the similarity in the similarity sorting is higher than the second preset order, and the similarity sorting is a sorting in descending order of the similarity.
[0073] The similarities between illegal URLs can be calculated in pairs to obtain multiple similarities, and then sort the obtained similarities. For example, if the second pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com