A low-speed denial of service attack detection method based on an SNN-LOF algorithm
A denial of service attack and detection method technology, applied in computing, computer parts, instruments, etc., can solve problems such as low practicability, high resource consumption, and low accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
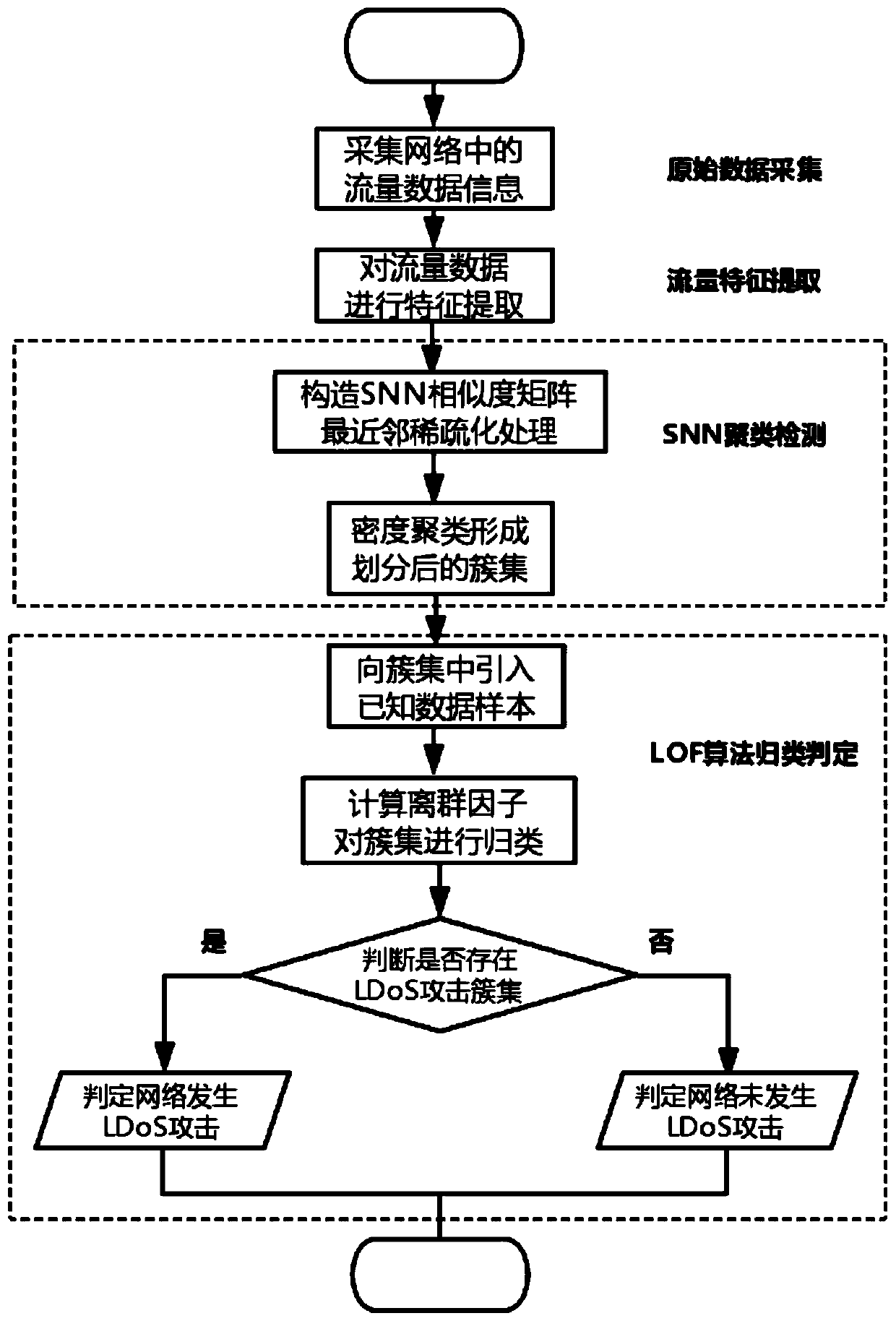
[0023] The present invention will be further described below in conjunction with the accompanying drawings.
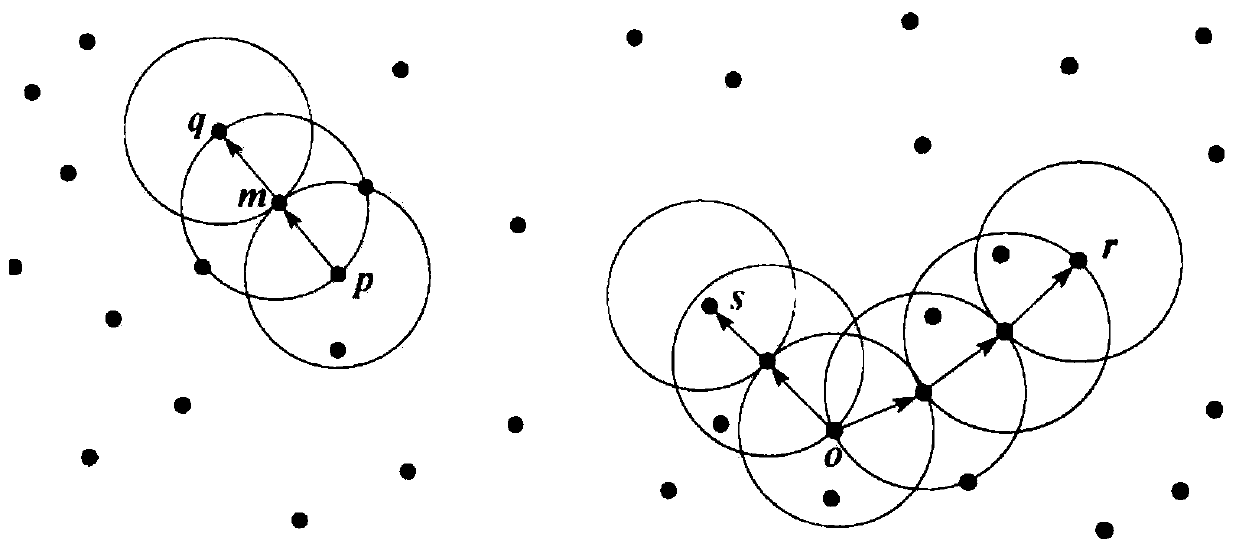
[0024] figure 1 It is a schematic diagram of the density clustering algorithm process. The clustering algorithm is mainly to extract an unprocessed sample point from the data sample. If the extracted sample point is a core point, then find all the objects that are reachable from the point density to form a cluster, otherwise the extracted sample point is the boundary point, and then continue to extract the next unprocessed sample point until all sample points have been traversed, and the detection samples are clustered into several clusters.
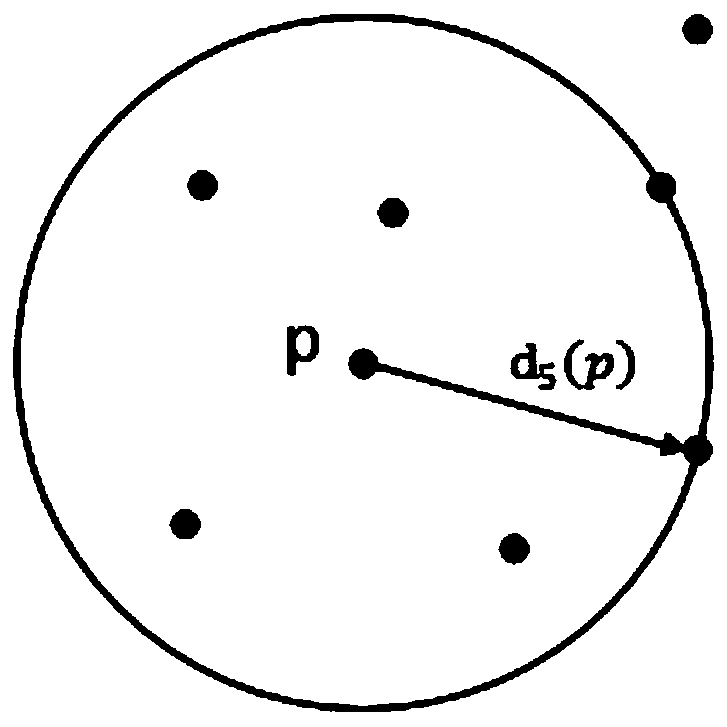
[0025] figure 2 is the schematic diagram of the fifth distance of the data sample point p. The k-th reachable distance of the data sample point refers to the distance or the actual distance from at least the k-th farthest sample point. According to the reachable distance between each sample point, the local reachable density ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com