Computer information security system
An information security system and computer technology, applied in the field of computer information security systems, can solve problems such as information loss, and achieve the effects of improving security, preventing viruses, and improving operational comfort.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
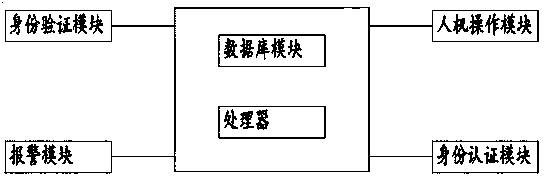
[0026] see Figure 1~2 , in Embodiment 1 of the present invention, a computer information security system includes:
[0027] The man-machine operation module is used for user registration, and collects and generates biometric data corresponding to the user registration identity, and saves the biometric data in the user registration database; it is used for inputting information access requests and data modification requests and modifications Operation; for making an input requiring storage of data and sending the entered data to the processor; for entering biometric data and sending the data to the processor.
[0028] The identity authentication module is used to compare the received biometric data with the biometric data in the user registration database, and send the comparison result to the processor.
[0029] The identity verification module intermittently sends requests to the processor to verify the identity of the operator; this setting ensures that the operator is a l...
Embodiment 2
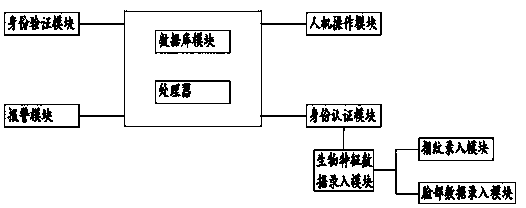
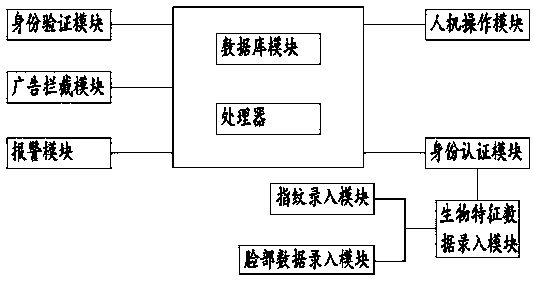
[0039] see image 3 , the main difference between Embodiment 2 and Embodiment 1 is that a computer information security system also includes:
[0040] The advertisement blocking module is used to block advertisements, improve user's operating comfort, prevent advertisements from containing viruses, and improve system security.
[0041] The working principle of the present invention is:
[0042] Through the identity verification module, intermittently send a request to the processor to verify the identity of the operator, and the processor sends a biometric data verification instruction to the identity verification module according to the request, collects the biometric data of the operator, and compares the data with the database. Compare the data stored in the computer and send the result to the processor. When the verification result is that the logged-in user and the operator are the same person, no instruction is given. If the operator is inconsistent with the logged-in u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com