Node and user interactive authentication method and system in blockchain network mode
A network mode, interactive authentication technology, applied in the field of node and user interactive authentication, can solve the problems that the technology cannot be widely popularized and applied, and the block node calculation amount and storage capacity are higher.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
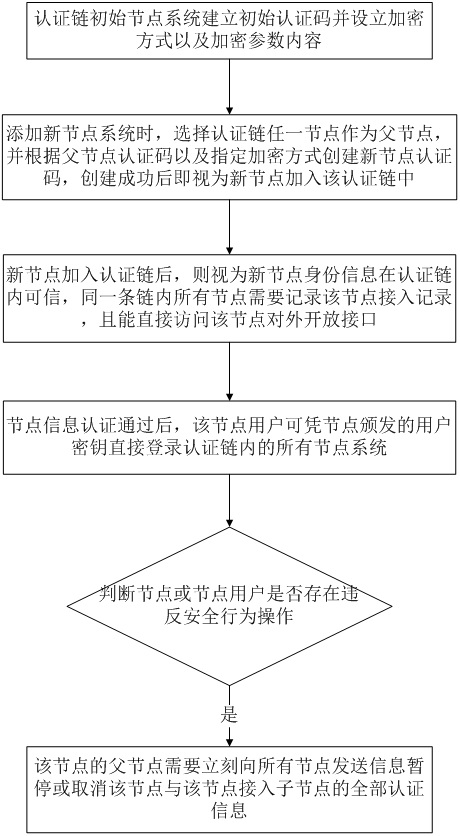
[0037] as attached figure 1 As shown, the node and user interactive authentication method under the block chain network mode of the present invention, the method steps are as follows:
[0038] S1. The initial node system of the authentication chain establishes the initial authentication code and sets up the encryption method and encryption parameter content; the encryption parameter content includes time, node name or address; the initial authentication code is the information starting point of the entire authentication chain; the initial node is a system or a dedicated Authentication service; the initial node needs to establish a basic user information access interface, that is, to ensure that users can access relevant user information stored on other nodes after logging in at any node, so as to realize the security and efficiency of the authentication chain.
[0039] S2. When adding a new node system, select any node in the authentication chain as the parent node, and create...
Embodiment 2
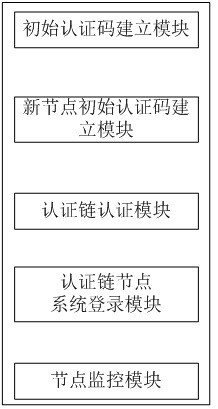
[0045] as attached figure 2 As shown, the node and user interactive authentication system in the blockchain network mode of the present invention includes an initial authentication code establishment module, a new node initial authentication code establishment module, an authentication chain authentication module, an authentication chain node system login module and Node monitoring module. The initial authentication code establishment module is used to establish the initial authentication code of the initial node system of the authentication chain and establishes the encryption method and encryption parameter content of the initial node of the initial authentication chain; the new node initial authentication code establishment module is used for the establishment of the initial authentication code of the new node. When adding a new node system, select any node in the authentication chain as the parent node, and create a new node authentication code according to the parent nod...
Embodiment 3
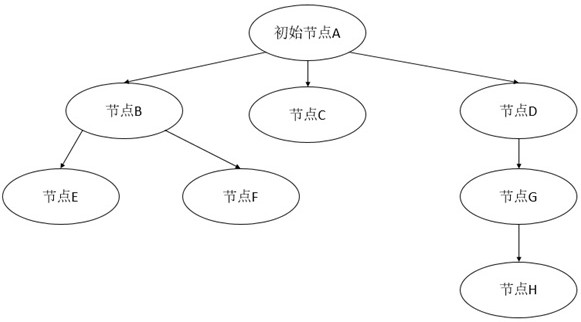
[0047] as attached image 3 As shown, taking A, B, C, D, E, F, G and H as examples:
[0048] (1), the initial node establishes the initial authentication code and sets up the encryption method;
[0049] (2), A allows nodes B, C, and D to access the authentication chain, and builds a basic information interface. At the same time, the node can create a special data interface to provide access within the chain and add other restrictions such as permissions;
[0050] (3) Node B allows E and F to access the authentication chain, D allows G to access the authentication chain, and G allows H to access the authentication chain;
[0051] (4) If node G has malicious behavior, node D needs to notify all nodes except G and all child nodes (H nodes) of G to suspend the authentication behavior of all nodes under the node tree until it is repaired and resumes authentication.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com