An instruction-based data security protection system
A data security and protection system technology, applied in the direction of internal/peripheral computer component protection, etc., can solve the problems that have not been seen in public reports, and achieve the effect of preventing equipment design data leakage and protecting data security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The present invention is further described below.
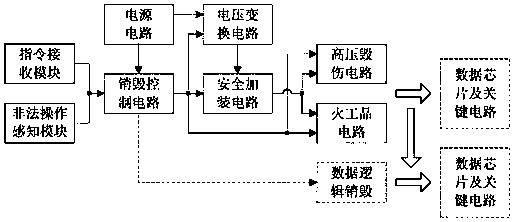
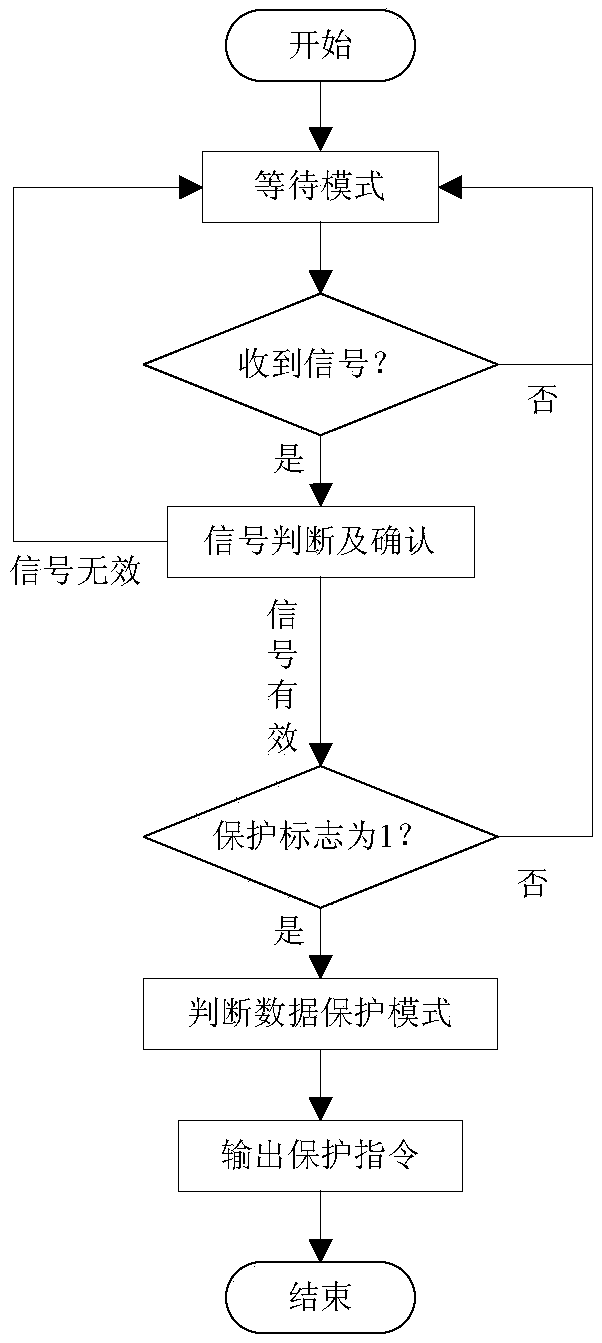
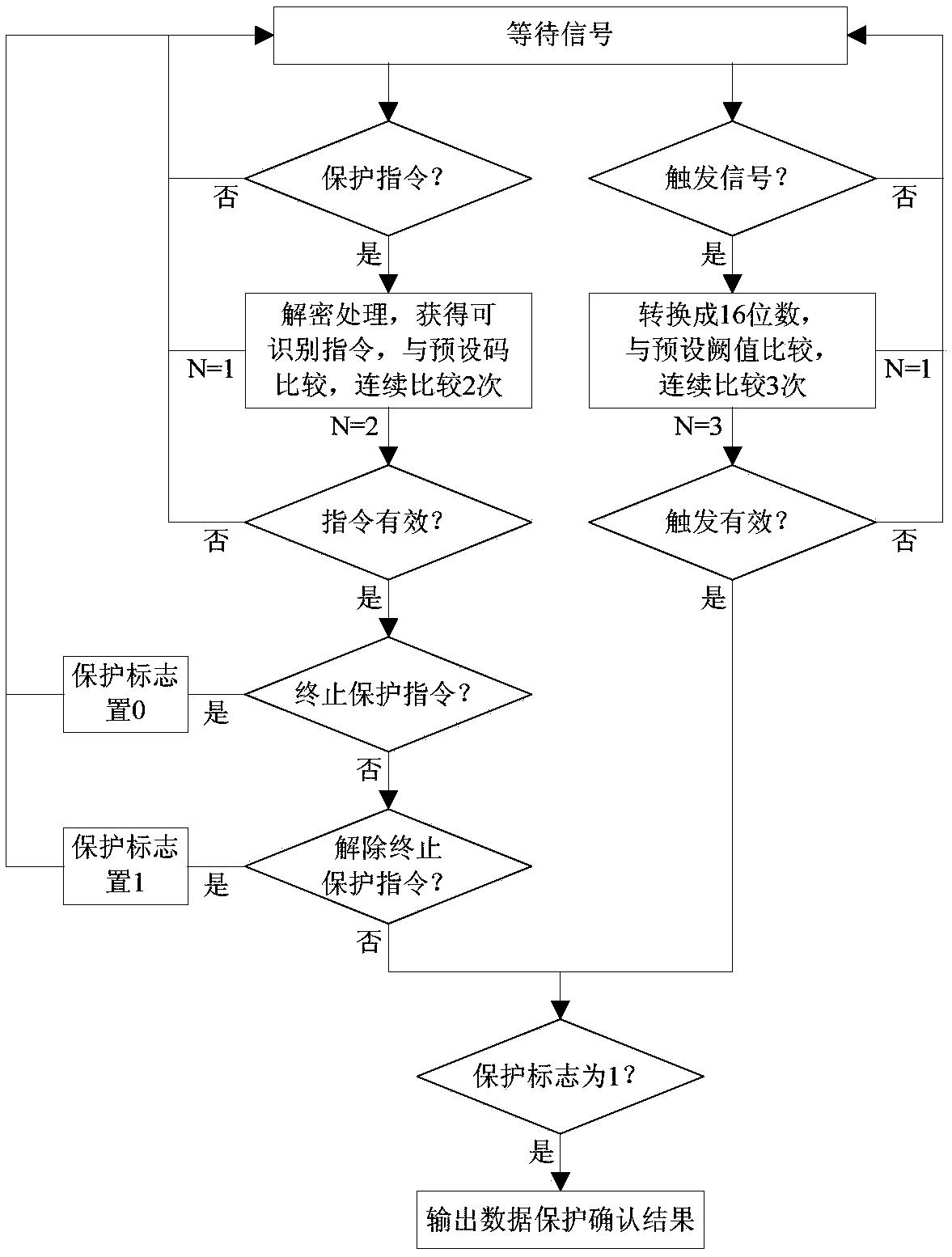
[0038] A data security protection system based on instructions. According to the functions and characteristics of the chip where the data resides and its circuit board in the device, different data security protection modes are set, and the conditional self-triggering or command destruction mode is set. The criterion for data destruction conditions is valid After that, the data can be overwritten or block deleted in logical ways, and the data can be quickly and safely protected at the software level, or the high-voltage pulse voltage can be generated by destroying the control circuit and the voltage conversion circuit to break down and burn down or control the blowing up of small pyrotechnics Or complexly destroy the chip and core circuit where the data is located, and irreversibly physically destroy it at the hardware level, so that the data can be quickly and thoroughly protected, and solve the problem of rapidity, th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com