Verification method and device based on IEEE 1588 protocol
A verification method and protocol technology, applied in the field of verification methods and devices based on the IEEE1588 protocol, can solve problems such as difficult clock node control and difficult verification of time synchronization, and achieve the effect of simplifying verification steps and optimizing verification results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
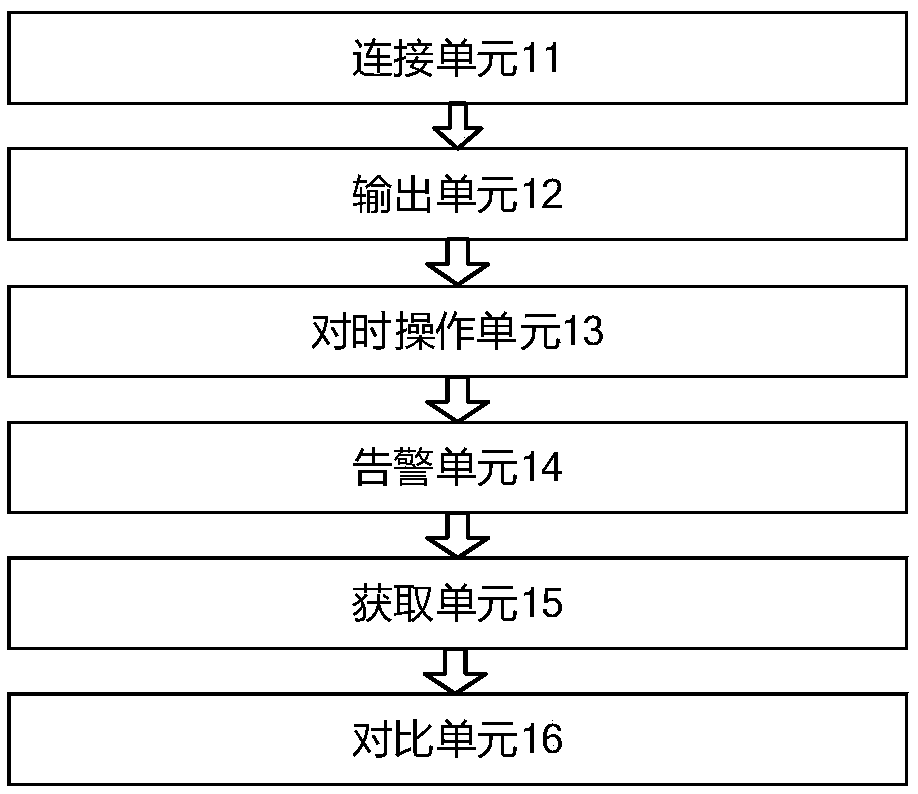
Image
Examples
Embodiment Construction
[0024] The technical solution of the present invention is clearly and completely described below in conjunction with the accompanying drawings.
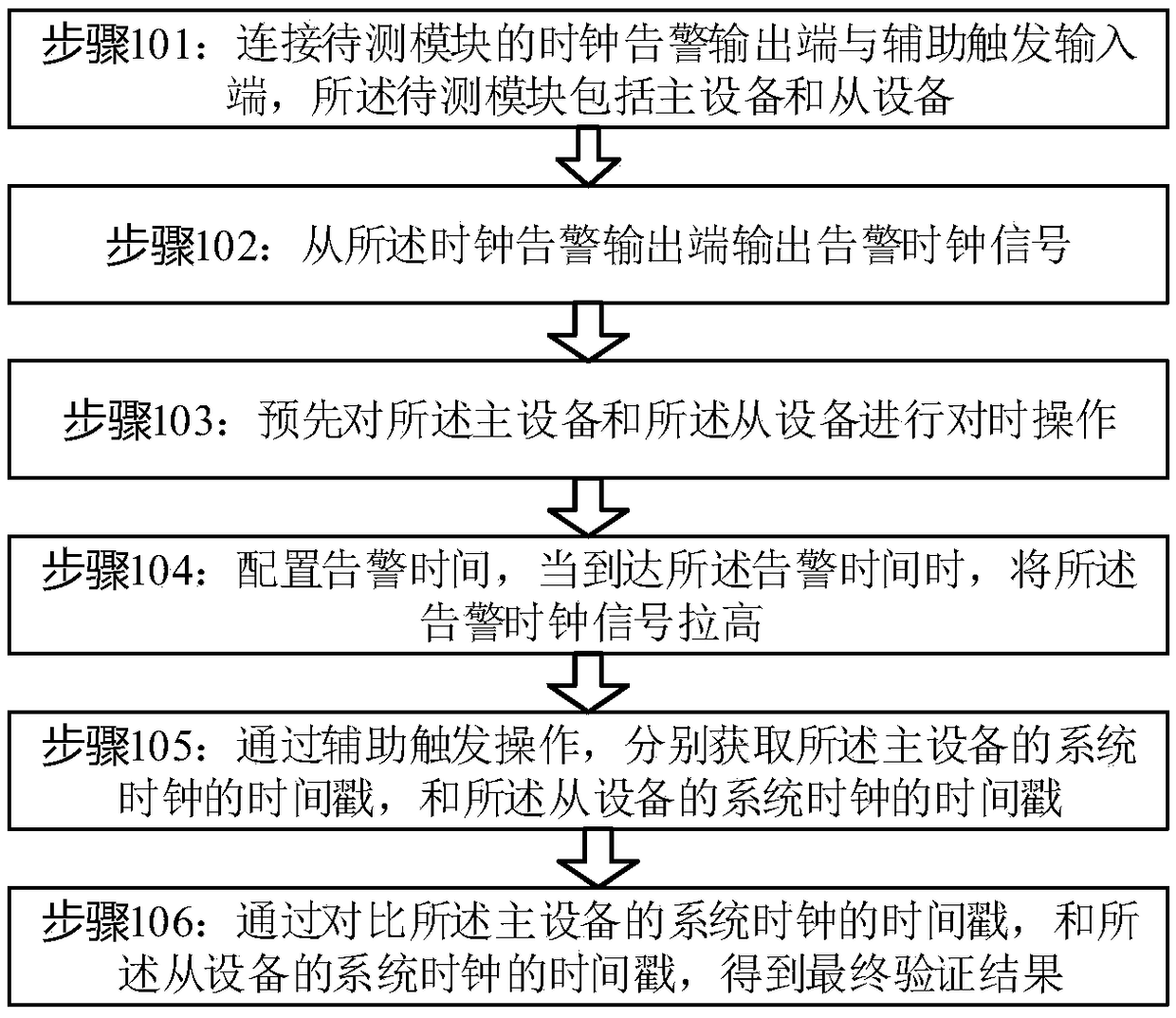
[0025] Such as figure 1 As shown, the embodiment of the present invention provides a kind of verification method based on IEEE 1588 agreement, and described method comprises:
[0026] Step 101: Connect the clock alarm output terminal and the auxiliary trigger input terminal of the module under test, the module under test includes a master device and a slave device;
[0027] It should be noted that the clock alarm output terminals of the master device and the slave device are respectively interconnected with their corresponding auxiliary trigger input terminals.
[0028] Step 102: Outputting an alarm clock signal from the clock alarm output terminal;
[0029] Step 103: performing a time synchronization operation on the master device and the slave device in advance;
[0030] Specifically, based on the 1588 protocol, the time synchro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com