Illegal external-connection detection method and device, equipment and storage medium
An outreach detection and illegal technology, applied in the direction of electrical components, transmission systems, etc., can solve the problems of false positives as attacks, occupying intranet bandwidth, affecting the intranet network environment and normal business operation of the intranet, etc., to reduce the impact, Avoid contract sending and traffic occupation, and improve the effect of intranet security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] In order to enable those skilled in the art to better understand the solution of the present invention, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments. Apparently, the described embodiments are only some of the embodiments of the present invention, but not all of them. Based on the embodiments of the present invention, all other embodiments obtained by persons of ordinary skill in the art without making creative efforts belong to the protection scope of the present invention.
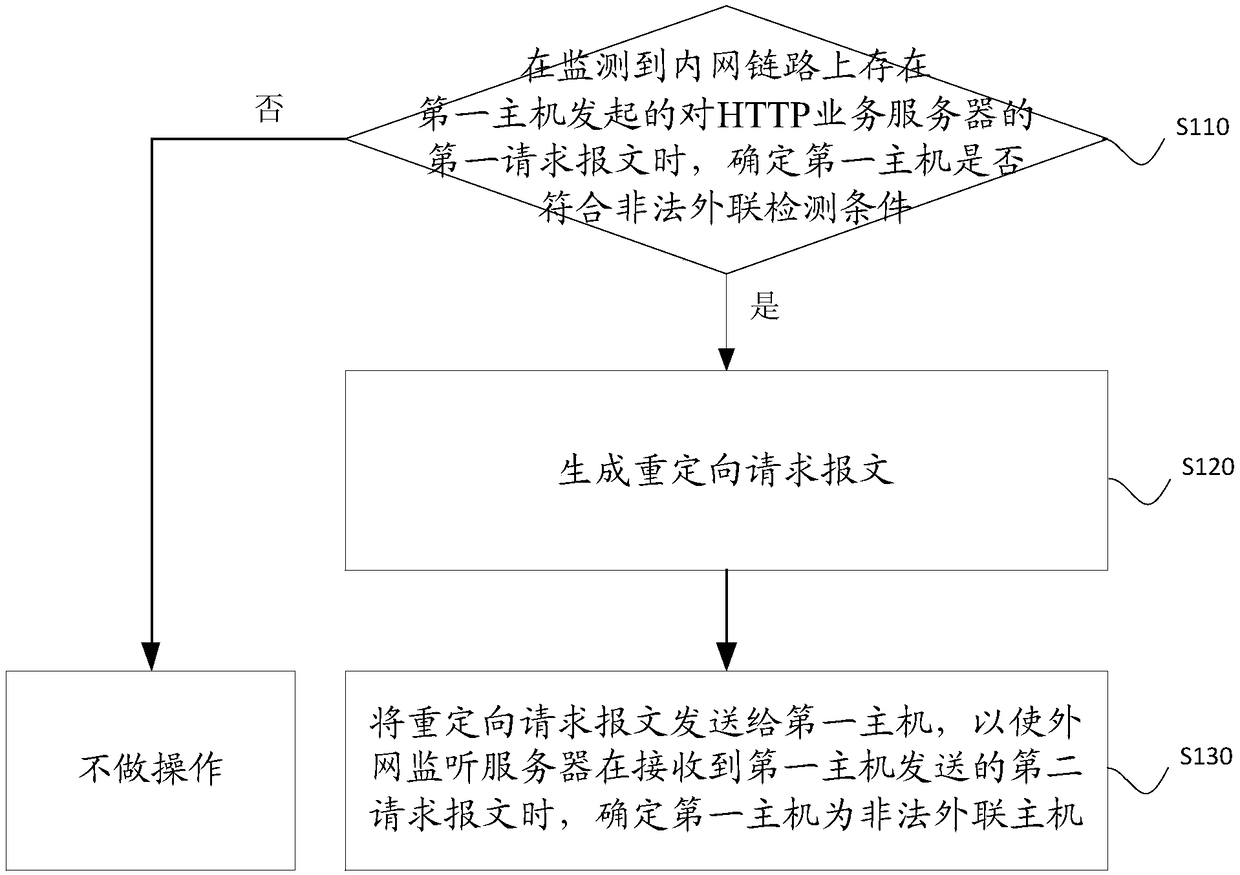
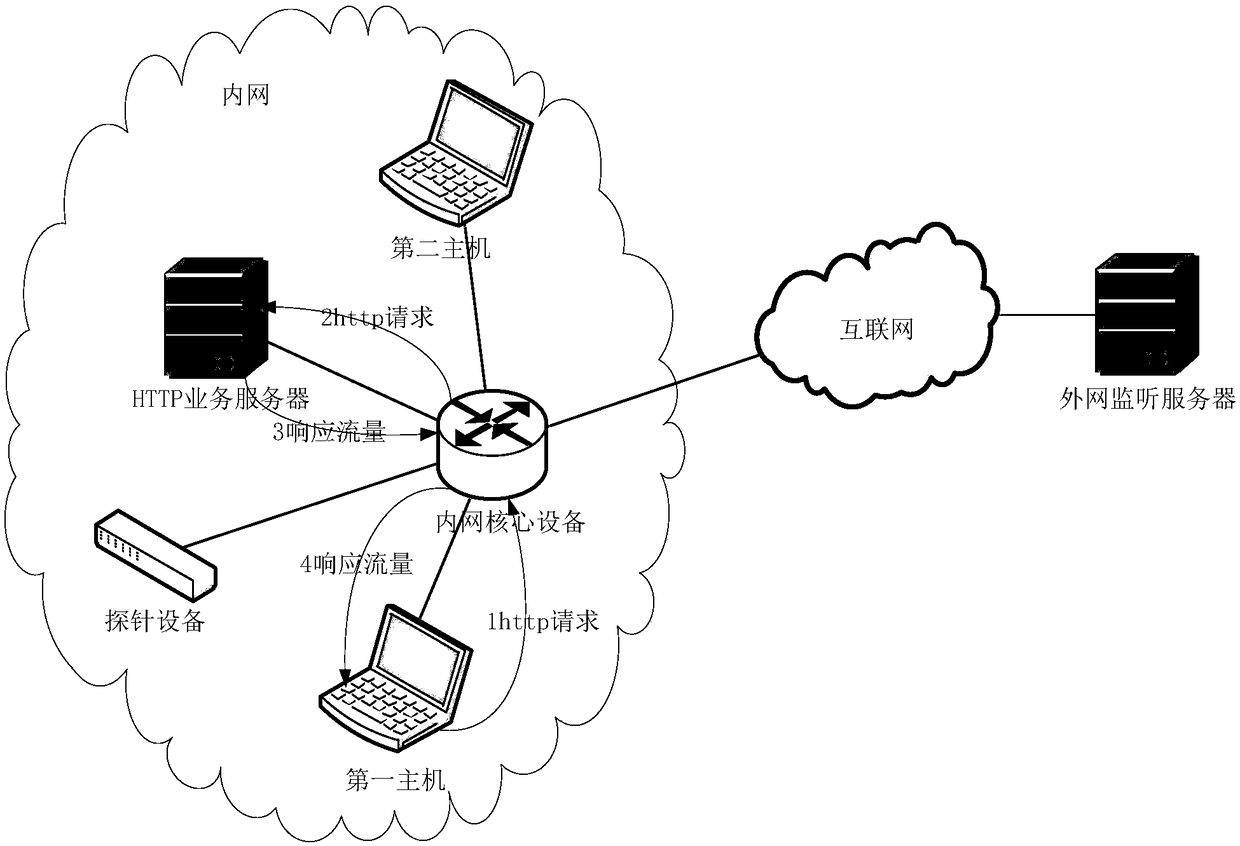
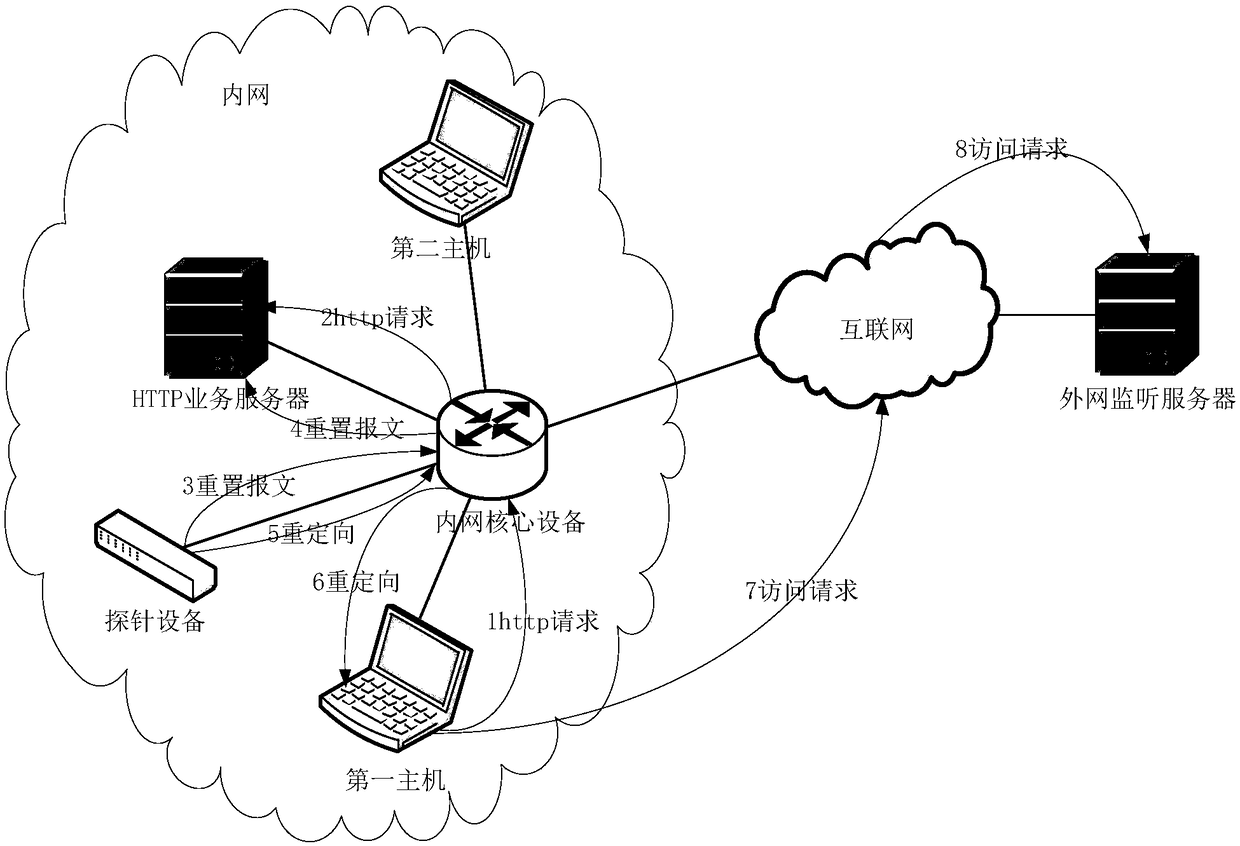
[0045] The core of the present invention is to provide an illegal outreach detection method, which is applied to a probe device deployed on an intranet link. The probe device is a traffic collection device in a bypass deployment mode. It is generally used for situational awareness products to collect and analyze, and can identify quintuple information, application / protocol information, etc. in traffic access. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com