A real-time privacy exposure monitoring method for data publishing
A real-time monitoring, data-oriented technology, applied in the field of information security technology and privacy protection, can solve the problem that the data collector cannot obtain valuable information from it, and achieve the effect of avoiding leakage and preventing malicious acquisition.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The present invention will be further described below in conjunction with the accompanying drawings and examples.
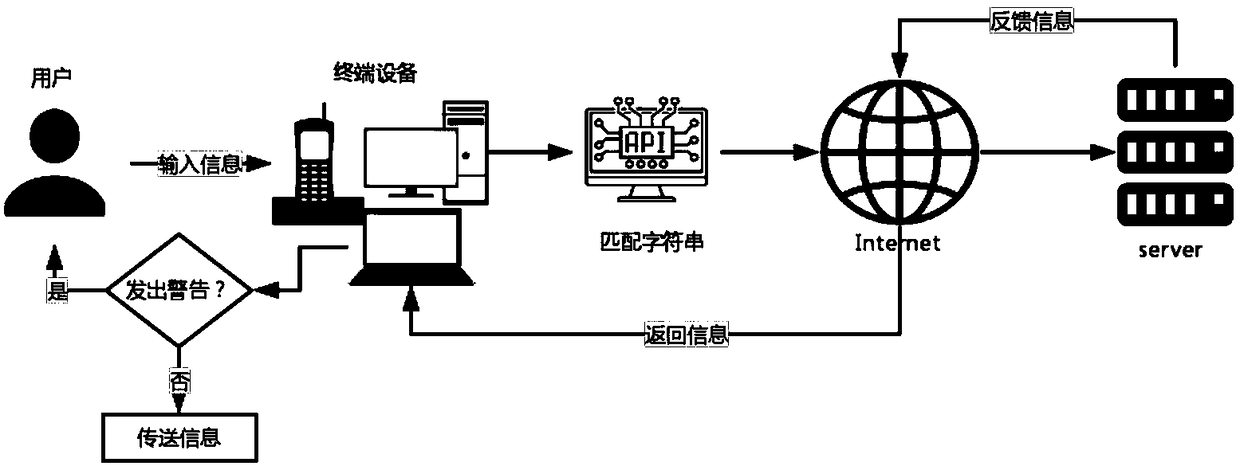
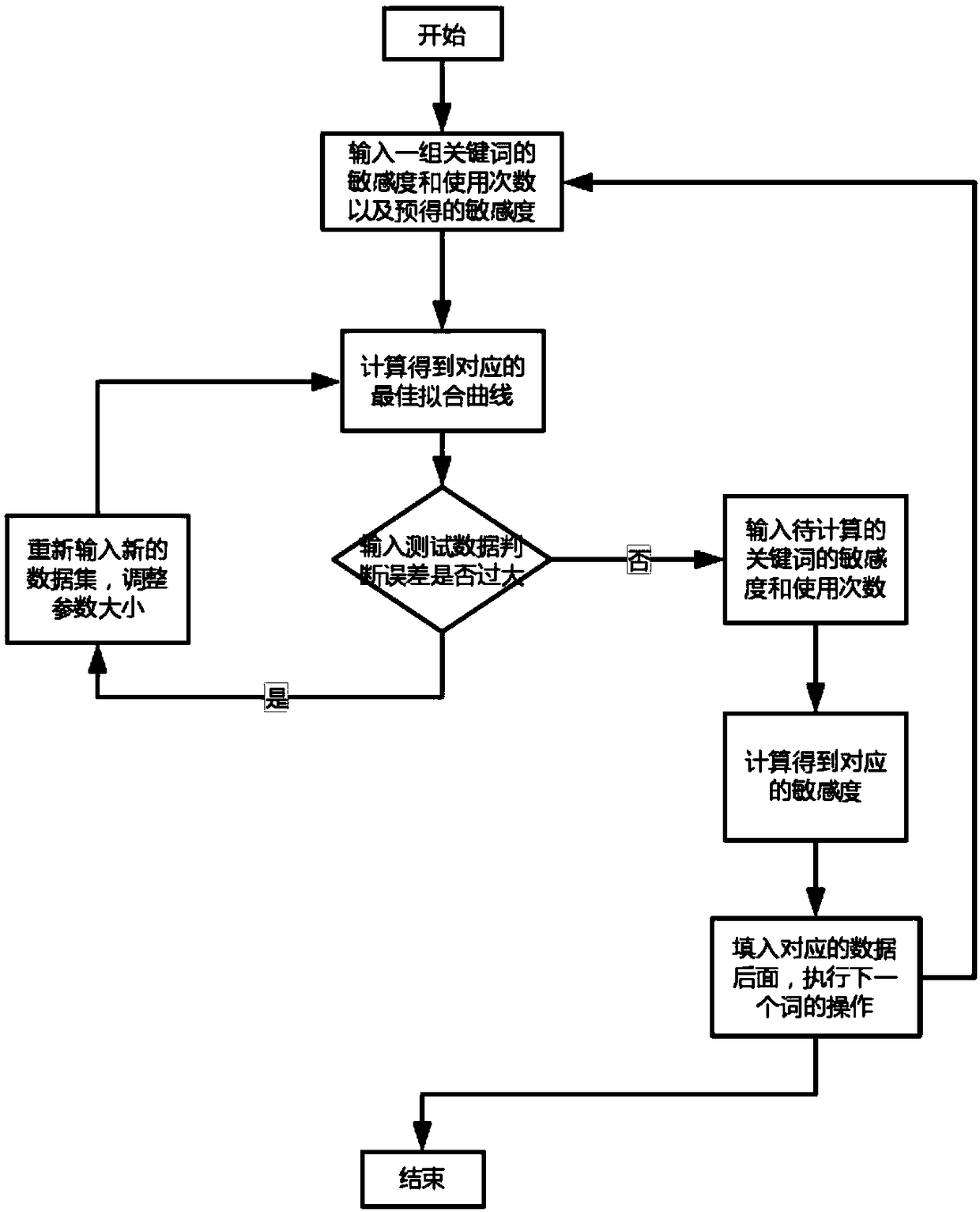
[0034] A data release-oriented real-time monitoring method for privacy exposure of the present invention comprises the following steps:
[0035] S1: Obtain user input content;
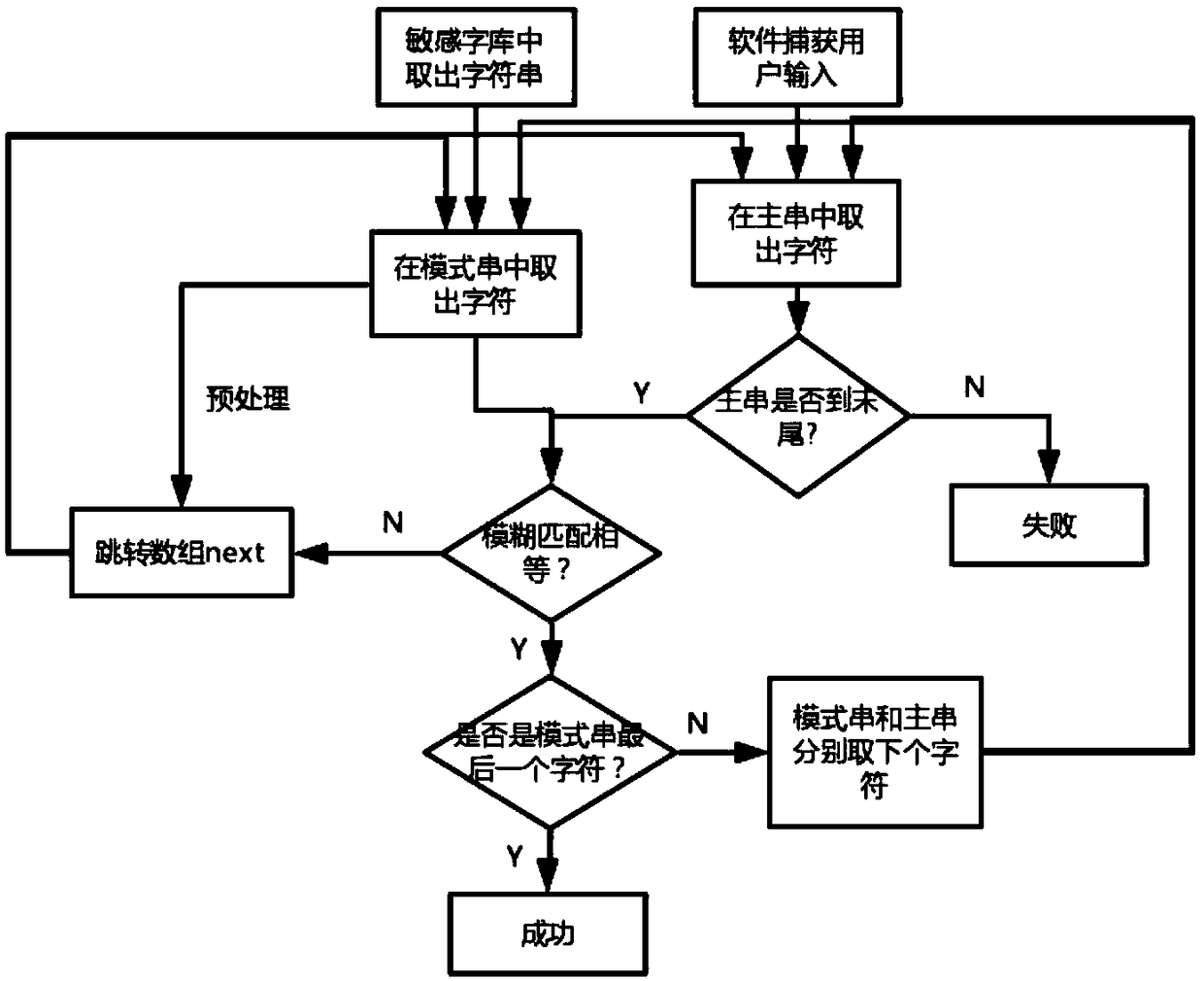
[0036] S2: Search and match the user input content and obtain the required keywords: decompose the user input content into several individual words according to the grammatical features of Chinese characters, and obtain the corresponding keywords through fuzzy matching and KMP algorithm.
[0037] Among them, the fuzzy matching algorithm is to calculate the edit distance between the sound and the shape of the two Chinese characters respectively. The pinyin of the Chinese character can be obtained directly from the pinyin database. Items with different weights can be accumulated to obtain the editing distance of the word sound; while the glyph is obtained by using the four-corner nu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com