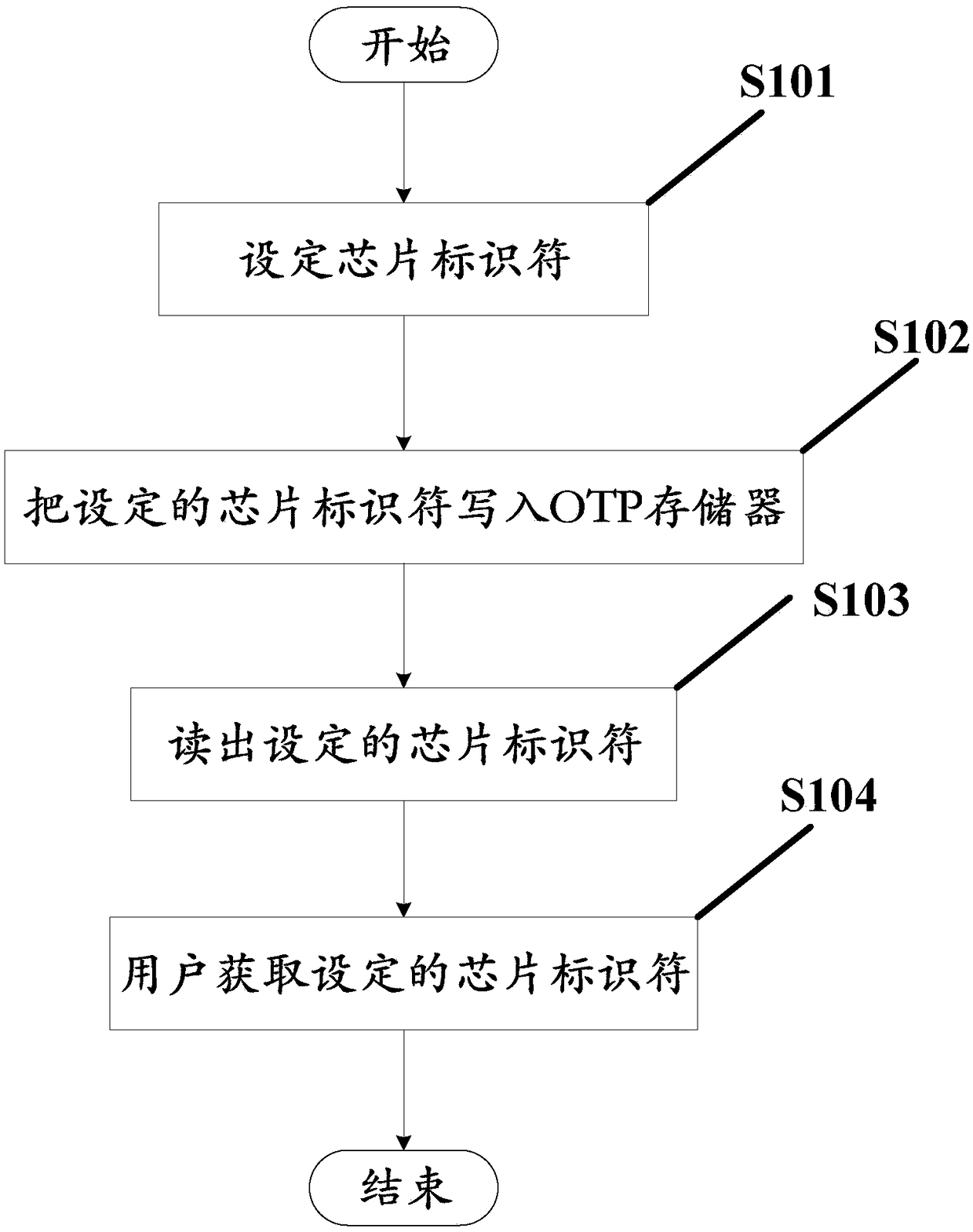
Chip identification method
A chip identification, chip technology, applied in the field of chip identification, can solve problems such as product security threats
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
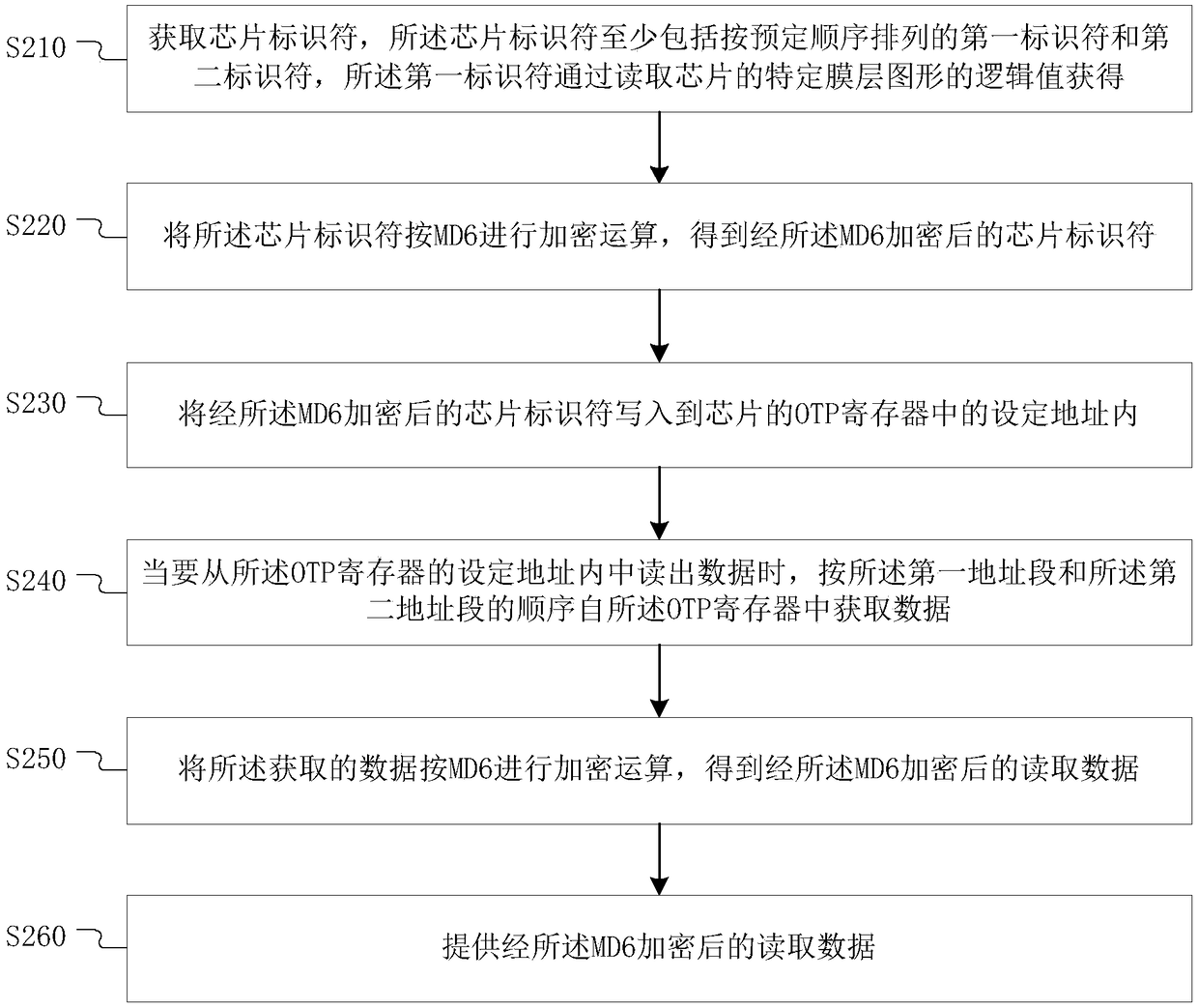
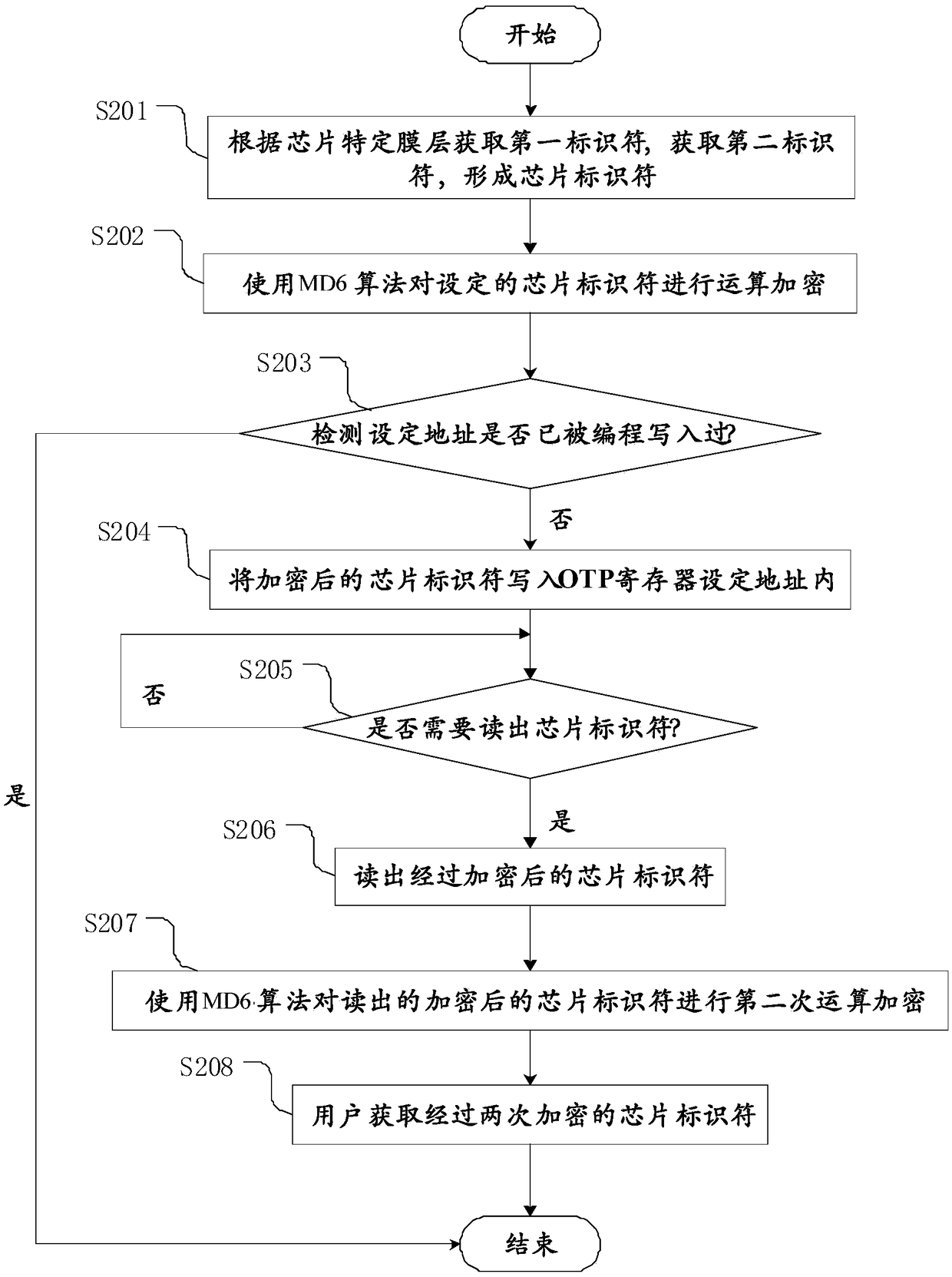
[0059] The first is step S201, the first identifier is obtained according to the specific film layer of the chip, and the second identifier is obtained to form a chip identifier.
[0060] The chip identifier includes an identifier set by a user (second identifier), an identifier set by a manufacturer (first identifier), other user-defined identifiers or identifiers in any combination thereof. In this embodiment, a combination of user-set identifiers and manufacturer-set identifiers is used, such as Figure 4 Reference numerals 301 and 302 show. Using this method, as long as the identifiers set by the user and the identifiers set by the manufacturer are well protected, even a researcher who knows all the design details cannot crack the above-mentioned chip identifiers without any value, nor can the blank The chip, rewritten as a chip with a specific chip identifier, is more secure than a single manufacturer code or user code.
[0061] Next is step S202, using the secure hash ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com