Setting method for viewing permission of operation record based on time period
一种操作记录、时间段的技术,应用在计算机安全装置、仪器、数字数据认证等方向,能够解决不利公司信息保密、使用方操作繁琐又麻烦、操作记录泄露等问题,达到提高准确性和授权速度、权限设置清晰、降低可能性的效果
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 3
[0085] [Embodiment 3] The method for setting the permission to view operation records based on time period includes: S31. Selecting a role as an authorization object.
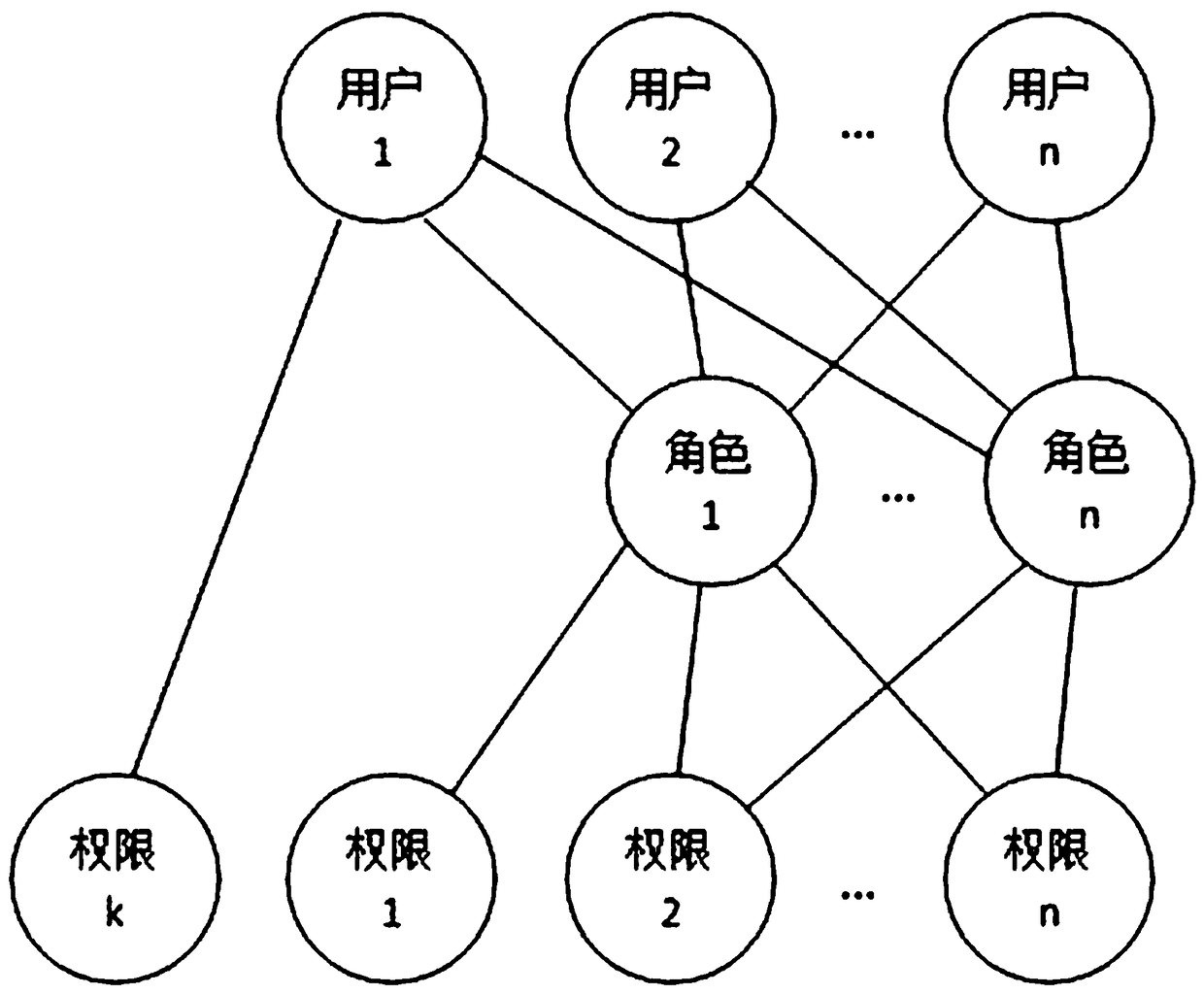
[0086] The role is an independent individual, not a group / class. A role can only be associated with a unique user at the same time, and a user is associated with one or more roles; users obtain the permissions of their associated roles; users obtain their associated roles permission. When a role (independent individual character role) is created or after the role is created, select a department for the role, then the role belongs to the department, and the role is authorized according to the job content of the role, and the name of the role is unique under the department. The number of this role is unique in the system.
[0087] When the user is transferred, cancel the association between the user and the original role, and associate the user with the new role, then the user automatically loses the authority o...
Embodiment 4
[0102] [Embodiment 4] A method for setting the permission to view operation records based on time periods, including: S41. Select a role as an authorization object.
[0103] The role is an independent individual, not a group / class. A role can only be associated with a unique user at the same time, and a user is associated with one or more roles; users obtain the permissions of their associated roles; users obtain their associated roles permission. When a role (independent individual character role) is created or after the role is created, select a department for the role, then the role belongs to the department, and the role is authorized according to the job content of the role, and the name of the role is unique under the department. The number of this role is unique in the system.
[0104] When the user is transferred, cancel the association between the user and the original role, and associate the user with the new role, then the user automatically loses the authority of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com