An industrial control full flow analysis method and device
An analysis method and technology of an analysis device, applied in the field of network security, can solve problems such as inability to use peripheral equipment, inconvenience for network security personnel, and monitoring software vulnerable to human interference and virus attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
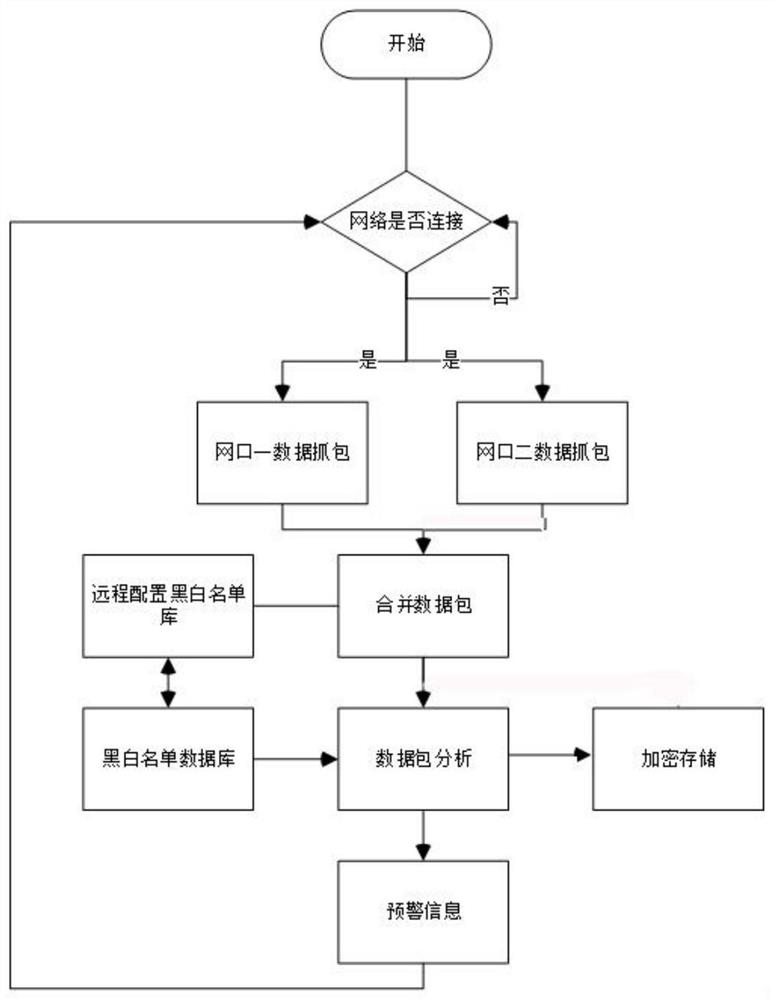
[0041] Such as figure 1 An industrial control full flow analysis method shown includes the following steps:
[0042] A. Capture packets from at least two mirror ports;
[0043] B. Merge the data packets and identify and analyze the data packets according to the black and white list database;
[0044] C. Encrypt and store data packets and generate early warning information.
Embodiment 2
[0046] Based on the method principle of the foregoing embodiment, this embodiment discloses a specific implementation method by taking two mirroring ports as an example.
[0047] Capture packets from two mirrored ports;
[0048] A ListsMap container is used to sort and merge the time stamps of the data packets, and the ListsMap container includes a red-black binary tree algorithm. The red-black binary tree algorithm uses a balanced tree binary structure, and its general structure is as follows Figure 5 shown. To achieve the greatest balance of the binary tree in ListsMap is to make the number of its left and right subtrees as equal as possible to reduce the subsequent sorting time. By using a binary tree, binary sorting can be easily implemented, because binary sorting is already in progress when data is inserted. For example, let's sort {7,8,9,10,11,12} and draw its process, such as Figure 6 shown.
[0049] Use the load_protcols algorithm and the Corasickplus algorithm...
Embodiment 3
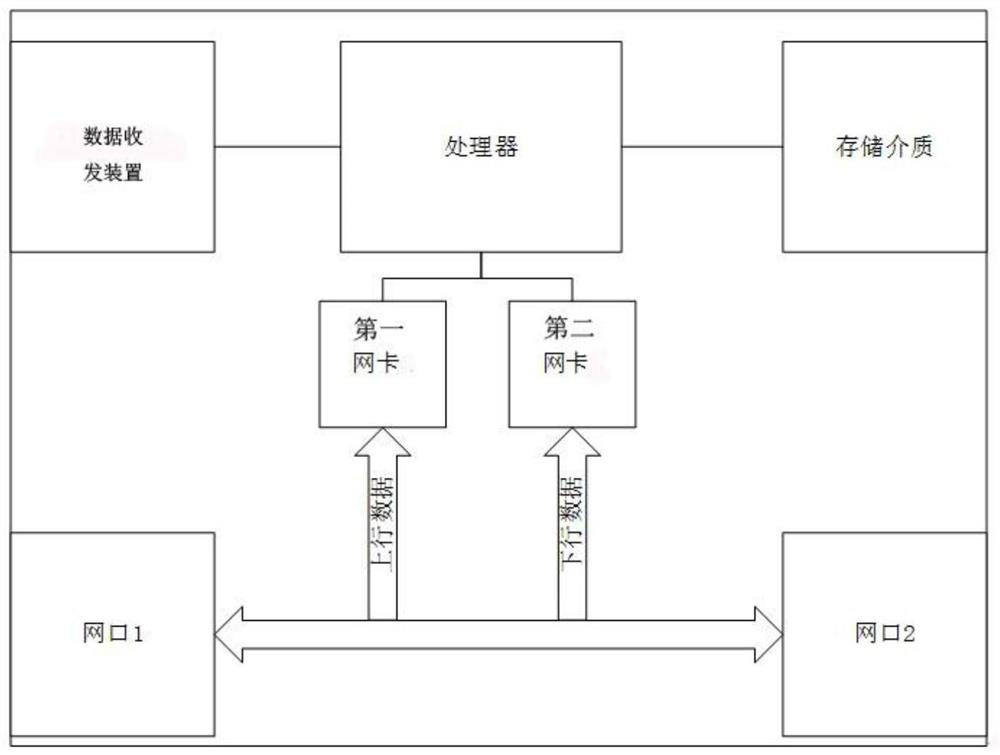
[0060] Based on the above method, as figure 2 The illustrated embodiment discloses a device capable of implementing the above method.
[0061] An industrial control full flow analysis device, comprising:
[0062] The first network card used to obtain data packets;
[0063] A second network card for obtaining data packets;
[0064] According to the method of any one of the above-mentioned embodiments, a processor for merging, recognizing and analyzing data packets is realized;
[0065] A storage medium for storing data packets;
[0066] A data transceiver module for data reception to realize remote configuration of black and white lists.
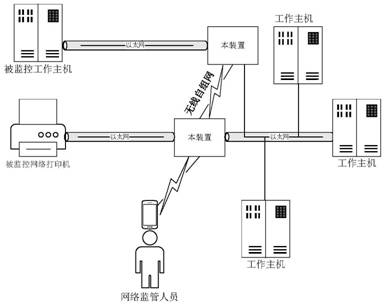
[0067] Multiple industrial control full-flow analysis devices can be connected through a wireless ad hoc network. In the case of large-scale deployment, only one terminal node can be used to manage the entire device group in batches.
[0068] Such as image 3 As shown, this embodiment discloses a specific application of the device. The...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com