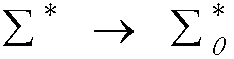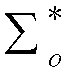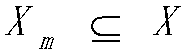Information security discrimination method and system based on rough set theory and related device
A rough set theory and information security technology, applied in computer-readable storage media, in the field of information security discrimination based on rough set theory, can solve the problem of low verification efficiency, inability to timely and accurately feedback security status, and adaptability to industrial application scenarios problems such as poor verification, to achieve the effect of improving verification efficiency, reducing time complexity, and reducing verification time.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0117] Combine the following Figure 11 , Figure 11 A flow chart of an information security discrimination method based on rough set theory provided in the embodiment of the present application, which specifically includes the following steps:
[0118] S101: Execute considerable transition optimization operations on the first event sequence and the second event sequence constructed according to the target discrete event system, respectively, to obtain the first generator and the second generator correspondingly;
[0119] Among them, the first event string contains the information that needs to be concealed, and the second event string is the cover event string of the first event string, that is, the ultimate goal is to prevent others from accurately distinguishing which event the information that needs to be concealed (need to be kept secret) is. In the string, it can be considered that the information that needs to be concealed is kept confidential if it cannot be determine...
Embodiment 2
[0135] The following combination Figure 12 , Figure 12 The flow chart of a method for judging whether there is opacity and the degree of opacity between the first event string and the second time string in the information security judging method provided by the embodiment of the present application, based on the first embodiment, is given A method for specifically judging opacity and the degree of opacity, the specific steps are as follows:
[0136] S201: Determine the event string to which it belongs according to the decision attribute corresponding to each event path contained in the decision table, and obtain the event path set of the first event string and the event path set of the second event string;
[0137] S202: Determine whether there is a consistent event path in the set of event paths respectively corresponding to the first event string and the second event string;
[0138] S203: Determine that there is no opacity between the first event string and the second e...
Embodiment 3
[0148] Aiming at the opacity of the discrete event system, this embodiment proposes a method using rough set theory as a knowledge extraction tool to deal with the verification of the opacity of the discrete event system: first formalize the opacity of the discrete event system, and then use the rough set The theory expresses the discrete event system in the form of information tables and decision tables, and obtains a sufficient and necessary condition for the opacity of the discrete event system, and thus gives an algorithm for verifying the opacity of the discrete event system, realizing the opacity of the system Validation of:
[0149] 1. According to the discrete event system G=(∑, X, δ, ψ, x 0 , X m ), first construct the automaton of L and K:
[0150] Known L, Construct the automaton of L first: G 1 =(∑,X 1 ,δ 1 , ψ 1 , x 10 , X 1m ), where L m (G 1 ) = L, for all x 1 ∈X 1 , ψ 1 (x 1 ) = ∑. In order to determine G 1 Substantial transfer of , one can ch...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com