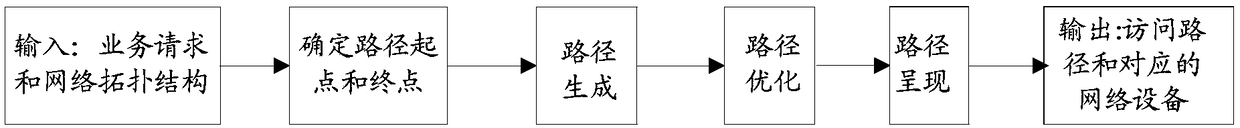
Method and device for acquiring access path
An access path and routing technology, applied in the field of network communication and network security, which can solve the problems of redundancy, not considering the different characteristics of device routing and forwarding, and forwarding errors.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 4 example
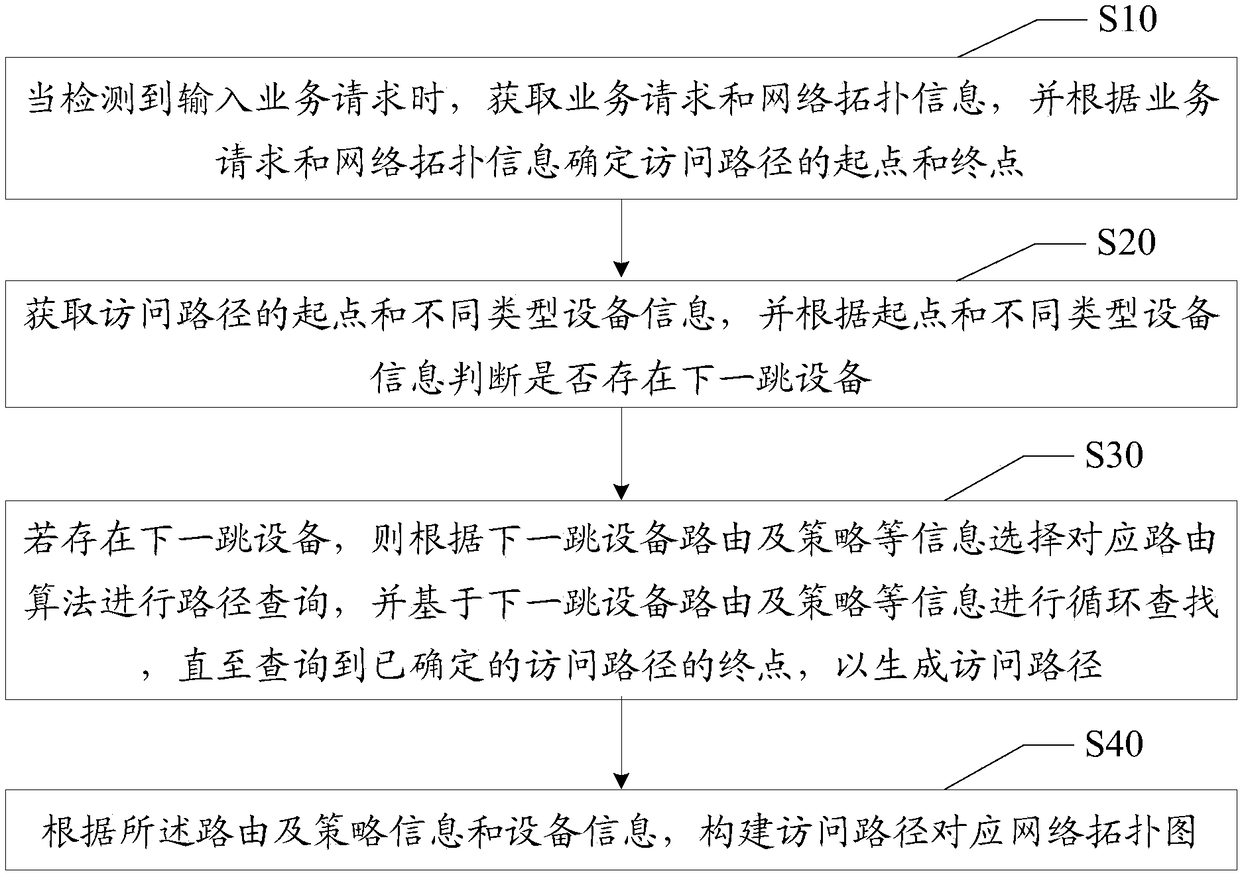
[0091] refer to Figure 6 , the present invention also proposes a fourth embodiment correspondingly, and step S30 includes:
[0092] Step S31, if there is a next-hop device, perform path query according to different query modes according to the type of the next-hop device;
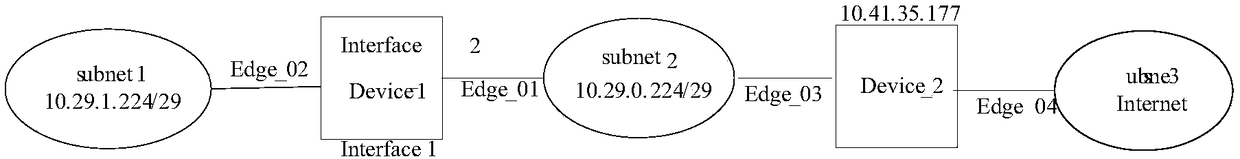
[0093] According to the determined device type and service request, the background business system will query the path of the next-hop device type according to different query modes, and there are general algorithms in the routing selection process; however, there are differences in the routing selection process of each type of device For example, some devices support policy routing and destination routing, some devices support policy routing, source interface routing, source address routing, and destination routing, and some devices support blocking policies and destination routing. different device types for different routing options.
[0094] Step S32, when the path query is detected, analyze and matc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com