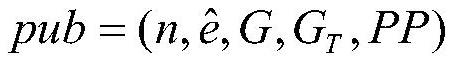A Confusable Anonymous Authentication Method
An anonymous authentication and authentication key technology, applied in the field of anonymous authentication and confusion theory, cryptography, can solve the problem that the program is difficult to understand and analyze, and achieve high security effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
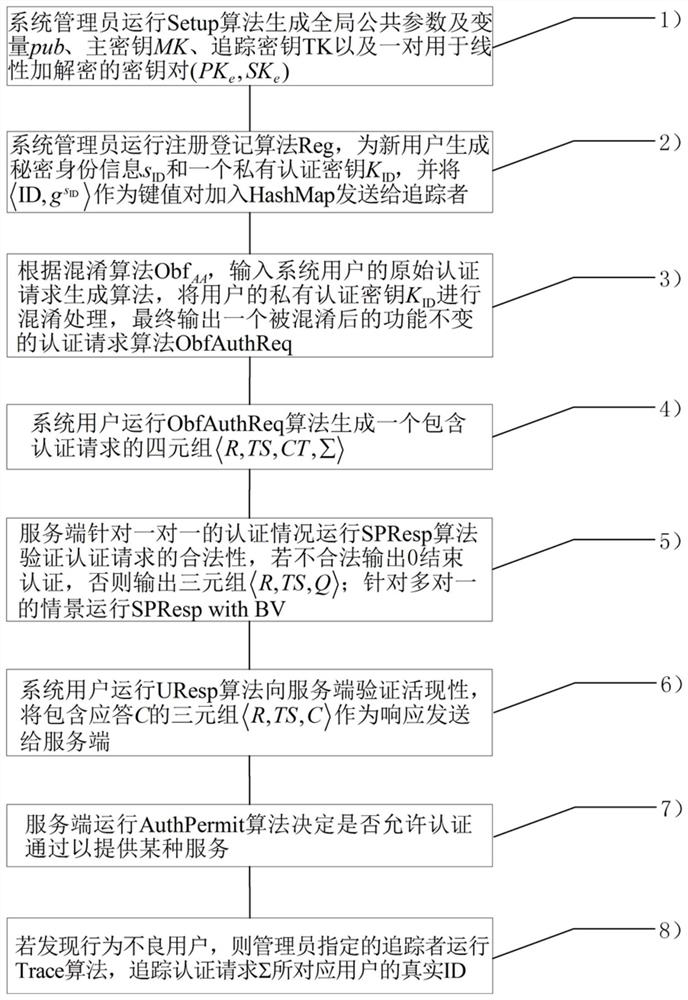
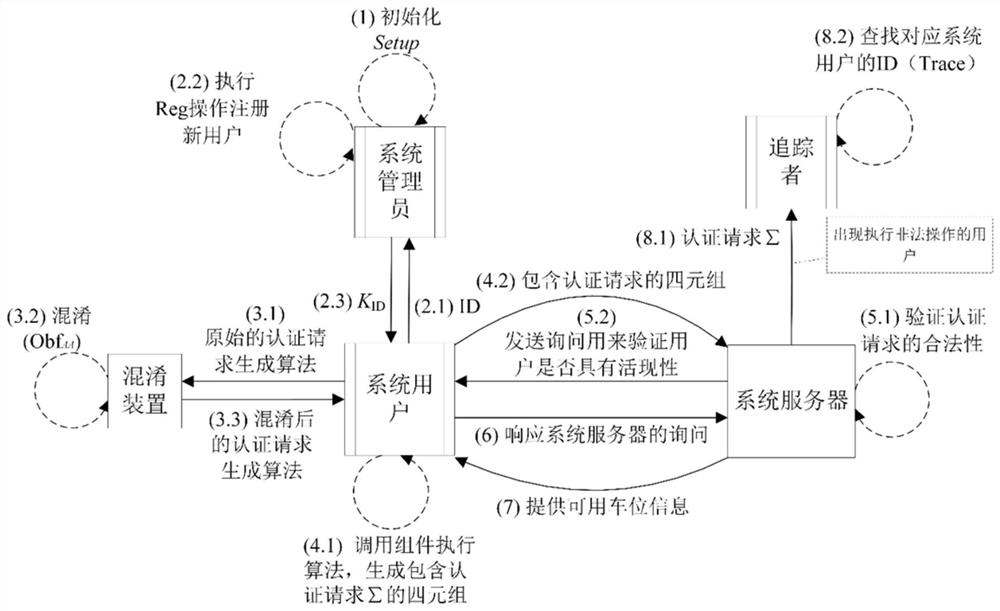
[0237]Such asfigure 2 As shown, the present embodiment applies the above method to a mobile smart group perception system for finding a parking space, and the user first needs to register your identity information to the system administrator, and the legal user after registration can mark the server in the system. Initiate anonymous authentication requests, the server provides information on the user's legitimacy and provides users with the available parking space. The anonymous authentication request guarantees that the user's privacy information is not exposed, but if some users have implemented illegal operations that do not meet the system, the tracker can find user identity through the user's authentication request.
[0238]The specific steps of the application are as follows:
[0239]1 System administrator initializes the system (SETUP)
[0240]2 new members conduct user registration
[0241]2.1 Send its identity ID to the system administrator when the user requests to join the system
[024...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com