Method and device for protecting personal identification code
An identification code and field filling technology, applied in the field of information security, can solve problems such as personal identification code leakage, and achieve the effect of preventing leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0031] This embodiment provides a method for personal identification code protection, including:
[0032] Step S1, the device receives the plaintext personal identification code and encryption parameters, and determines the encryption mode according to the encryption parameters. When the encryption mode is the first encryption mode, execute step S2; when the encryption mode is the second encryption mode, execute step S3;
[0033] Step S2, the device sets the control field data to the first preset value, and uses the sixth preset value to organize the filling field data, organizes the plaintext data packet according to the control field data, the plaintext personal identification code and the filling field data, and uses the The account domain data performs the first preset processing on the plaintext data packet, and encrypts the processing result with the pre-stored encryption key to obtain the ciphertext data packet; sends the ciphertext data packet to the server;
[0034] S...
Embodiment 2
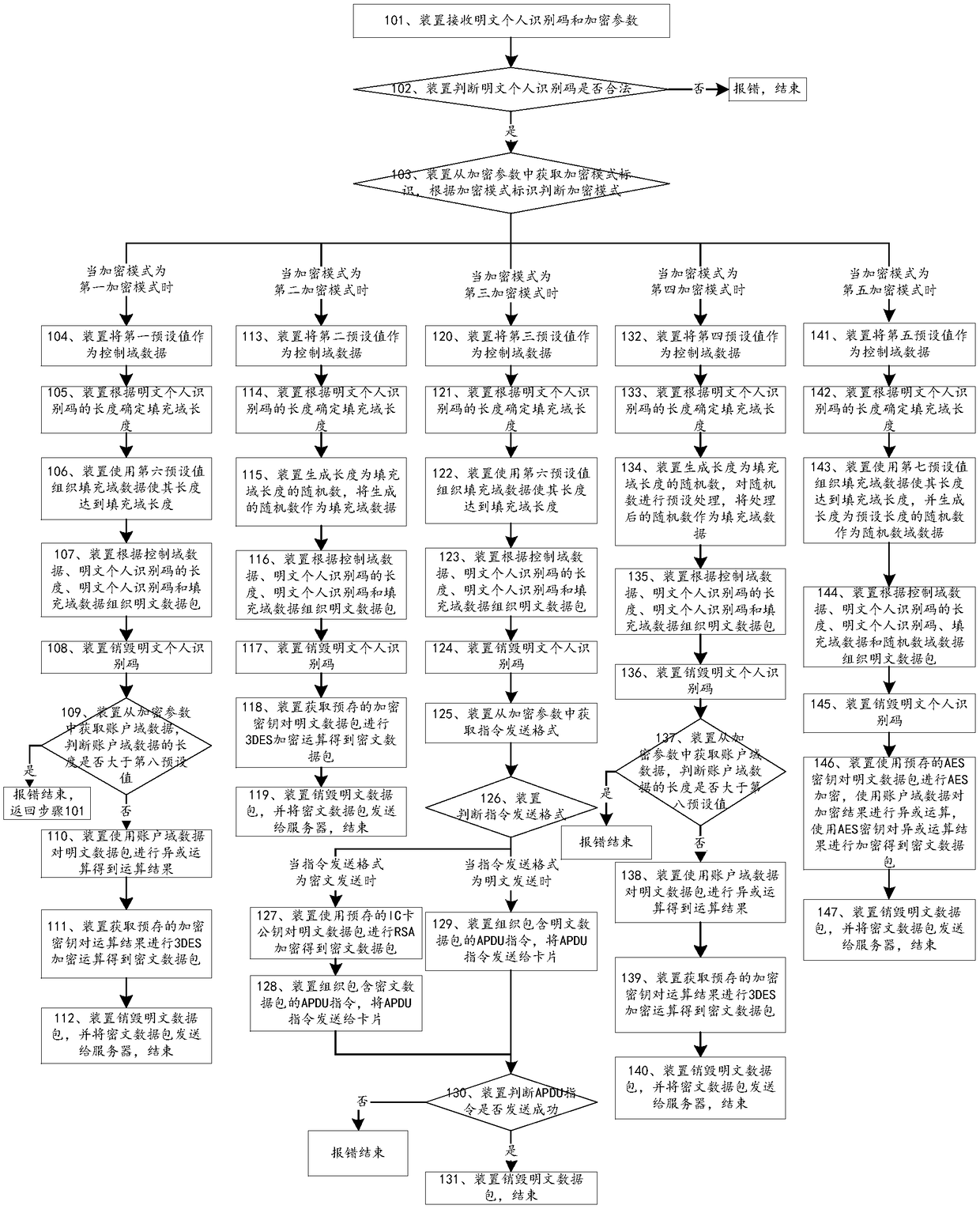
[0053] This embodiment provides a method for personal identification code protection, see figure 1 ,include:
[0054] Step 101, the device receives a plain text personal identification code and encryption parameters;
[0055] Specifically, in this embodiment, the clear text personal identification code received by the device is specifically 1234;
[0056] The encryption parameters include at least the encryption mode identifier; it also includes account domain data or data transmission format;
[0057] When the encryption mode is 01, the encryption parameters also include: account domain data; when the encryption mode is 03, the encryption parameters also include: data transmission format; when the encryption mode is 04, the encryption parameters also include: account domain Data; when the encryption mode is 05, the encryption parameters also include: account domain data;
[0058] Step 102, the device judges whether the plaintext personal identification code is legal, and i...
Embodiment 3
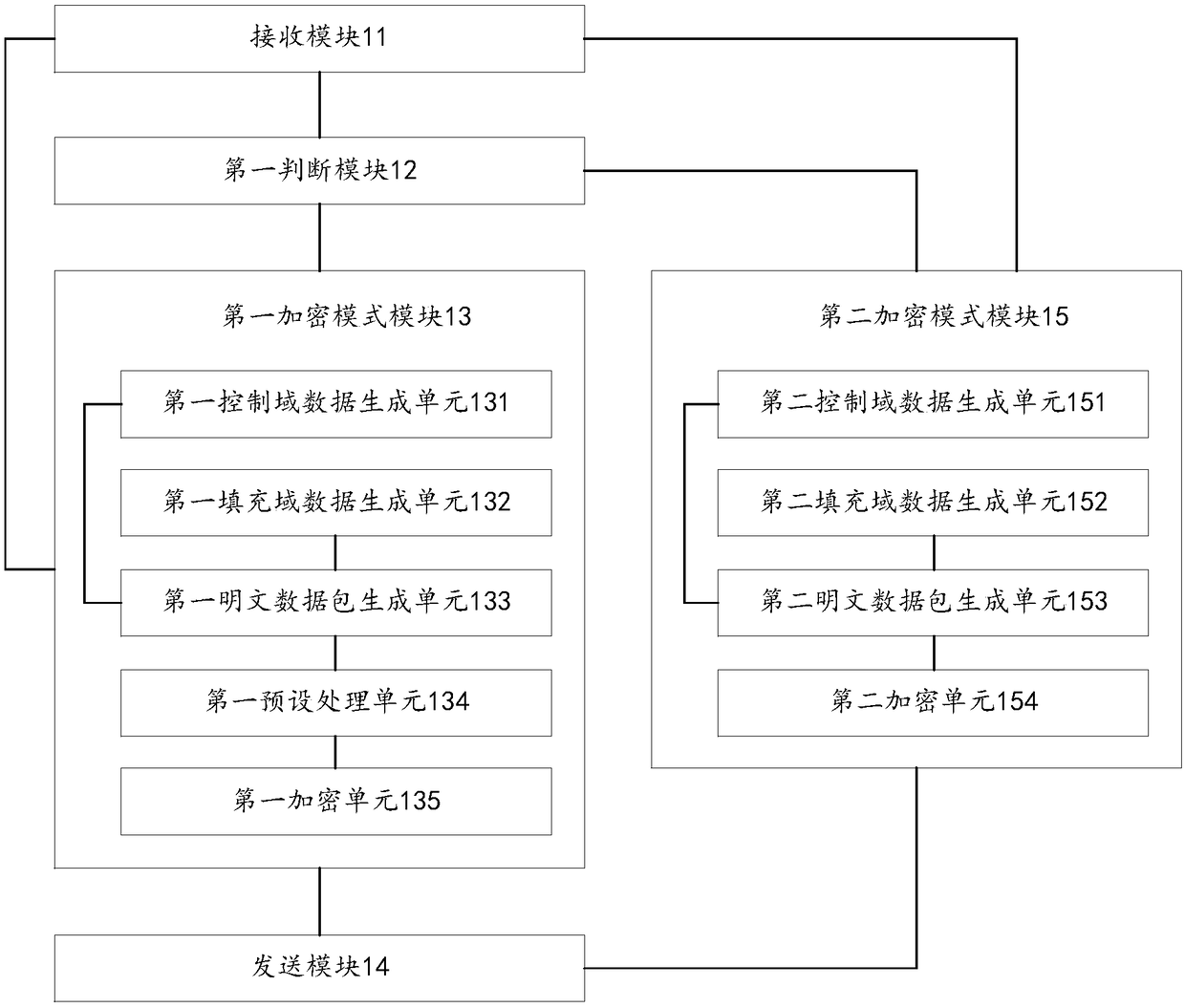
[0156] This embodiment provides a personal identification code protection device, see figure 2 ,include:
[0157] The receiving module 11 is used to receive plaintext personal identification codes and encryption parameters;
[0158] The first judging module 12 is configured to determine the encryption mode according to the encryption parameters received by the receiving module 11;
[0159] The first encryption mode module 13 includes:
[0160] The first control field data generating unit 131 is configured to set the control field data to a first preset value when the first judging module 12 determines that the encryption mode is the first encryption mode;
[0161] The first padding field data generating unit 132 is configured to use the sixth preset value to organize padding field data when the first judging module 12 determines that the encryption mode is the first encryption mode;
[0162] The first plaintext data packet generating unit 133 is configured to generate the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com