Data authorization deterministic update method based on proxy re-encryption for cloud
A proxy re-encryption and data authorization technology is applied in the field of data authorization management and deterministic update based on proxy re-encryption in the cloud. burden effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
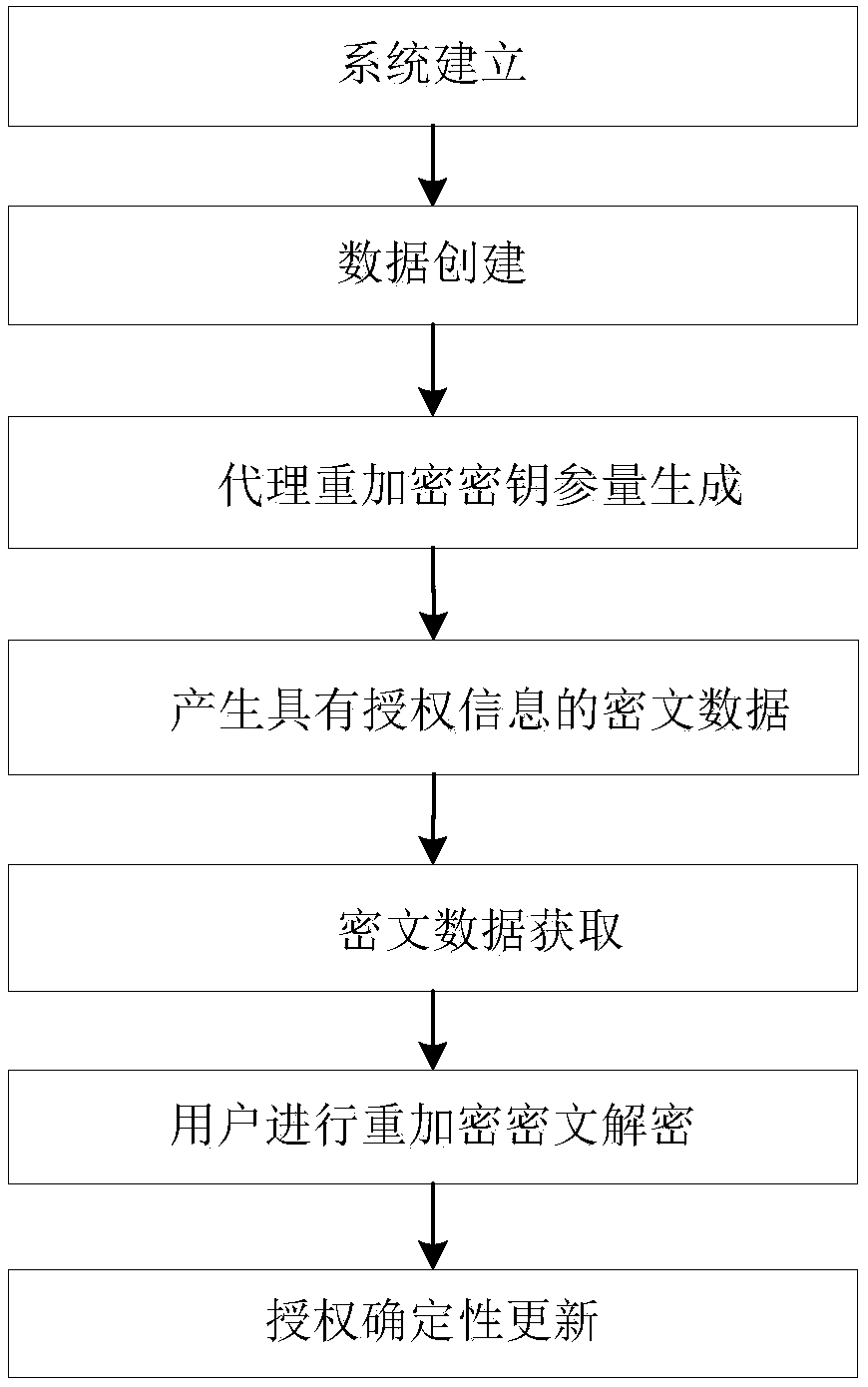
Embodiment
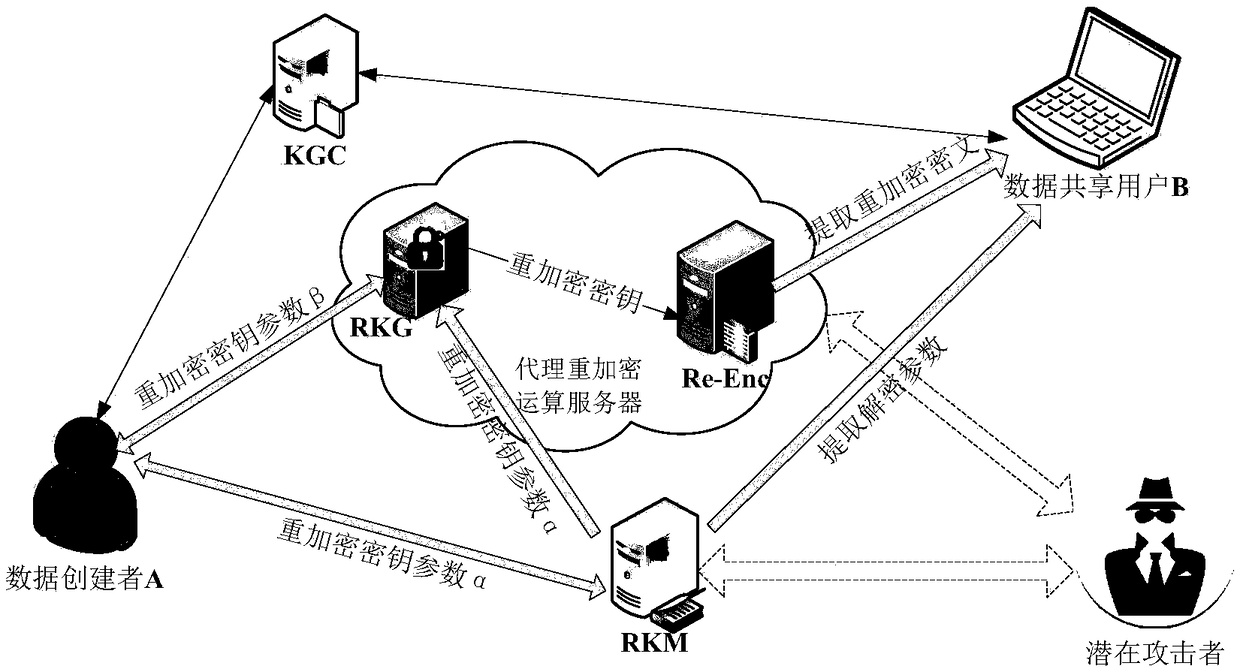
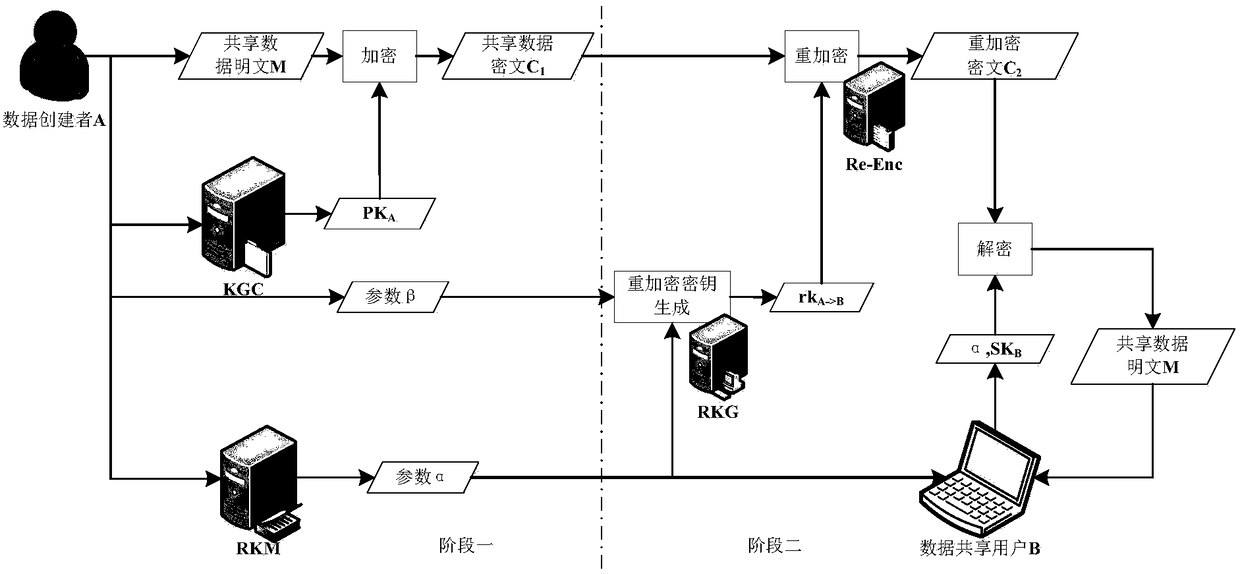
[0086] figure 1 It is the system model diagram of the present embodiment, wherein:
[0087] Data creator A: Create the accessed data m, and perform security processing such as encryption on it, and finally share the data through the cloud server, and manage the authorized scope of the data at the same time.
[0088] Data sharing user B: Apply for access to the message M, obtain the data through the cloud server and decrypt it, and finally realize the acquisition of data or services.
[0089] KGC server: Initialize re-encryption parameters for users and generate public-private key pairs.
[0090] RKM server: used to store proxy re-encryption key parameters and also decryption key parameters. The server interacts with the data creator and achieves deterministic changes in authorization through parameter management;
[0091] RKG server: used to generate the proxy re-encryption key, which requires the user's initialization parameters and the parameters stored in RKM to jointly g...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com