Method and device for discriminating threat information credibility based on multi-dimensional trusted feature
A discriminative method and multi-dimensional technology, applied in the field of network security, can solve the problems of reducing the accuracy of threat intelligence to be detected and incomplete untrustworthy threat intelligence, and achieve the effect of improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
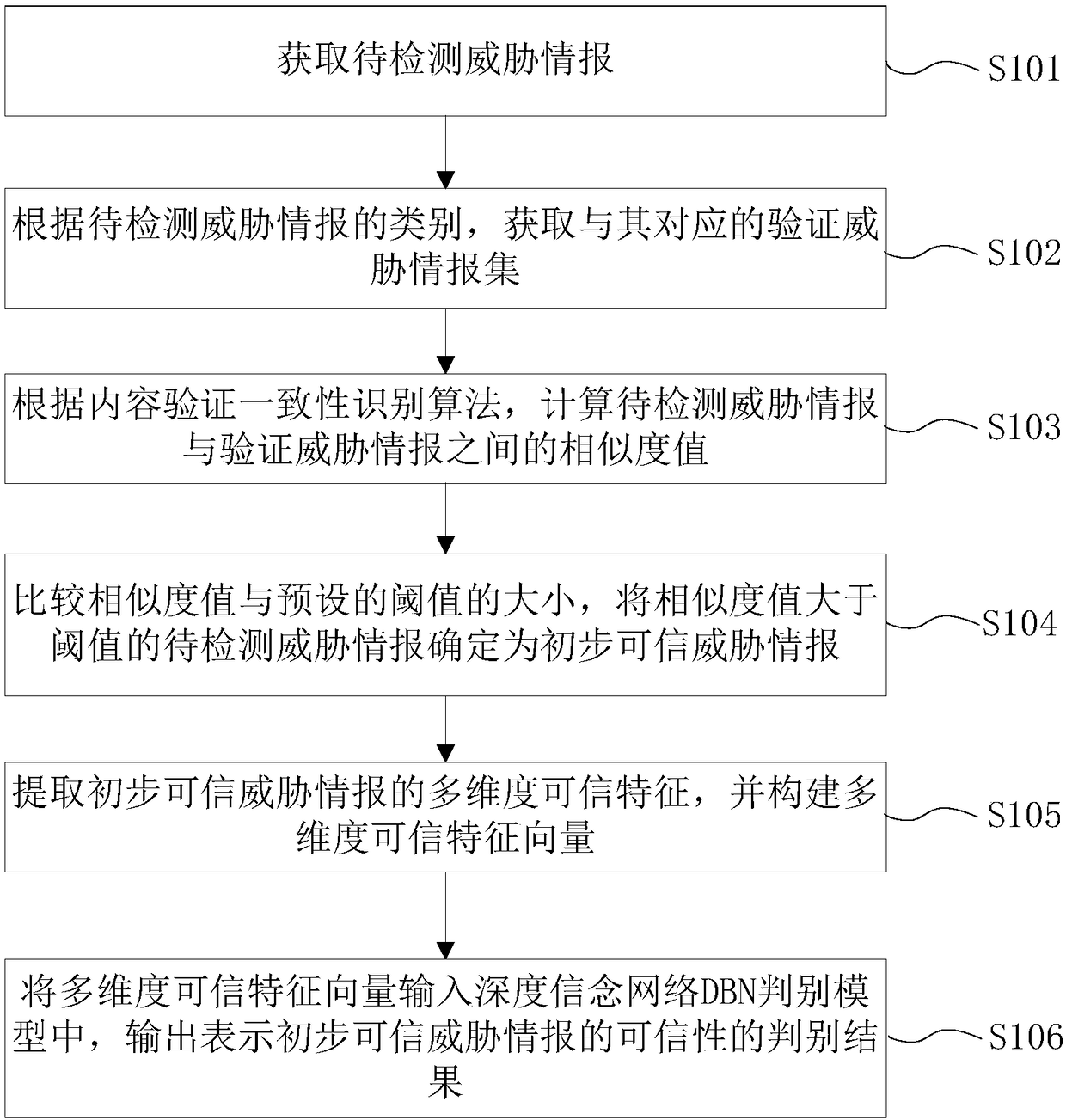
[0078] As an implementation of the embodiment of the present invention, the method further includes: using a threat intelligence sample set to train the DBN discriminant model to obtain a new DBN discriminant model, wherein the threat intelligence sample set contains multiple threat intelligence with known credibility .
[0079] In practical applications, the DBN discriminant model will mark the credibility of the classified preliminary credible threat intelligence after each output of the credibility discrimination result representing the preliminary credible threat intelligence, and store it in the threat intelligence sample set , and then according to the preset cycle, the DBN discriminant model is trained with the updated threat intelligence sample set to obtain a new DBN discriminant model.
[0080] Specifically, the threat intelligence sample set is divided into training threat intelligence sample set and test threat intelligence sample set, the training threat intellige...
Embodiment approach
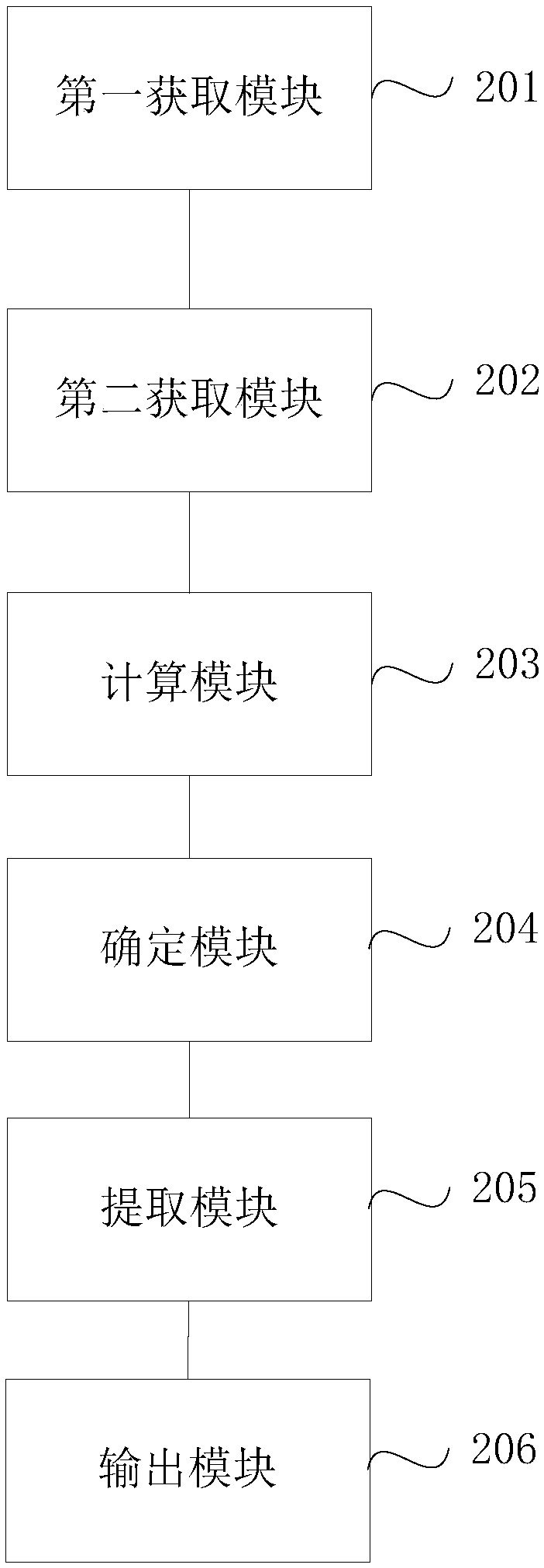
[0095] As an implementation manner of the embodiment of the present invention, the device further includes: a training module, configured to use a threat intelligence sample set to train the DBN discriminant model to obtain a new DBN discriminant model, wherein the threat intelligence sample set contains multiple credible Known Threat Intelligence.
[0096] As an implementation manner of the embodiment of the present invention, the above-mentioned training module includes:
[0097] The division sub-module is used to divide the threat intelligence sample set into a training threat intelligence sample set and a test threat intelligence sample set;
[0098] The extraction sub-module is used to extract the multi-dimensional credible feature set of the training threat intelligence sample set, and construct a multi-dimensional credible feature vector space;
[0099] The training sub-module is used to iteratively train the DBN discriminant model using the multi-dimensional credible ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com