Method and system for electronic data preservation
A technology of electronic data and original data, applied in the field of information security, can solve problems such as the inability to verify the authenticity of electronic data, and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
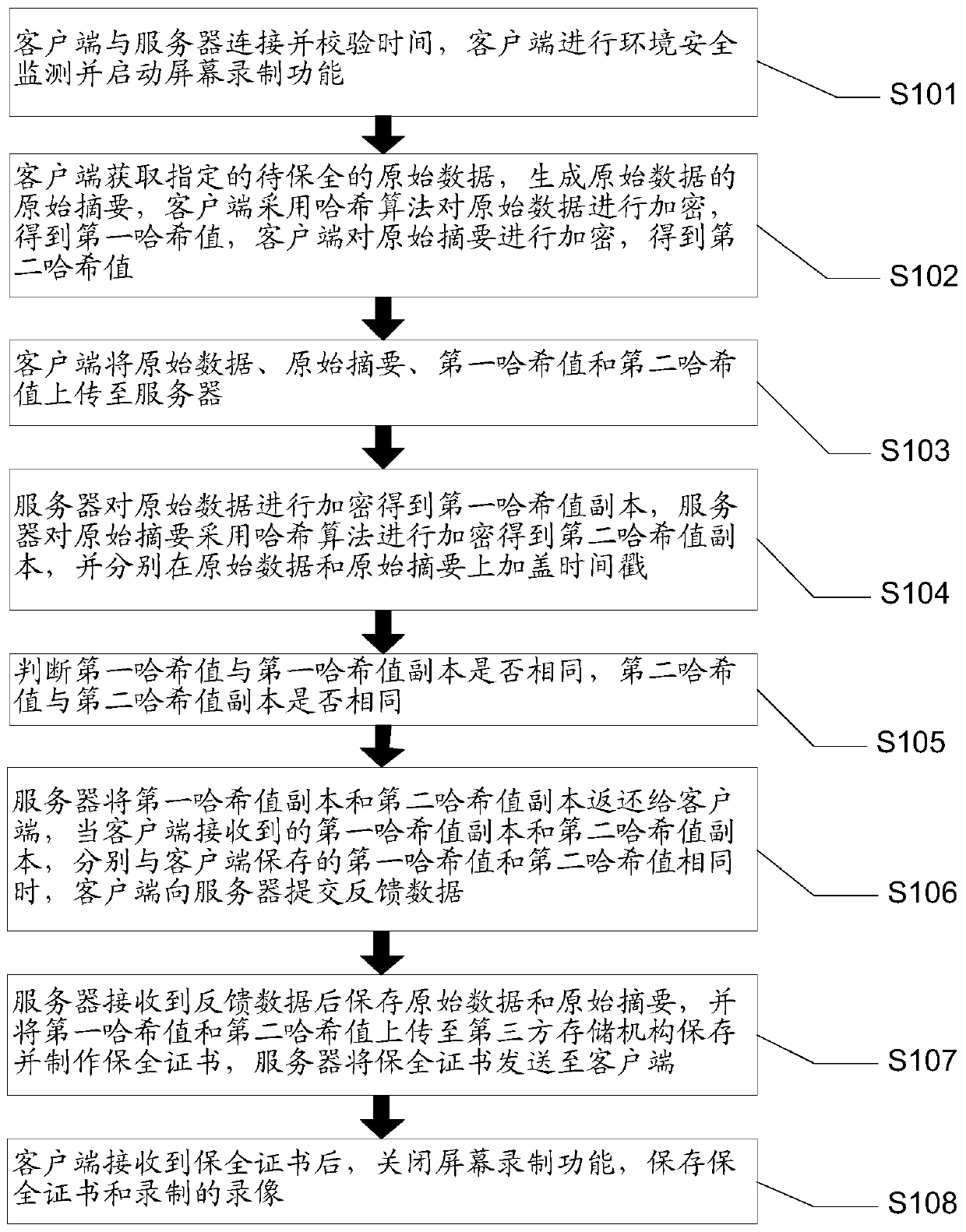
[0059] figure 1 It is a flowchart of a method for electronic data preservation in Embodiment 1 of the present invention, such as figure 1 As shown, a method of electronic data preservation, including:
[0060] S101: the client connects to the server and verifies the time, the client performs environmental security monitoring and starts a screen recording function.
[0061] Specifically, when using the client in the present invention, it is necessary to try to connect to the server first. After the connection is successful, check the local time of the client and the time of the server. It is necessary to keep the time of the client consistent with the time of the server. When the time is inconsistent with the time of the server, the server returns a warning message to the client, requiring the client to modify the local time. If the client does not modify, but continues to operate, all time is based on the time of the server, and the time of the server is passed through the ne...
Embodiment 2
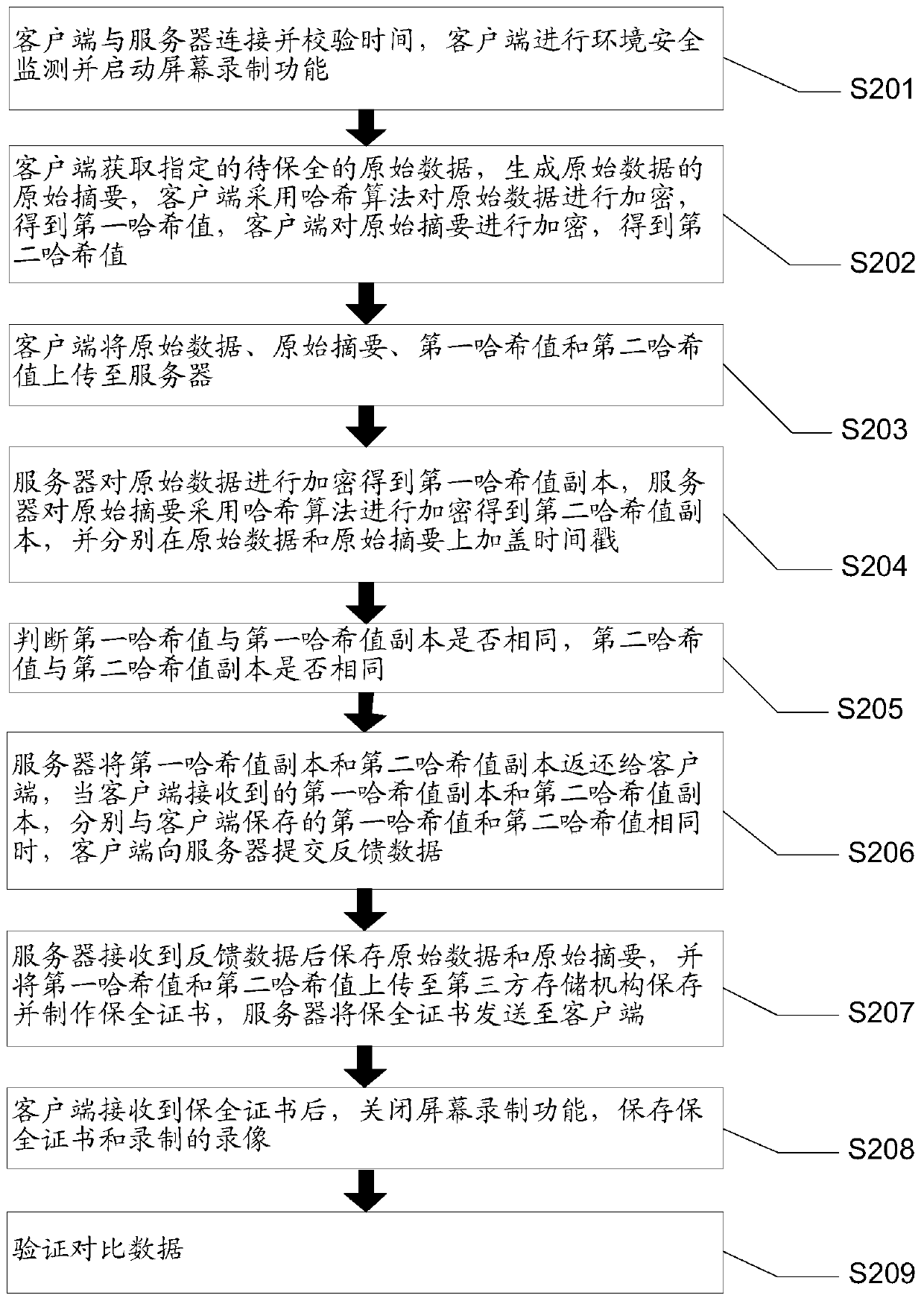
[0078] figure 2 It is a flowchart of a method for electronic data preservation in Embodiment 1 of the present invention, such as figure 1 As shown, a method of electronic data preservation, including:
[0079] S201: The client connects to the server and verifies the time, and the client performs environmental security monitoring and starts a screen recording function.
[0080] Specifically, when using the client in the present invention, it is necessary to try to connect to the server first. After the connection is successful, check the local time of the client and the time of the server. It is necessary to keep the time of the client consistent with the time of the server. When the time is inconsistent with the time of the server, the server returns a warning message to the client, requiring the client to modify the local time. If the client does not modify, but continues to operate, all time is based on the time of the server, and the time of the server is passed through t...
Embodiment 3
[0108] image 3 It is a system for electronic data preservation in Embodiment 3 of this method, such as image 3 As shown, an electronic data preservation system includes: the client 310, the server 320 and the third-party storage mechanism 330 in any one of the present invention, wherein:
[0109] The client 310 is connected with the server 320, including:
[0110] A screen recording module 311, configured to record the screen;
[0111] The first encryption module 312 is used for data encryption and decryption;
[0112] A first transmission module 313, configured to transmit data;
[0113] The first storage module 314 is used for storing data;
[0114] Server 320, connected with client 310 and third-party storage mechanism 330, includes:
[0115] The second encryption module 321 is used to encrypt and decrypt data;
[0116] A security certificate processing module 322, configured to make a security certificate;
[0117] A second transmission module 323, configured to t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com