Industrial control network device abnormal traffic detection method
A technology for abnormal equipment and abnormal traffic, applied in the direction of data exchange network, digital transmission system, electrical components, etc., to achieve the effect of reliable operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
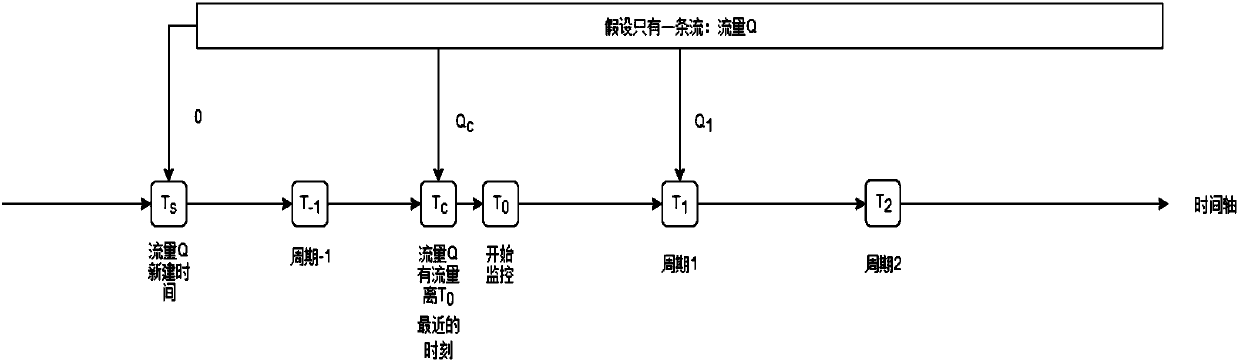
[0062] Such as figure 1 Shown:
[0063] When monitoring started, the latest flow value of the previous cycle (5 minutes) was found from the database;
[0064] Monitoring cycle 1 (T 0 ~T 1 ) are update traffic.
[0065] Brief description of the process: from T 0 From time to time, go to the database to query (according to the 5-tuple + start time query) to the previous cycle (T -1 ~T 0 ) of the latest flow value Qc, this value is used as the initial value, and then the flow value received in cycle 1 minus the initial value is used as the flow of this time period.
[0066] In summary: monitoring period 1(T 0 ~T 1 ) flow = Q 1 –Qc.
Embodiment 2
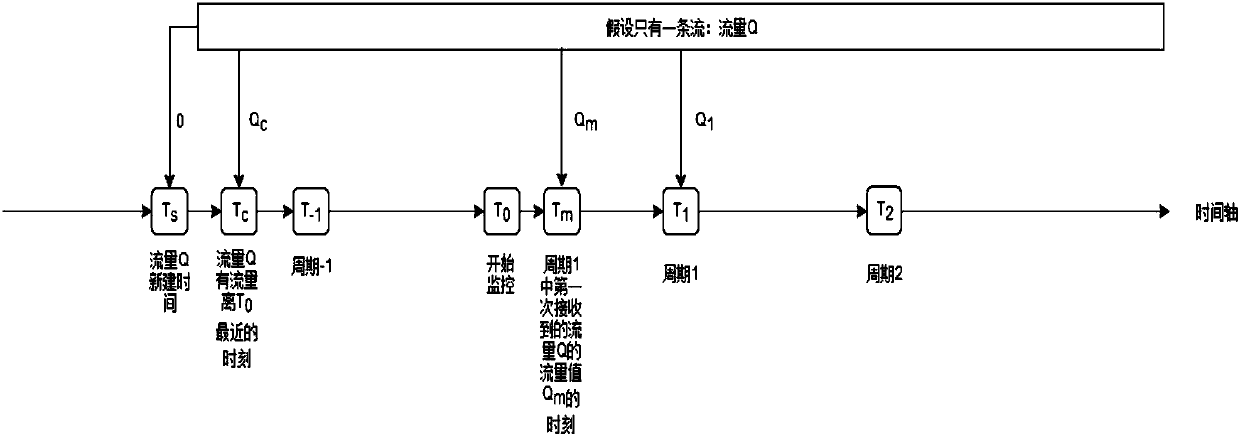
[0068] Such as figure 2 Shown:
[0069] When monitoring starts, the latest flow value of the previous cycle (5 minutes) cannot be found from the database;
[0070] Monitoring cycle 1 (T 0 ~T 1 ) are update traffic.
[0071] Brief description of the process: from T 0 Time starts, at time Tm, go to the database query (according to 5-tuple + start time query) away from T 0 Time (this moment is not within the range of the previous cycle) the latest flow value Qc; to ensure T 0 The accuracy of the flow rate within the time period ~Tm, use the following formula to calculate the flow value of this period:
[0072] Δ=(Qm-Qc) / Tm-Tc*(Tm-T 0 ).
[0073] Tm~T 1 Flow rate for time period = new value Qm.
[0074] The new value: namely Tm~T 1 The traffic value received again in .
[0075] In summary: monitoring period 1(T 0 ~T 1 ) flow = Δ + Q 1 –Qm.
Embodiment 3
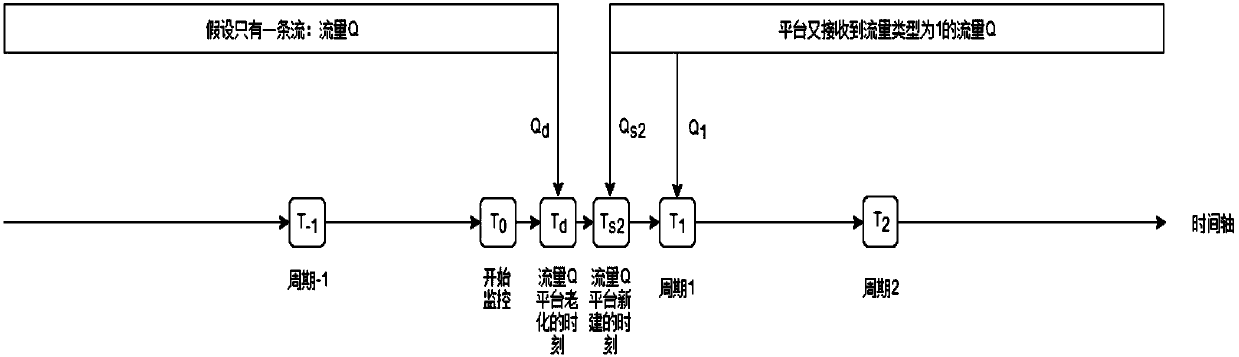
[0077] Such as image 3 Shown:
[0078] Monitoring cycle 1 (T 0 ~T 1 ), the same quintuple has both aging flow and new flow; the monitoring period T 0 ~T d flow calculation, to determine whether the latest flow value of the previous cycle (5 minutes) has been found from the database, and deal with it according to case 1 or case 2, and finally get the time period (T 0 ~T d ) flow Δ.
[0079] Brief description of the process: from T 0 Moment starts at Ts 2 time, if the traffic type is judged to be 1, then Qs 2 Indicates a new stream, then period 1(T 0 ~T 1 ) flow = Δ + Q 1 .
[0080] Device outgoing traffic:
[0081] In the session information queried with the device as the source IP, the number of all uplink bytes + in the session information queried with the device as the destination IP, the number of all downlink bytes.
[0082] Device inflow traffic:
[0083] In the session information queried with the device as the source IP, the number of all downlink bytes ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com