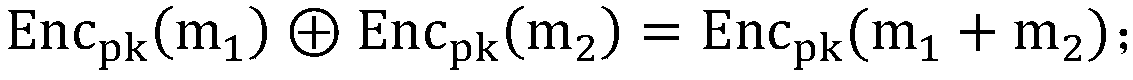RSA digital signature generation method and system based on identity
A digital signature and identity technology, applied in the field of information security, can solve problems such as key leakage and weak signature key protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] The present invention will be described in detail below in conjunction with examples. The following embodiments only show that the present invention is a possible implementation, not all possible implementations, and are not intended to limit the present invention.
[0037] One, at first set forth the method principle of the present invention.
[0038] The key generation center generates a pair of RSA public-private key pair (e, d), and a pair of random numbers satisfying part of the signing key send P 1 , send to P 2 , where H(ID) is a hash value generated based on user identity. At the same time, select and generate a set of public-private key pairs (pk, sk) of the homomorphic encryption algorithm, and send (pk, sk) to P 1 , pk sent to P 2 . Both parties involved in digital signature generation P 1 and P 2 , respectively generate a random number r 1 and r 2 . P 1 calculate first Encrypt r using homomorphic encryption method 1 get C 1 , followed by ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com