TPCM system for building and maintaining trusted operating environment and corresponding method
A credible, operating system technology, applied in the field of information security, can solve problems such as tampering replacement without security verification, non-prevention, malicious tampering, etc., to achieve high system security, reduce consumption, and improve reliability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
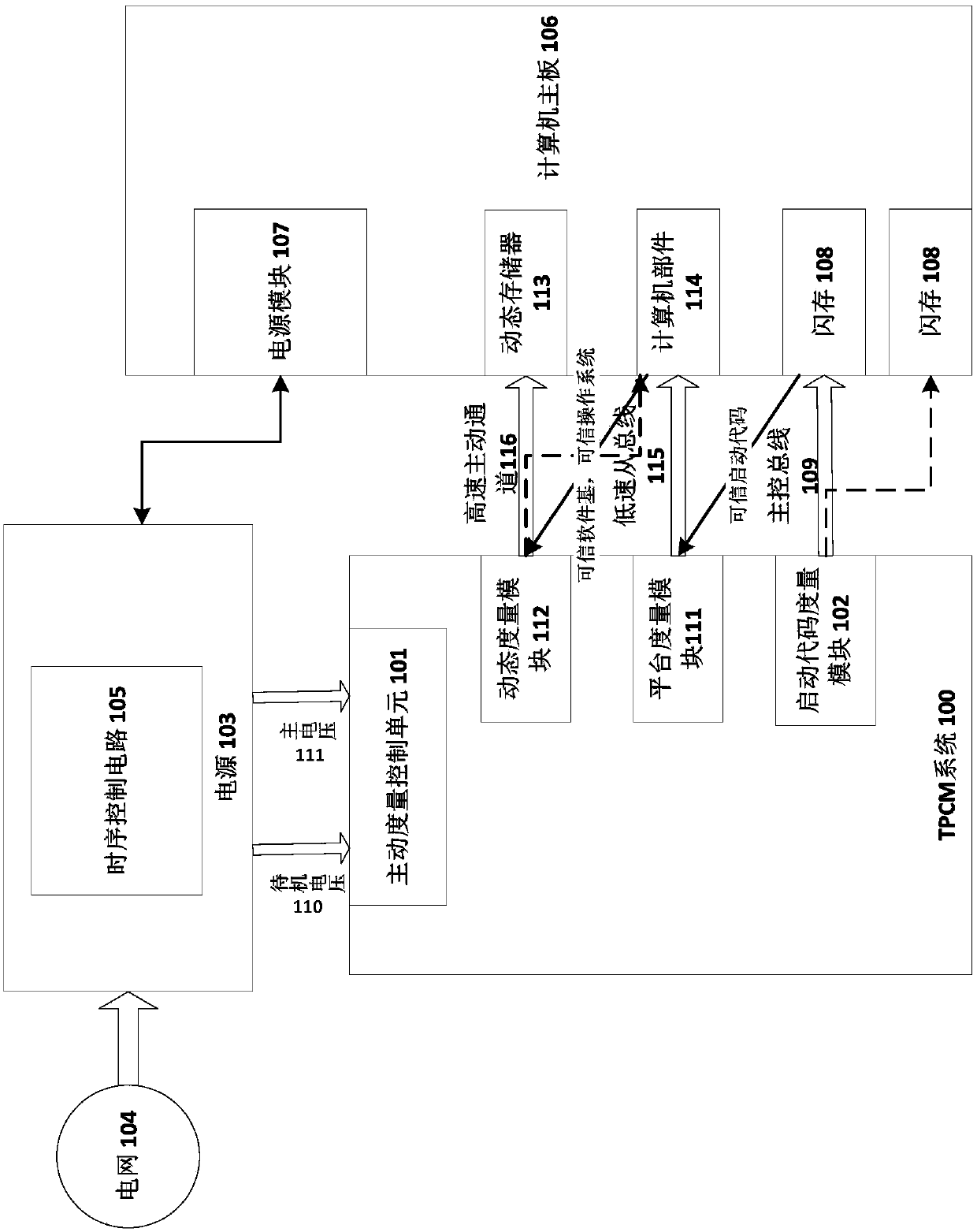
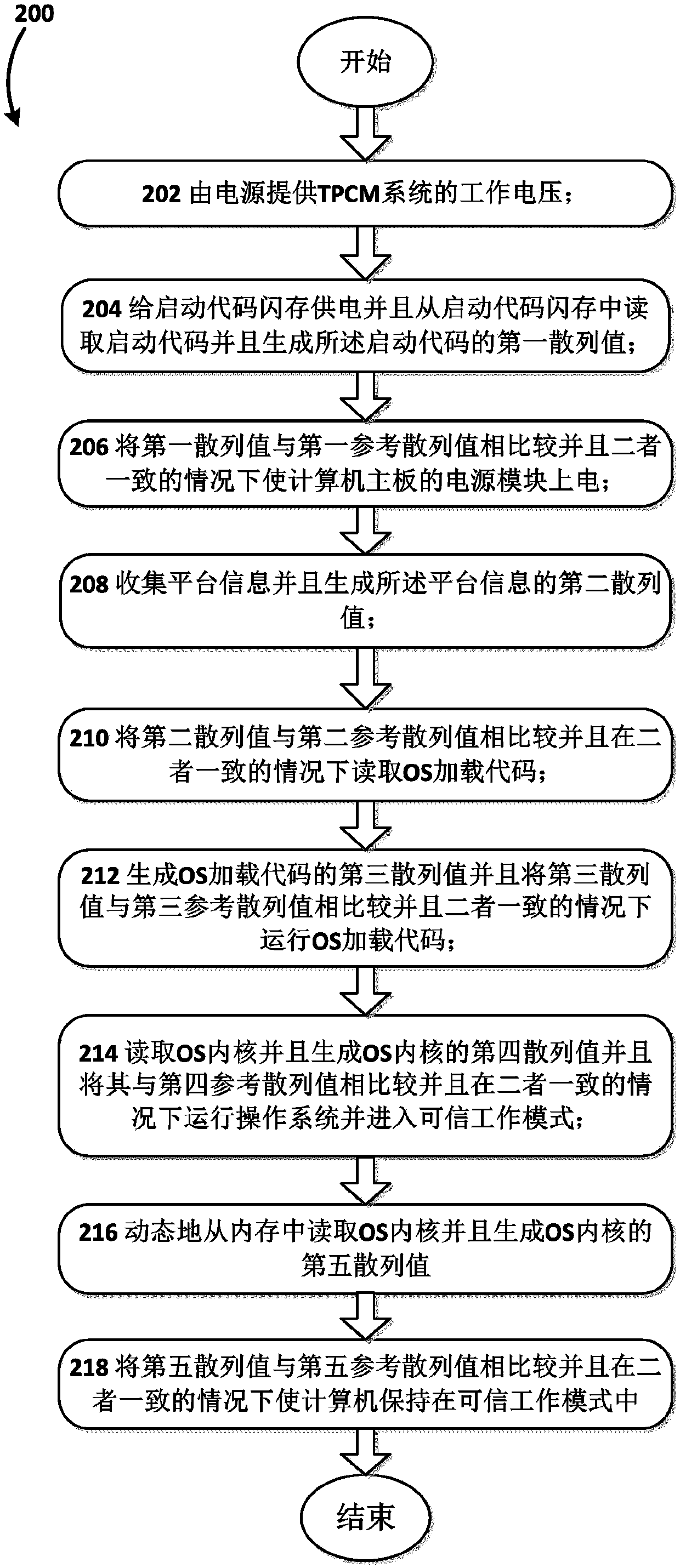
[0066] figure 1 A block diagram of the system environment of the TPCM system 100 according to the present invention is shown. figure 1 The system environment in includes grid 104 , ATX power supply 103 , computer motherboard 106 and TPCM system 100 . Here, it should be pointed out that although the embodiment of the present invention is illustrated with an x86 architecture, that is, a computer including a BIOS flash memory, the present invention is not limited thereto, but can also be applied to computers based on PowerPC architecture, ARM architecture, MIPS, etc. Computers of other architectures. It should also be noted that in this block diagram, other components have been omitted for simplicity.
[0067] The power grid 104 is used to supply power to the power supply 103, the power supply 103 is, for example, an ATX power supply, and the power grid 104 is, for example, a 220V AC power grid. It should be noted that although the system environment includes the grid here, in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com