Keystroke motion identification method based on cosine similarity
A cosine similarity, action recognition technology, applied in character and pattern recognition, instrument, digital data authentication, etc., can solve the problem of low security of digital identity
Inactive Publication Date: 2018-01-09
GUANGDONG INST OF SCI & TECH
View PDF3 Cites 0 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
[0005] Aiming at the current situation that the security of digital identity is not high but the application range is extremely wide, the present invention provides a cosine similarity-based method that uses negative selection algorithm to simulate the biological immune process and abstracts immune cells into detectors to complete non-self detection. keystroke recognition method
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment 1
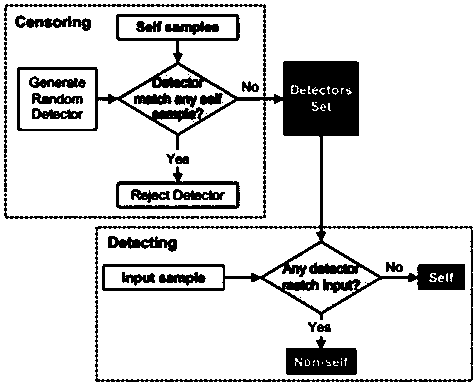
[0019] A keystroke recognition method based on cosine similarity, such as figure 1 As shown, it mainly includes the following steps:
[0020] (a) determine the dimensional space of the detection data;
[0021] (b) Determine the detector using a negative selection algorithm based on cosine similarity;
[0022] (c) Ego-space detection in the detection data space is done with the detector.
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
The invention provides a keystroke motion identification method based on cosine similarity, which relates to the field of network safety based on negative selection algorithm. Based on the keystroke dynamics, the biological immunization process can be simulated by means of the negative selection algorithm. Through the abstractness of immune cells, non-self detection can be completed by the detector, and the aim of distinguishing truth from falsehood can be achieved. The invention is advantageous in that the keystroke dynamics is applied, and with multiple attributes, the bottleneck of the negative selection algorithm in a high-dimensional space can be broken through; the high-dimensional negative selection algorithm has great advantage in the self recognition and non-self recognition in the complicated compound application scene.
Description
technical field [0001] The invention relates to the field of network security based on a negative selection algorithm, in particular to a keystroke recognition method based on cosine similarity. Background technique [0002] It is clear that digital identities represent an important advancement in our society. However, the dissemination of these identities has resulted in increased data exposure and identity theft. , identity theft occurs when a person uses another person's personal information to illegally pretend to be that person. Another promising approach for curbing this problem is to use behavioral intrusion detection systems, which detect anomalous behavior as potential intrusions. [0003] Among the aspects in which a user may be analyzed, keystroke dynamics are studied. This work demonstrates that an immune negative selection algorithm (NSAS) is applied to identify users based on their typing rhythm. These algorithms are novelty detectors that use only positive...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More IPC IPC(8): G06K9/00G06K9/62G06F21/32
Inventor 杨忠明张彬常亚萍李威
Owner GUANGDONG INST OF SCI & TECH
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Patsnap Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com