Sign-in data based user behavior trajectory clustering method
A trajectory clustering and user technology, applied in data processing applications, special data processing applications, geographic information databases, etc., can solve problems such as no users, data sparsity, and large differences in check-in times.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
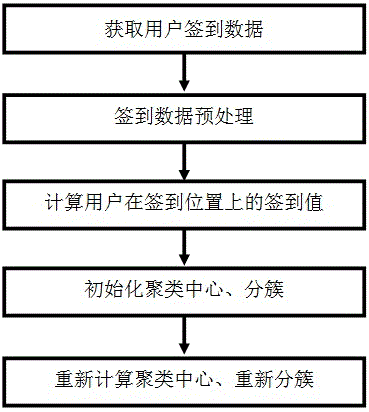
[0023] The present invention will be described in detail below in conjunction with the accompanying drawings.
[0024] as attached figure 1 Shown, the inventive method carries out according to the following steps:
[0025] Step 1: Obtain user check-in data, including user ID, check-in location, check-in time, and check-in date;
[0026] Location-based mobile social networks (LBSN) such as Sina Weibo, Jiepang, Renren, Foursquare, and Gowalla have developed rapidly in recent years. A large number of users use these services to record spatio-temporal behavior trajectories in the form of check-in. Therefore, they can provide API to capture the required user sign-in data.
[0027] Step 2: Preprocessing the user check-in data, including filtering useless data, converting types and unifying formats;
[0028] The analysis shows that the invalid users in the location data (that is, users who rarely check in after registration, such as users with less than 5 check-ins) and location P...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com