Abnormal equipment identification method and apparatus
A device identification and abnormal technology, applied in the field of network security, can solve the problems of server bandwidth and computing resources being full, normal users providing services, and the server can no longer provide services, to achieve the effect of avoiding network attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
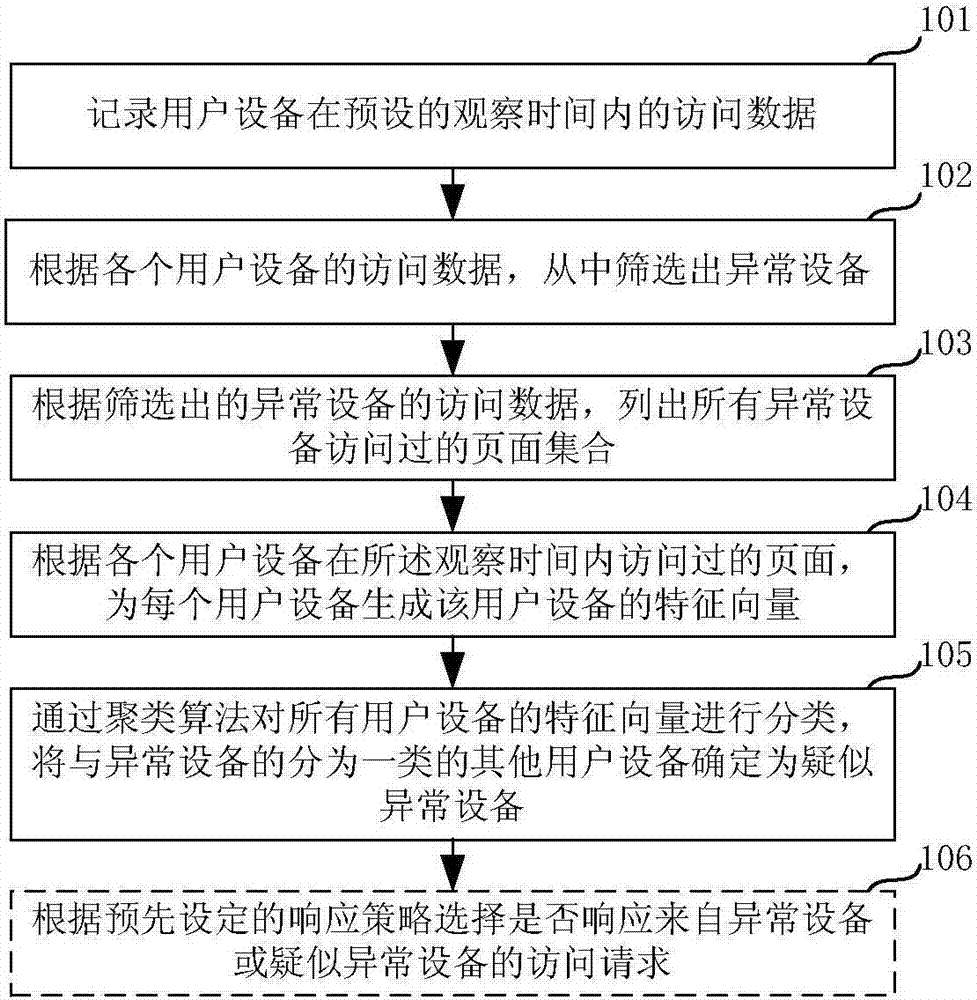
[0044] The embodiment of the present invention proposes an abnormal device identification method, which can find suspected abnormal devices according to the access data of known abnormal devices, and then can identify abnormal devices more quickly and accurately, and realize fast and accurate network attack interception .
[0045] figure 1 The flow of the method for identifying abnormal equipment described in the embodiment of the present invention is shown. Such as figure 1 As shown, the method mainly includes:
[0046] Step 101, recording the access data of the user equipment within a preset observation time.
[0047] It should be noted that, in each step of the embodiment of the present invention, each user equipment can be identified by its IP (Internet Protocol) address. For example, in this step, when recording the access data of each user equipment within the preset observation time, the access data within the preset observation time may be recorded corresponding to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com