Network attack detection method and device, terminal equipment and computer storage medium
A network attack and detection method technology, applied in the field of network security, can solve problems such as low analysis efficiency, high maintenance cost, and difficulty in having unknown attack detection capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
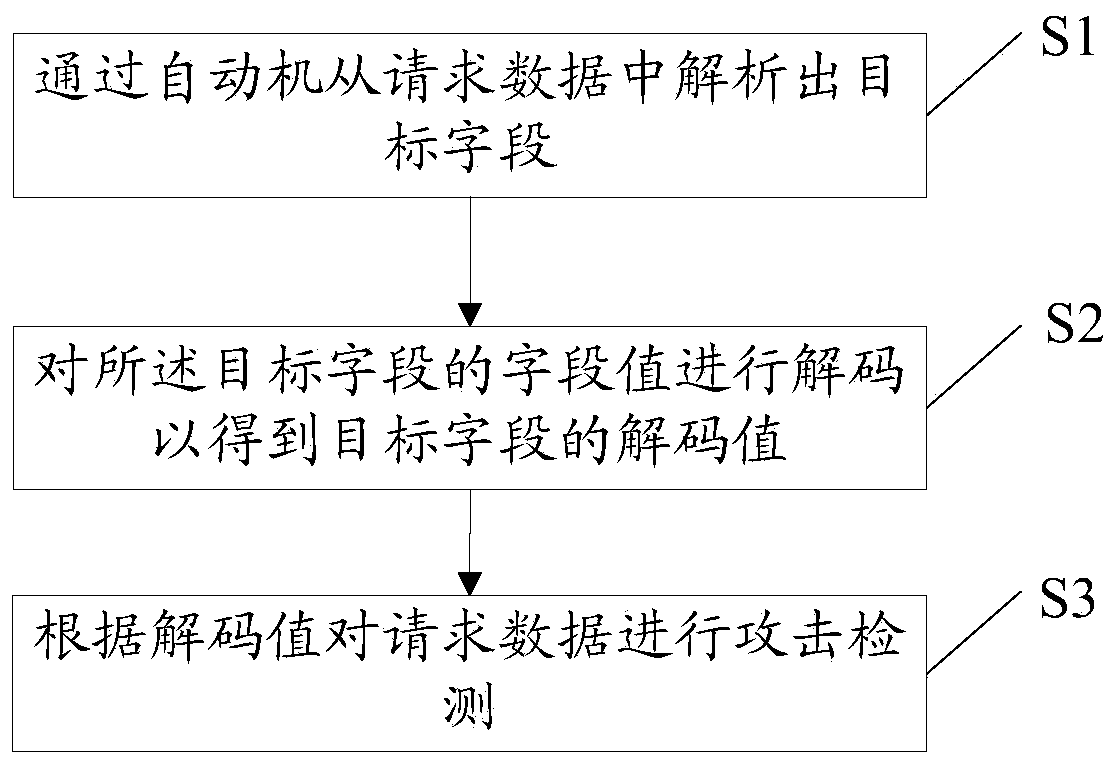
[0084] figure 1 It is a flow chart of the method for detecting a network attack according to Embodiment 1 of the method of the present invention. see figure 1 , in this embodiment, the method includes:
[0085] S1: Parse the target field from the request data by automaton.
[0086] S2: Decode the field value of the target field to obtain the decoded value of the target field.
[0087] S3: Perform attack detection on the request data according to the decoded value.
[0088] Field value refers to the value of a field in the request data. For example, "GET" is the field value of the method field in the request data.
[0089] The decoded value refers to the decoded result obtained after decoding a certain field value in the request data.
[0090] Wherein, the automaton is used for parsing request data (such as HTTP request), scanning the entire request data in a linear time, and analyzing each component of the request data for subsequent detection process.
[0091] Taking t...
Embodiment approach 2
[0095] The method provided in this embodiment includes all the content in method embodiment 1, and details are not repeated here. Wherein, the direct carrier of the target field may be request data or a field value in the request data.
[0096] If the direct carrier of the target field is the request data, the processing S1 is realized in the following way:
[0097] The target field is parsed directly from the request data by the first automaton.
[0098] Correspondingly, in the method provided in this embodiment, the first automaton is constructed based on the communication standard corresponding to the request data.
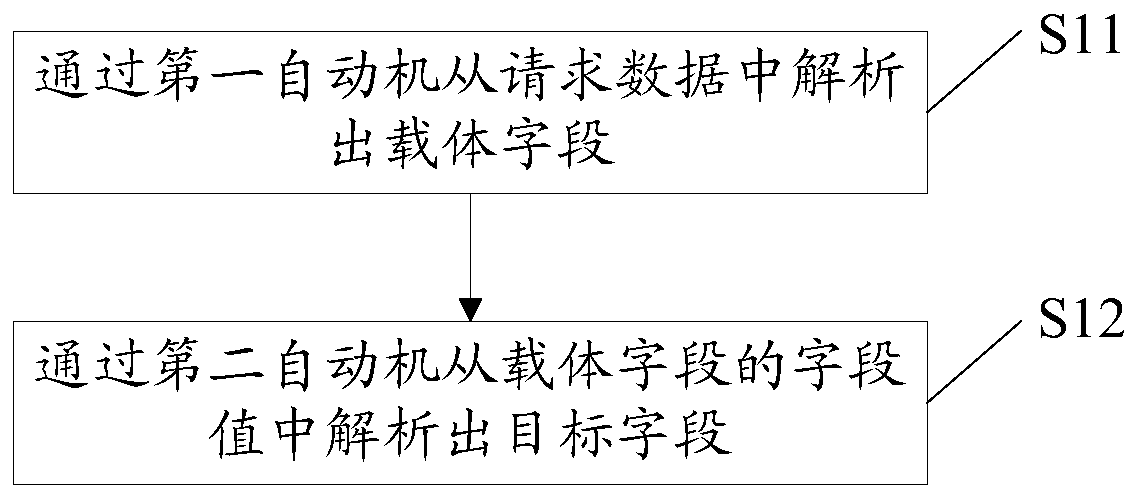
[0099] Such as image 3 As shown, if the direct carrier of the target field is the field value in the request data, the processing S1 is realized in the following way:
[0100] S11: Parsing out the carrier field (the request data field including the target field) from the request data by the first automaton.
[0101] S12: Using the second automaton to parse...
Embodiment approach 3
[0107] The method provided in this embodiment includes all the content in the method embodiment 2, which will not be repeated here. Such as Figure 4 As shown, in this embodiment, S12 includes the following processing:
[0108] S121: Determine the suspected content type of the request body field (possible content type of the request body field).
[0109] S122: Select a second automaton according to the suspected content type.
[0110] S123: Using the selected second automaton to parse out the target field from the field value of the request body field.
[0111] Because the present invention analyzes the possible content types of the request body, and executes parsing processing corresponding to the analyzed content types, it can effectively prevent attackers from using the protocol to bypass attack detection.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com