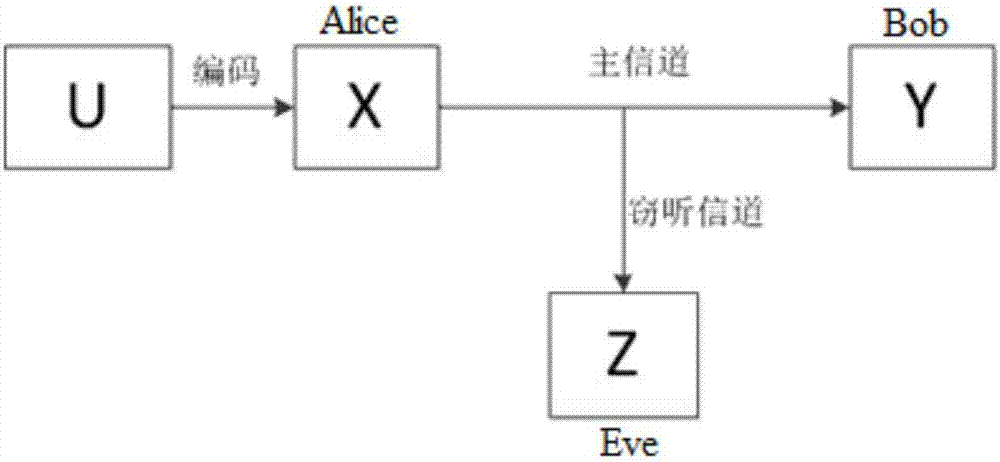
AWGN-wiretap channel anti-wiretapping security structure based on polar code and implementation method thereof
A security structure and implementation method technology, applied in the field of communication, can solve problems such as ciphertext decryption failure, physical layer bit error rate cannot be ignored, etc., and achieve simple composition, increased decoding error rate, and flexible and adjustable secure transmission rate Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
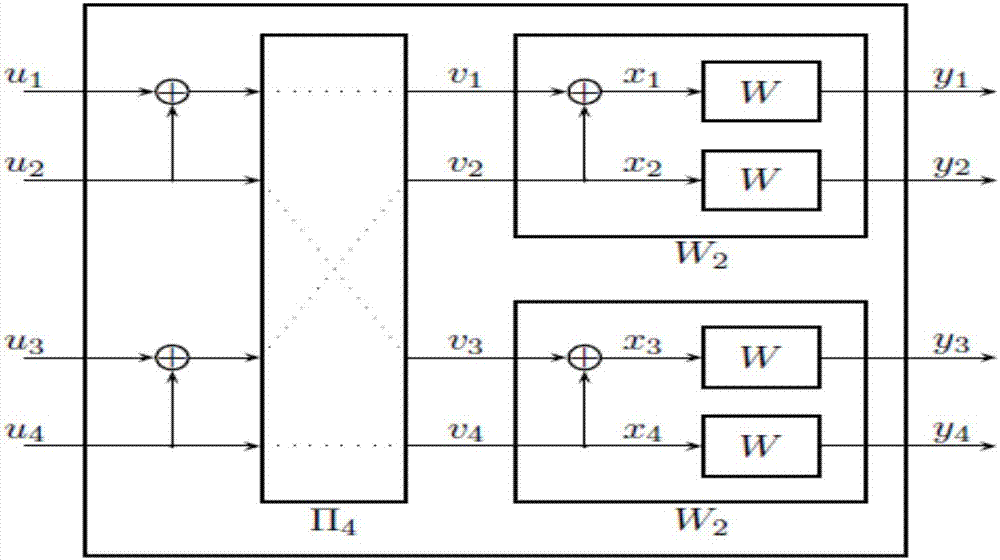
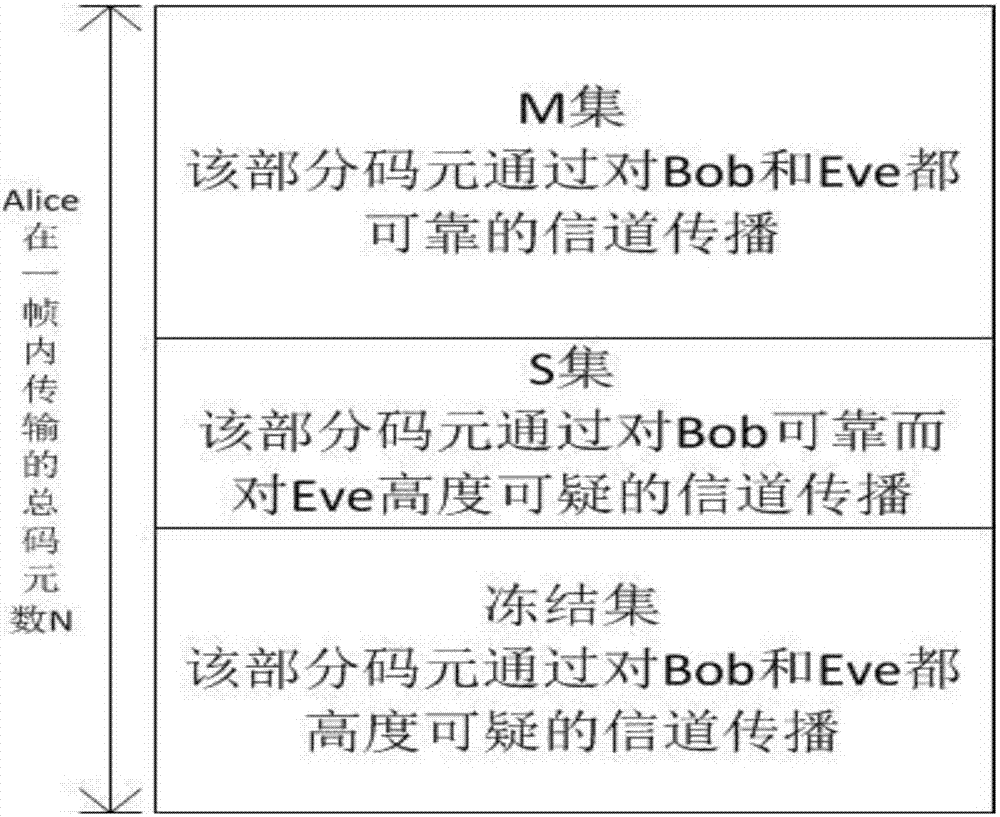
[0095] This example illustrates the obfuscation / de-obfuscation method for polar coded signals under AWGN-wiretap channel. In this example, the Polar code used has a code length of 2048, and the total length of transmission symbols is 10000 frames. The signal-to-noise ratio of the legal main channel is fixed at 5dB, and Bob’s anchor bit error rate is set to P gap (Bob) is 1e-5, the required polar code transmission code rate is 0.11, and Alice estimates that the signal-to-noise ratio of the eavesdropper is more than 1dB lower than that of the legitimate channel, then Alice sets the channel ratio of Eve to 4dB. According to the Gaussian density evolution calculation, it can be obtained that at Bob=5dB, Eve 估 M-set and S-set when =4dB.
[0096] Then the concrete steps of applying the inventive method are as follows:
[0097] Step 1: Complement the symbols of the M set to the S set to make its length 112, which is recorded as the S' set. Select 112 symbols from the other symbol...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com