Cross-device login method, system and device
A login method and cross-device technology, applied in the field of communications, which can solve problems such as secondary user intervention
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
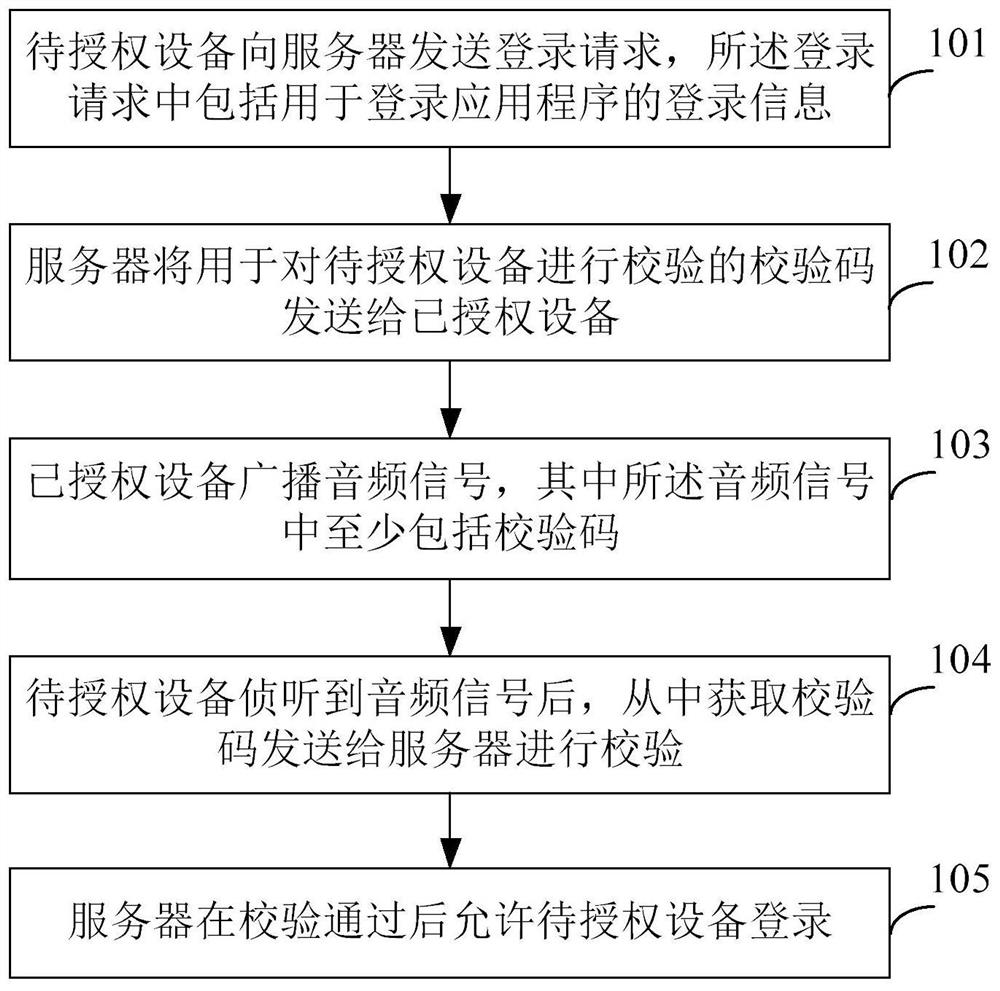
[0053] figure 1 It is a schematic flowchart of a cross-device login method according to Embodiment 1 of the present invention. Such as figure 1 As shown, the cross-device login method includes the following steps:
[0054] S101. The device to be authorized sends a login request to a server, where the login request includes login information for logging into an application program.
[0055] When a user tries to log in to an application program on a device to be authorized, a login request needs to be sent to the server corresponding to the application program through the device to be authorized, so as to request the server to allow the device to be authorized to log in to the application program, so that the device to be authorized The device has permission to use the application. Wherein, the login request at least includes login information for logging into the application program. Wherein, the login information is preferably a login account. In practical applications, g...
Embodiment 2
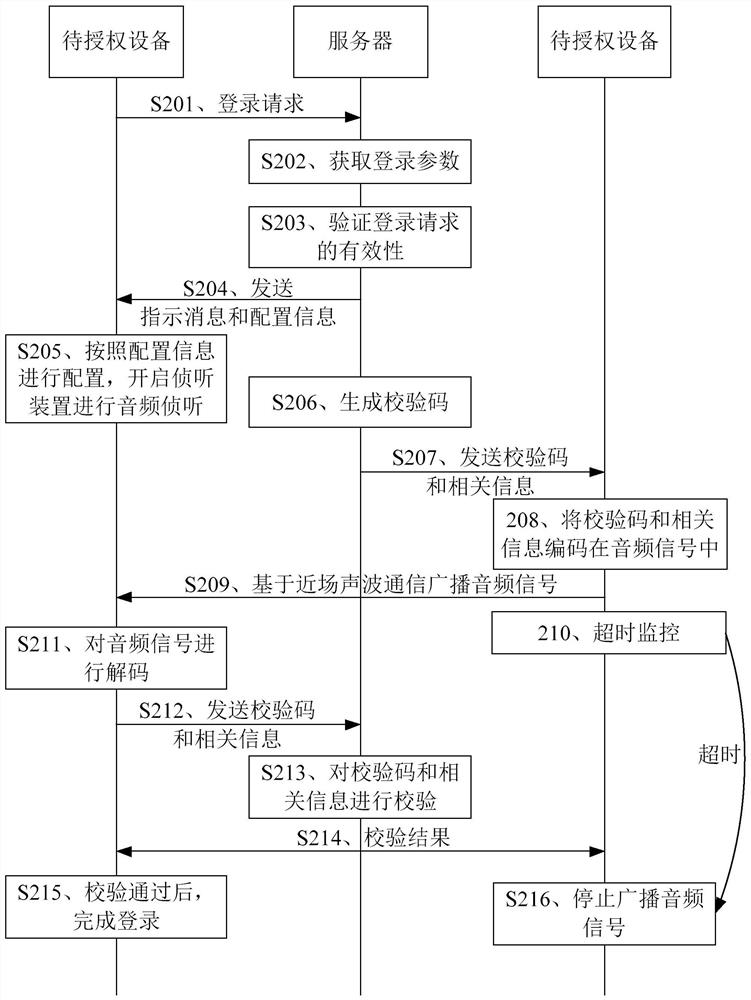
[0074] figure 2 It is a schematic flowchart of the cross-device login method provided by Embodiment 2 of the present invention. Such as figure 2 As shown, the cross-device login method includes the following steps:
[0075] S201. The device to be authorized sends a login request to the server.
[0076] For the specific process, please refer to the introduction of related content in the above embodiments, and details will not be repeated here.
[0077] S202. The server processes the login request to obtain login parameters therefrom.
[0078] The server may parse the login request to obtain the login parameters carried in the login request. The login parameters may include login account number and login time.
[0079] S203. The server verifies the validity of the login request according to the login parameters.
[0080] The server can determine whether the login account and the login time are valid, and if the login account is a valid account, it means that the login ac...
Embodiment 3
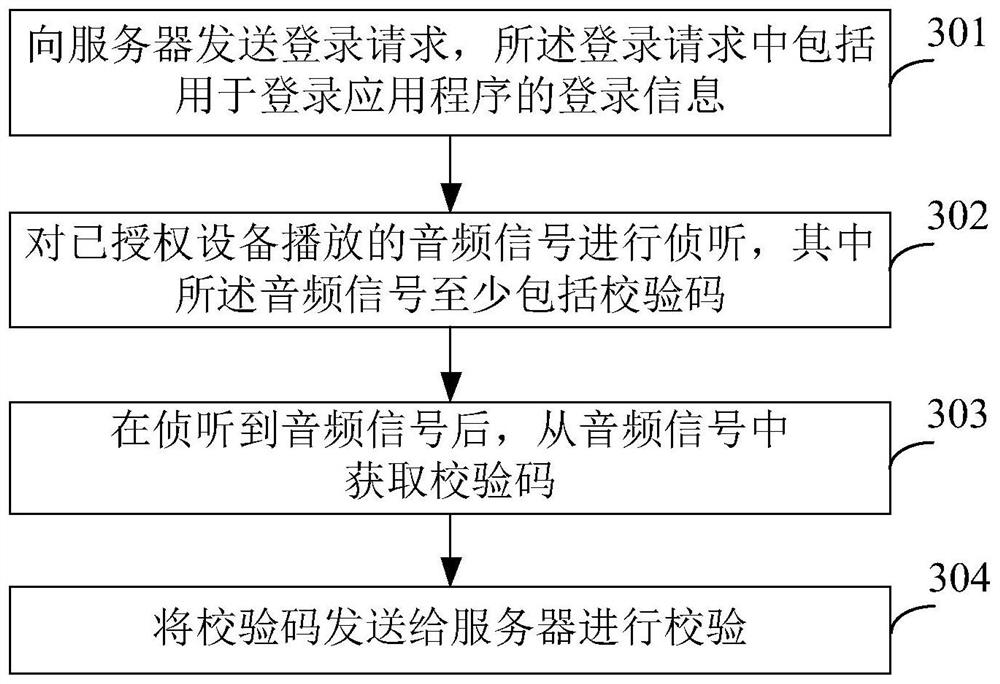
[0114] image 3 It is a schematic flowchart of a cross-device login method according to Embodiment 3 of the present invention. Such as image 3 As shown, the cross-device login method includes the following steps:
[0115] S301. Send a login request to a server, where the login request includes login information for logging into an application program.
[0116] In this embodiment, the execution subject of the cross-device login method is the device to be authorized. When a user tries to log in to an application program on a device to be authorized, the device to be authorized sends a login request to the server corresponding to the application program, requesting that the server allow the device to be authorized to log in to the application program, so that the device to be authorized has Permissions to use this application. Wherein, the login request at least includes a login account. Optionally, the login request may also include information such as the device identifie...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap